Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)
Which policy type is used to control traffic between the FortiClient endpoint to FortiSASE for secure internet access?
Which FortiSASE feature ensures least-privileged user access to all applications?
Which two additional components does FortiSASE use for application control to act as an inline-CASB? (Choose two.)
Refer to the exhibit.
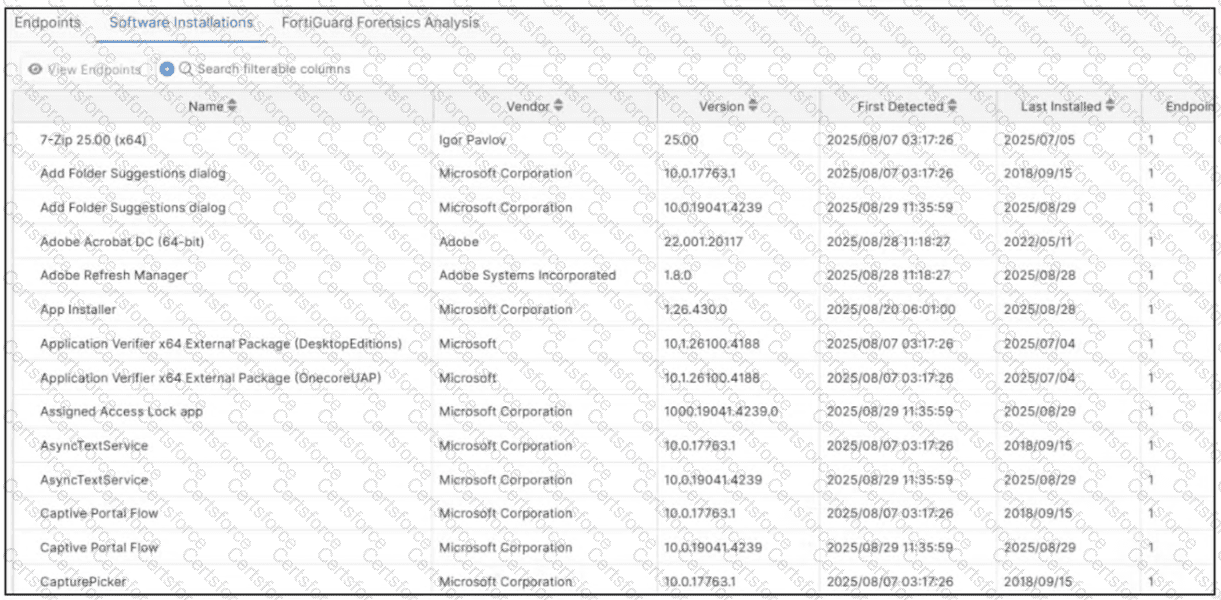
Which type of information or actions are available to a FortiSASE administrator from the following output? (Choose one answer)
Which statement about FortiSASE and SAML is true? (Choose one answer)
Refer to the exhibit.
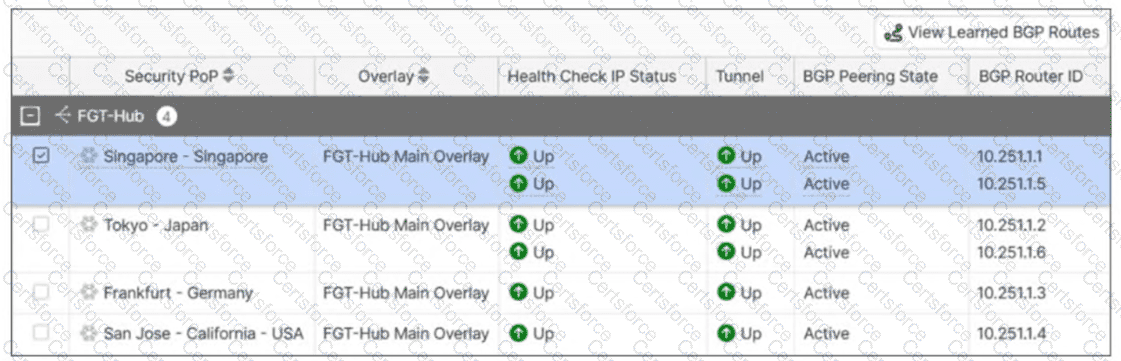
An SPA service connection is experiencing connectivity problems. Which configuration setting should the administrator verify and correct first? (Choose one answer)
An administrator must restrict endpoints from certain countries from connecting to FortiSASE. Which configuration can achieve this? (Choose one answer)
What are the two key features and benefits of Fortinet SOCaaS when integrated with FortiSASE? (Choose two answers)
When configuring the DLP rule in FortiSASE using Regex format, what would be the correct order for the configuration steps? (Place the four correct steps in order)
