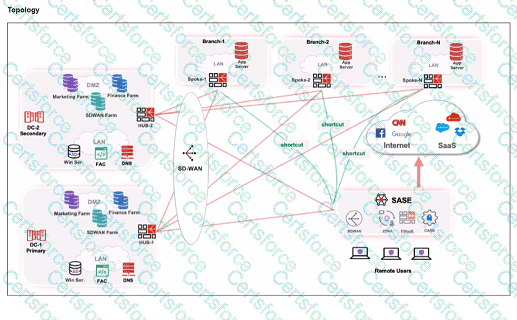
When remote users connected to FortiSASE require access to internal resources on Branch-2, the following process occurs:
SD-WAN Capability:
FortiSASE leverages SD-WAN to optimize traffic routing based on performance metrics and priorities.
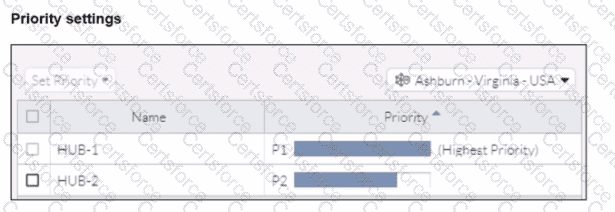
In the priority settings, HUB-1 is configured with the highest priority (P1), whereas HUB-2 has a lower priority (P2).
Traffic Routing Decision:
FortiSASE evaluates the available hubs (HUB-1 and HUB-2) and selects HUB-1 due to its highest priority setting.
Once the traffic reaches HUB-1, it is then routed to the appropriate branch based on internal routing policies.
Branch-2 Access:
Since HUB-1 has the highest priority, FortiSASE directs the traffic to HUB-1.
HUB-1 then routes the traffic to Branch-2, providing the remote users access to the internal resources.
[References:, FortiOS 7.6 Administration Guide: Details on SD-WAN configurations and priority settings., FortiSASE 23.2 Documentation: Explains how FortiSASE integrates with SD-WAN to route traffic based on defined priorities and performance metrics., ]
Submit