Which data flow direction is protected in a zero trust firewall deployment that is not protected in a perimeter-only firewall deployment?
What are three valid source or D=destination conditions available as Security policy qualifiers? (Choose three.)
An administrator would like to block access to a web server, while also preserving resources and minimizing half-open sockets. What are two security policy actions the administrator can select? (Choose two.)
Which two security profile types can be attached to a security policy? (Choose two.)
An administrator would like to see the traffic that matches the interzone-default rule in the traffic logs.
What is the correct process to enable this logging1?
Your company occupies one floor in a single building you have two active directory domain controllers on a single networks the firewall s management plane is only slightly utilized.
Which user-ID agent sufficient in your network?
Which security policy rule would be needed to match traffic that passes between the Outside zone and Inside zone, but does not match traffic that passes within the zones?
A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall?
Starting with PAN-OS version 9.1, application dependency information is now reported in which two locations? (Choose two.)
Review the Screenshot:
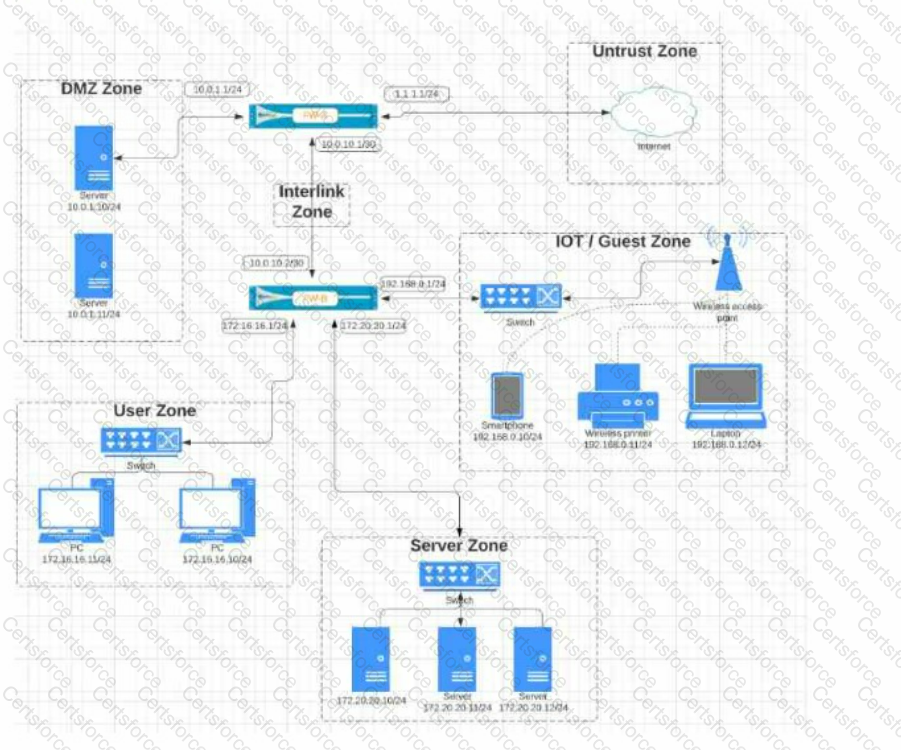
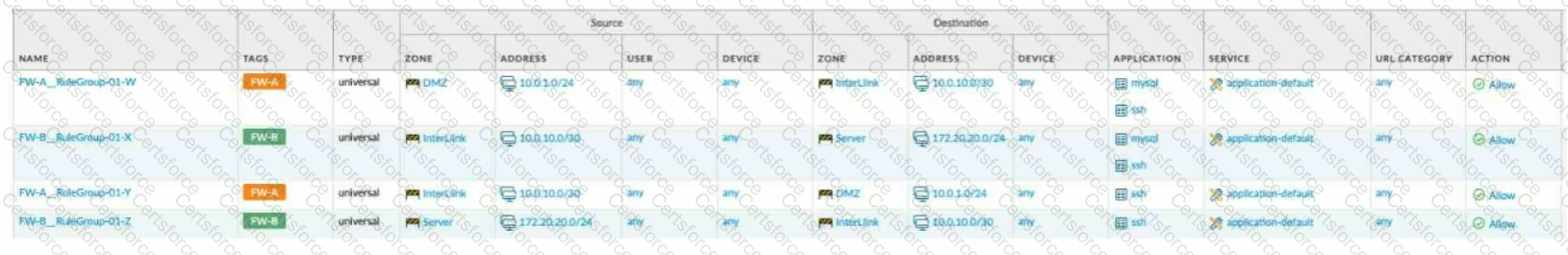
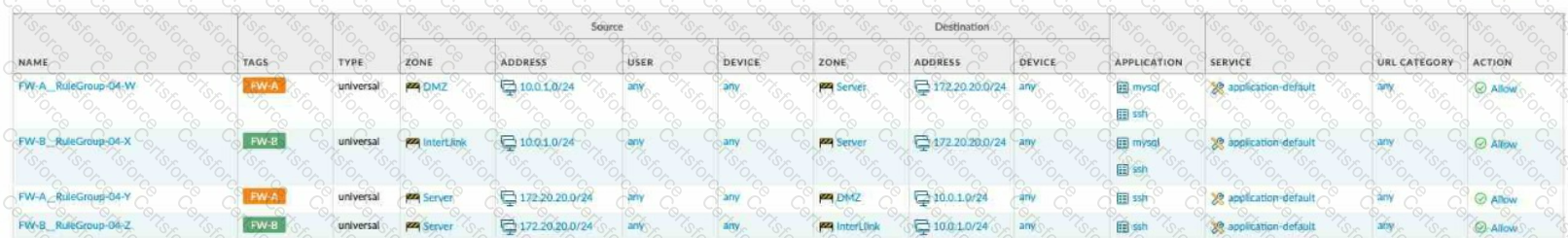
Given the network diagram, traffic must be permitted for SSH and MYSQL from the DMZ to the SERVER zones, crossing two firewalls. In addition, traffic should be permitted from the
SERVER zone to the DMZ on SSH only.
Which rule group enables the required traffic?
A)
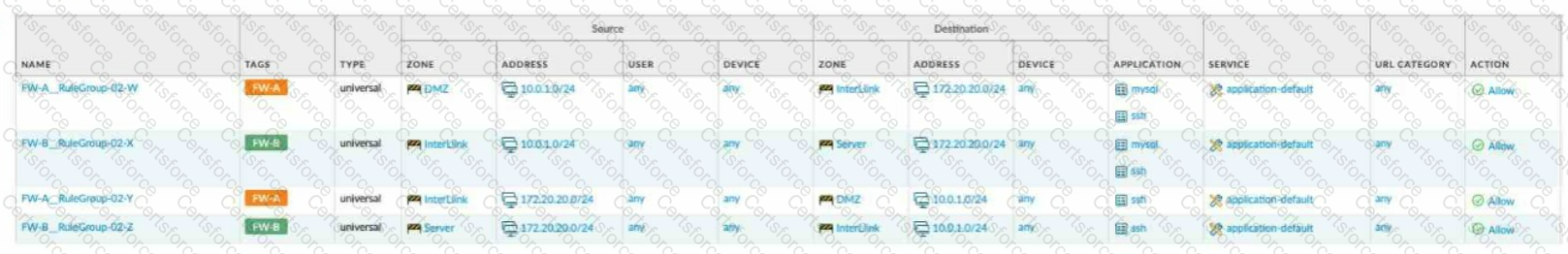
B)
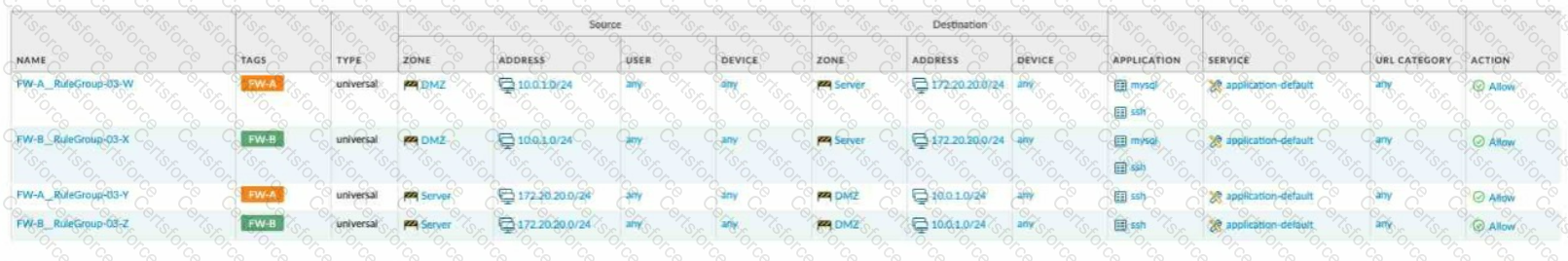
C)
D)