Which type of system is a user entity behavior analysis (UEBA) tool?
Which of the following is an AWS serverless service?
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
Which key component is used to configure a static route?
What is a function of SSL/TLS decryption?
A doctor receives an email about her upcoming holiday in France. When she clicks the URL website link in the email, the connection is blocked by her office firewall because it's a known malware website. Which type of attack includes a link to a malware website in an email?
Which element of the security operations process is concerned with using external functions to help achieve goals?
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?
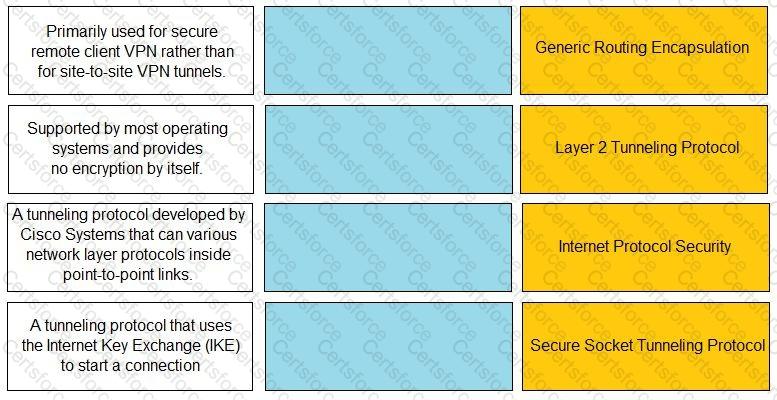
Match the description with the VPN technology.
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?