Which situation is recorded as a system log?
When is the content inspection performed in the packet flow process?
Which feature enables an administrator to review the Security policy rule base for unused rules?
Which license is required to use the Palo Alto Networks built-in IP address EDLs?
Which rule type is appropriate for matching traffic both within and between the source and destination zones?
What are two valid selections within an Anti-Spyware profile? (Choose two.)
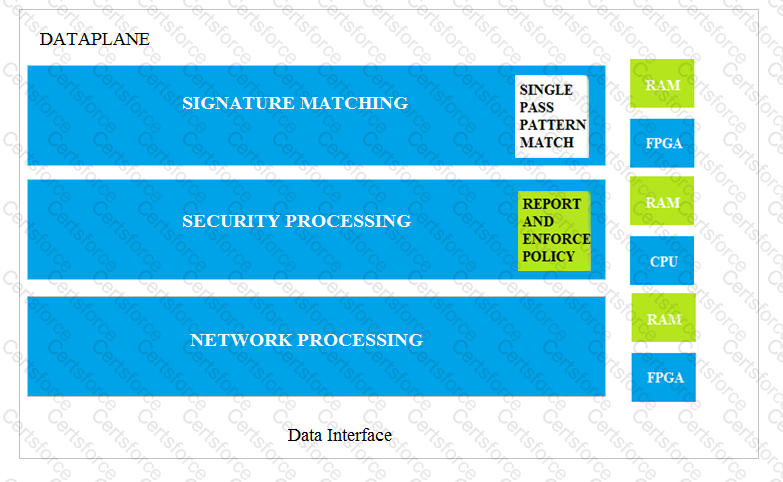
Which data-plane processor layer of the graphic shown provides uniform matching for spyware and vulnerability exploits on a Palo Alto Networks Firewall?
Which dynamic update type includes updated anti-spyware signatures?
In which two Security Profiles can an action equal to the block IP feature be configured? (Choose two.)
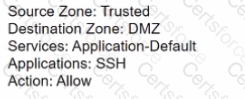
If users from the Trusted zone need to allow traffic to an SFTP server in the DMZ zone, how should a Security policy with App-ID be configured?
A)

B)

C)

D)