Which three interface deployment methods can be used to block traffic flowing through the Palo Alto Networks firewall? (Choose three.)
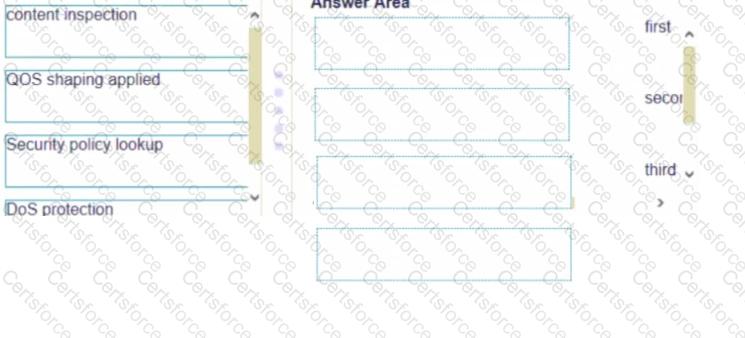
Place the following steps in the packet processing order of operations from first to last.
Within an Anti-Spyware security profile, which tab is used to enable machine learning based engines?
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?
What do dynamic user groups you to do?
An organization has some applications that are restricted for access by the Human Resources Department only, and other applications that are available for any known user in the organization.
What object is best suited for this configuration?
How would a Security policy need to be written to allow outbound traffic using Secure Shell (SSH) to destination ports tcp/22 and tcp/4422?
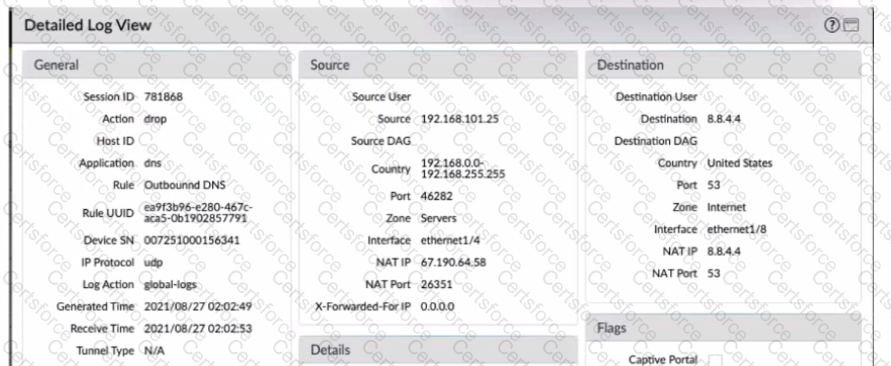
Given the detailed log information above, what was the result of the firewall traffic inspection?
An administrator should filter NGFW traffic logs by which attribute column to determine if the entry is for the start or end of the session?
Which Security profile must be added to Security policies to enable DNS Signatures to be checked?