Refer to the exhibits.
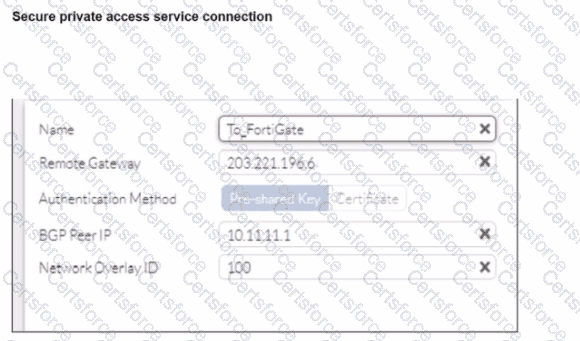

A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub. The VPN tunnel does not establish
Based on the provided configuration, what configuration needs to be modified to bring the tunnel up?
What are two advantages of using zero-trust tags? (Choose two.)
Refer to the exhibit.
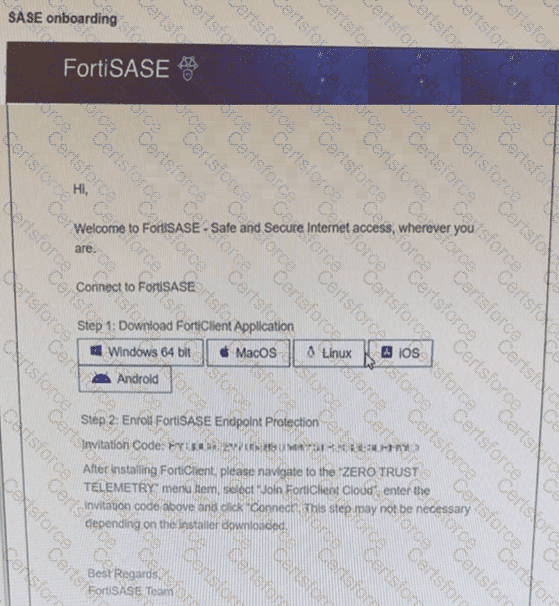
Which two statements about the onboarding process shown in the exhibit are true? (Choose two answers)
An organization needs to resolve internal hostnames using its internal rather than public DNS servers for remotely connected endpoints. Which two components must be configured on FortiSASE to achieve this? (Choose two.)
How does FortiSASE Secure Private Access (SPA) facilitate connectivity to private resources in a hub-and-spoke network? (Choose one answer)
Refer to the exhibits.
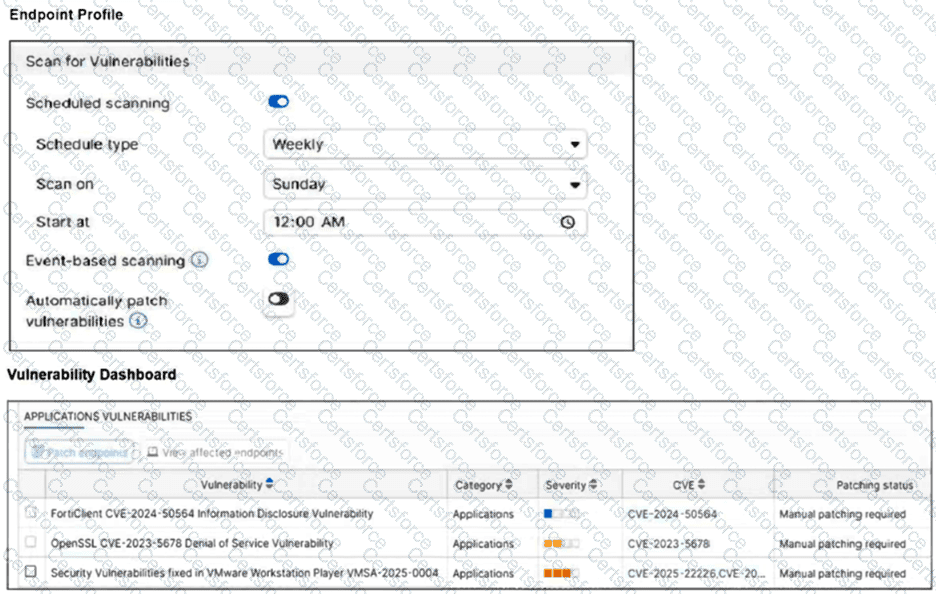
How will the application vulnerabilities be patched, based on the exhibits provided? (Choose one answer)
Refer to the exhibit.
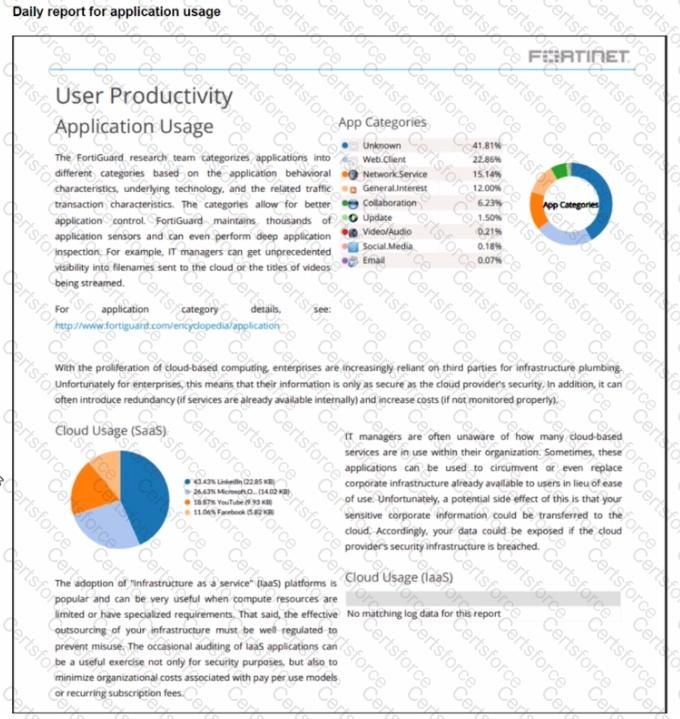
The daily report for application usage shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
Refer to the exhibit.
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters. Which configuration change must the administrator make to get proper user information?
What are two benefits of deploying secure private access (SPA) with SD-WAN? (Choose two answers)
A FortiSASE administrator is receiving reports that some users have travelled overseas and cannot establish their agent-based VPN tunnels, although they can authenticate with their SSO credentials to access O365 and SFDC directly. The administrator reviewed the firewall policies and ZTNA tags of some users and could not find anything unusual. Which action can the administrator take to resolve this problem? (Choose one answer)