Which security profile should be used to classify malicious web content?
What is the maximum volume of concurrent administrative account sessions?
Which DNS Query action is recommended for traffic that is allowed by Security policy and matches Palo Alto Networks Content DNS Signatures?
Which table for NAT and NPTv6 (IPv6-to-IPv6 Network Prefix Translation) settings is available only on Panorama?
Which action should be taken to identify threats that have been detected by using inline cloud analysis?
Which plane on a Palo alto networks firewall provides configuration logging and reporting functions on a separate processor?
Match each feature to the DoS Protection Policy or the DoS Protection Profile.
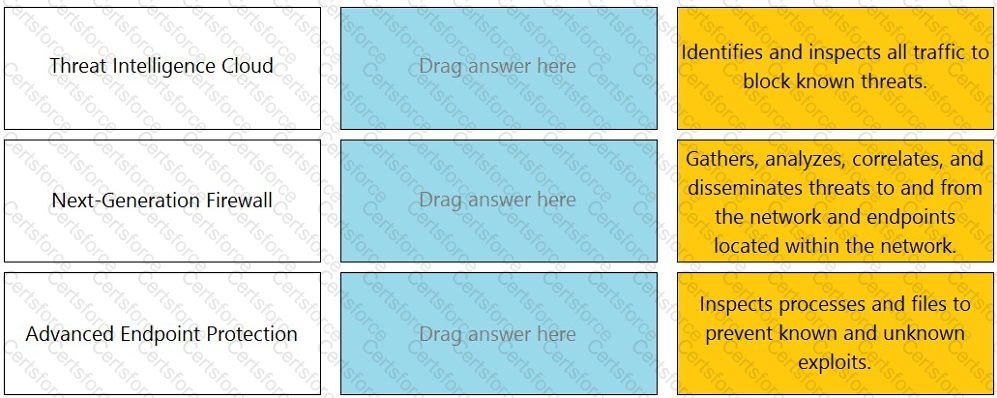
Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic deployed as internet gateways?
Which Security profile would you apply to identify infected hosts on the protected network uwall user database?
An internal host wants to connect to servers of the internet through using source NAT.
Which policy is required to enable source NAT on the firewall?