A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
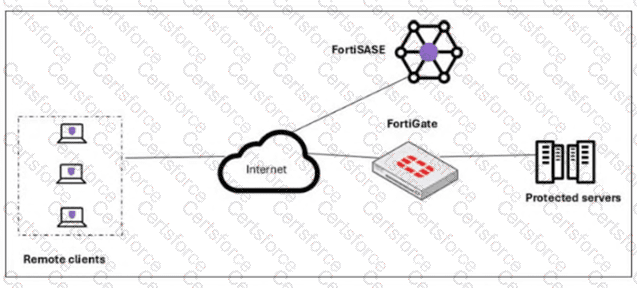
In this scenario, which two setups will achieve these requirements? (Choose two answers)
Refer to the exhibits.
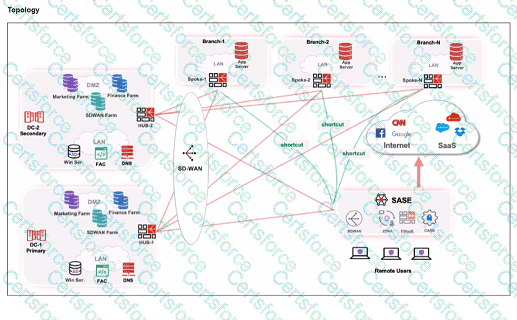
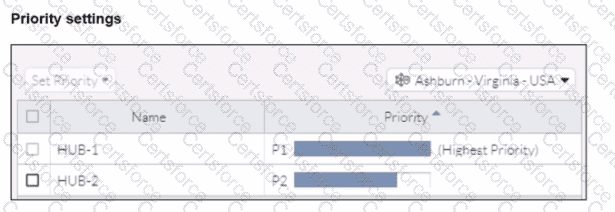
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
You are designing a new network, and the cybersecurity policy mandates that all remote users working from home must always be connected and protected. Which FortiSASE component facilitates this always-on security measure? (Choose one answer)
What happens to the logs on FortiSASE that are older than the configured log retention period? (Choose one answer)