A consultant creates three storage containers (container-1, container-2, container-3). The customer requires that only container-1, which will be utilized as an NFS datastore, be presented to external hosts.
However, users are able to mount all three containers.
What is causing this problem?
Refer to the exhibit.

The customer has an existing NX-3160 block and is adding a second node into it.
Where should the node be installed?"
During the knowledge transfer session, a consultant conducts a storage management demo. In the Creating a Storage Container workflow, the customer notices the Reserved Capacity parameter and asks for best practices related to it.
How should the consultant respond?
When utilizing the Nutanix cluster As Built Document generator, which two configuration elements should a consultant provide when running the run_as_built.exe command? (Choose two.)
After a consultant runs a bare metal Foundation, the imaging process fails.
In which two locations can the consultant find the logs? (Choose two.)
Refer to the exhibit.
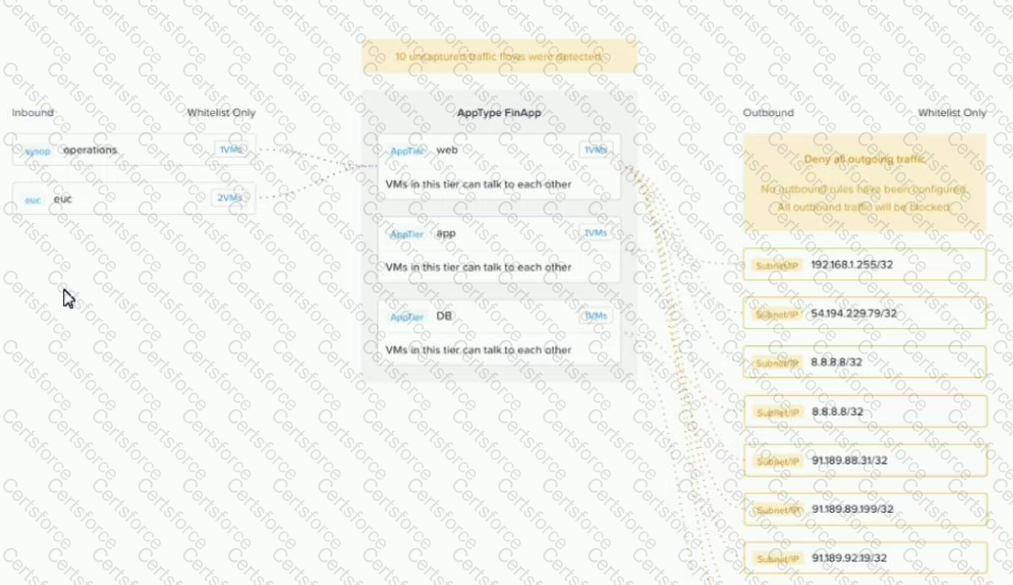
An administrator creates a security policy that isolates their financial application from accessing the Internet When viewing the policy in Prism Central, several connections from the application are outbound to the Internet.
What is causing this issue with the policy?
The networking team makes changes to the Top of Rack switches to which the Nutanix cluster are attached. A few VMs are able to communicate with each other on the same node but are unable to connect to other parts of the network.
What is the likely cause of this issue?
A consultant is unable to ping the CVM from the hypervisor using the external interface. The customer's network is configured with the 10.3.12.0/24 subnet without VLAN tagging. The CVM and hypervisor are using the same address space.
What is causing this issue?
An administrator needs to evaluate if the existing configuration of Protection Domains meets the specified corporate recovery policy for SQL Data. The corporate policy requires that all SQL Servers be recoverable at the DR site within 30 minutes, and must result in a maximum of 60 minutes of data loss. SQL data must be required.
The protection domain is configured as follows:
• Application consistent snapshots are enabled
• The SQL server VMs are assigned to the Protection Domain as their own Consistency Group
• The Protection Domain schedule is configured as snapshots taken every 90 minutes from 7 am until 8 pm
What must be changed to meet the required policy?
During Foundation, all nodes are imaged successfully. The cluster creation step fails. The consultant troubleshoots the issue and verifies that all Hosts and CVMs are up and running and responding to network pings.
Which method should the consultant select to create the cluster?