A systems administrator wants to introduce a newly released feature for an internal application. The administrate docs not want to test the feature in the production environment. Which of the following locations is the best place to test the new feature?
Which of the following supports the process of collecting a large pool of behavioral observations to inform decision-making?
A Chief Information Security Officer (CISO) is concerned that a company's current data disposal procedures could result in data remanence. The company uses only SSDs. Which of the following would be the most secure way to dispose of the SSDs given the CISO's concern?
A security engineer is given the following requirements:
• An endpoint must only execute Internally signed applications
• Administrator accounts cannot install unauthorized software.
• Attempts to run unauthorized software must be logged
Which of the following best meets these requirements?
An organization that performs real-time financial processing is implementing a new backup solution. Given the following business requirements:
The backup solution must reduce the risk of potential backup compromise.
The backup solution must be resilient to a ransomware attack.
The time to restore from backups is less important than backup data integrity.
Multiple copies of production data must be maintained.
Which of the following backup strategies best meets these requirements?
A company recently experienced an incident in which an advanced threat actor was able to shim malicious code against the hardware static of a domain controller The forensic team cryptographically validated that com the underlying firmware of the box and the operating system had not been compromised. However, the attacker was able to exfiltrate information from the server using a steganographic technique within LOAP Which of the following is me b»« way to reduce the risk oi reoccurrence?
A company wants to modify its process to comply with privacy requirements after an incident involving PII data in a development environment. In order to perform functionality tests, the QA team still needs to use valid data in the specified format. Which of the following best addresses the risk without impacting the development life cycle?
A company’sSIEMis designed to associate the company’sasset inventorywith user events. Given the following report:
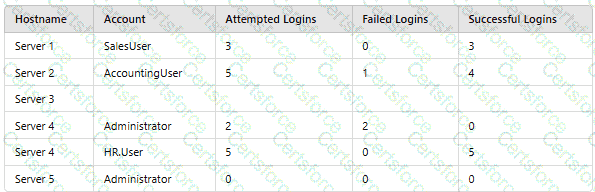
Which of thefollowing should asecurity engineer investigate firstas part of alog audit?
A company is having issues with its vulnerability management program New devices/lPs are added and dropped regularly, making the vulnerability report inconsistent Which of the following actions should the company lake to most likely improve the vulnerability management process'
A security officer performs due diligence activities before implementing a third-party solution into the enterprise environment. The security officer needs evidence from the third party that a data subject access request handling process is in place. Which of the following is the security officer most likely seeking to maintain compliance?