An administrator is reviewing another administrator s Security policy log settings
Which log setting configuration is consistent with best practices tor normal traffic?
Which security profile will provide the best protection against ICMP floods, based on individual combinations of a packet`s source and destination IP address?
The compliance officer requests that all evasive applications need to be blocked on all perimeter firewalls out to the internet The firewall is configured with two zones;
1. trust for internal networks
2. untrust to the internet
Based on the capabilities of the Palo Alto Networks NGFW, what are two ways to configure a security policy using App-ID to comply with this request? (Choose two )
Identify the correct order to configure the PAN-OS integrated USER-ID agent.
3. add the service account to monitor the server(s)
2. define the address of the servers to be monitored on the firewall
4. commit the configuration, and verify agent connection status
1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent
Which solution is a viable option to capture user identification when Active Directory is not in use?
Which three Ethernet interface types are configurable on the Palo Alto Networks firewall? (Choose three.)
An administrator would like to use App-ID's deny action for an application and would like that action updated with dynamic updates as new content becomes available.
Which security policy action causes this?
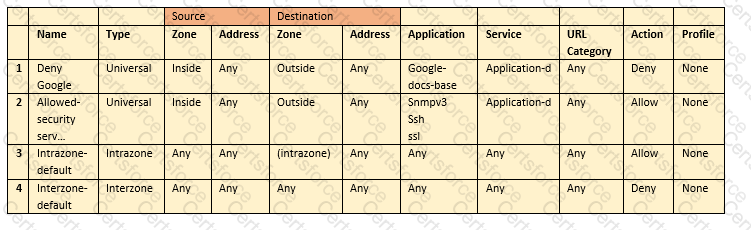
Based on the security policy rules shown, ssh will be allowed on which port?
What action will inform end users when their access to Internet content is being restricted?
An administrator wants to prevent access to media content websites that are risky
Which two URL categories should be combined in a custom URL category to accomplish this goal? (Choose two)