A security analyst Detected unusual network traffic related to program updating processes The analyst collected artifacts from compromised user workstations. The discovered artifacts were binary files with the same name as existing, valid binaries but. with different hashes which of the following solutions would most likely prevent this situation from reoccurring?
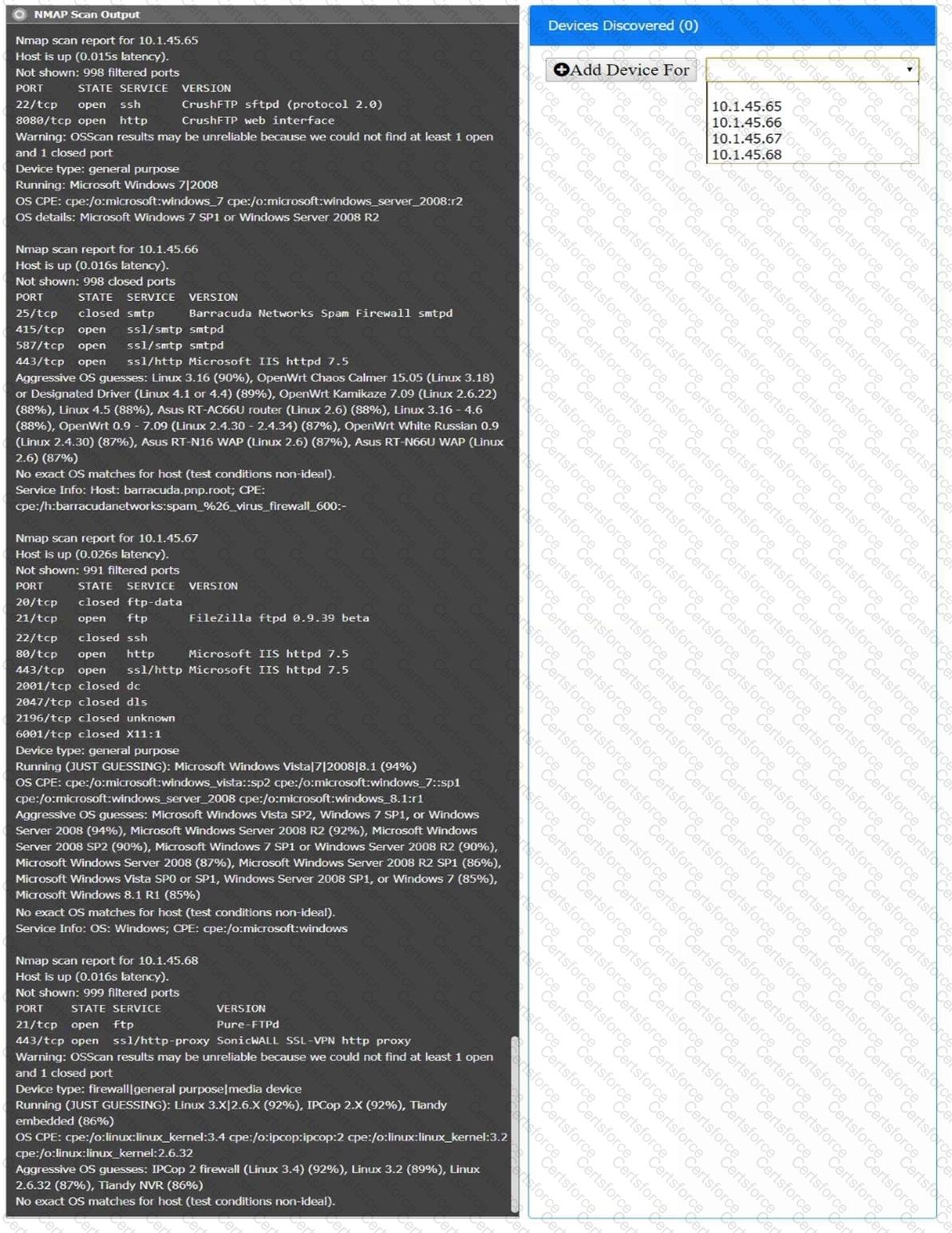
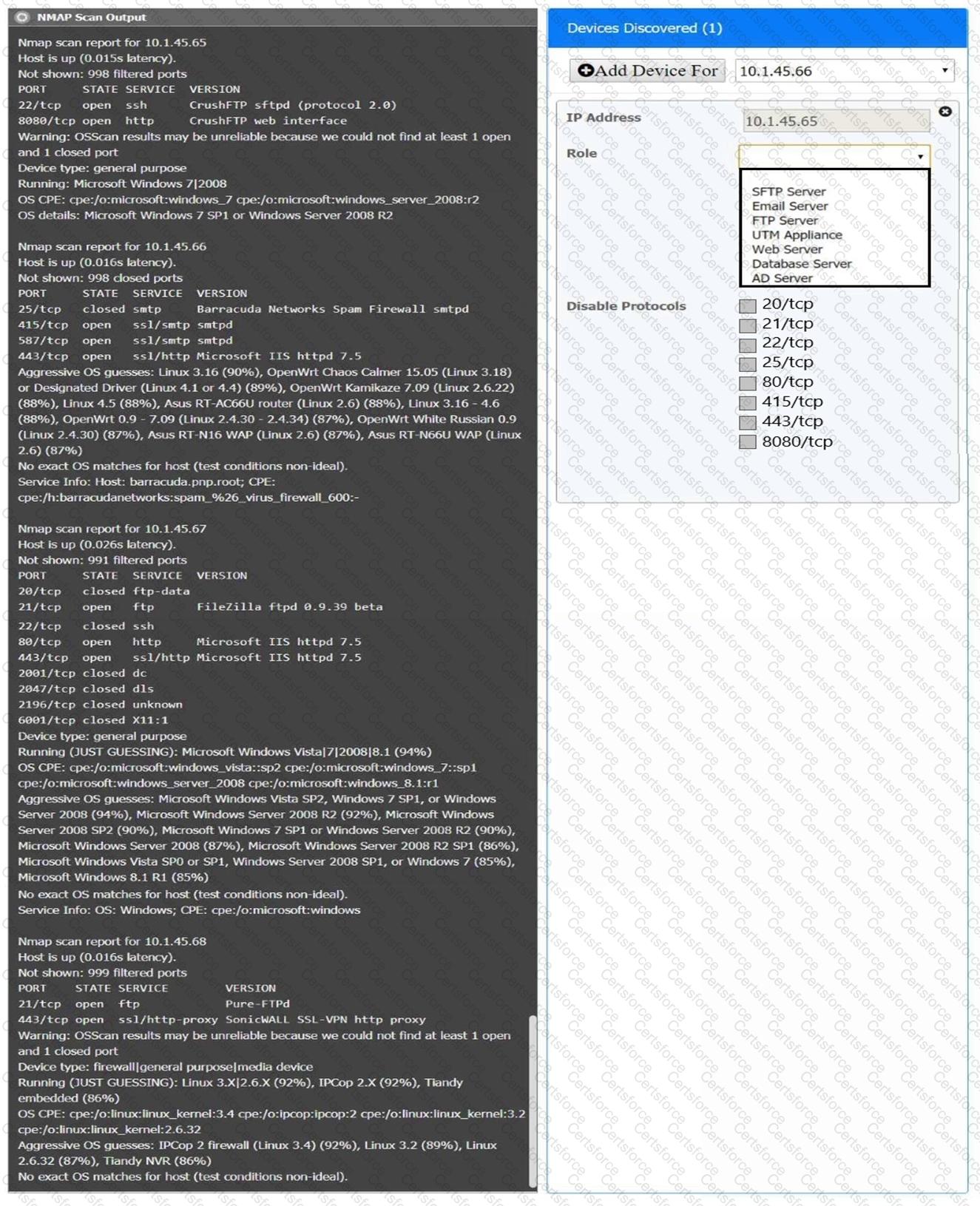
You are a security analyst tasked with interpreting an Nmap scan output from company’s privileged network.
The company’s hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only)
The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines)
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A security analyst is reviewing the following authentication logs:
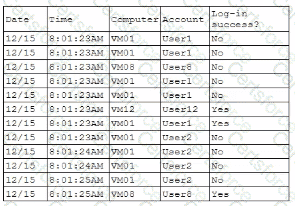
Which of thefollowing should the analyst do first?
A product development team has submitted code snippets for review prior to release.
INSTRUCTIONS
Analyze the code snippets, and then select one vulnerability, and one fix for each code snippet.
Code Snippet 1
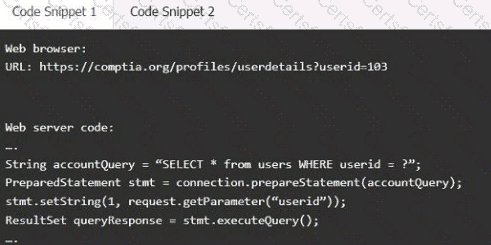
Code Snippet 2
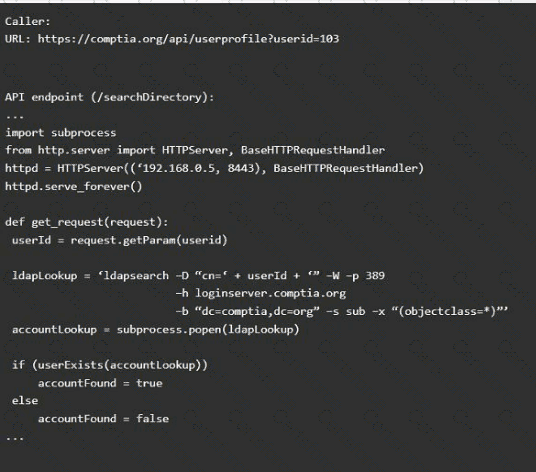
Vulnerability 1:
SQL injection
Cross-site request forgery
Server-side request forgery
Indirect object reference
Cross-site scripting
Fix 1:
Perform input sanitization of the userid field.
Perform output encoding of queryResponse,
Ensure usex:ia belongs to logged-in user.
Inspect URLS and disallow arbitrary requests.
Implementanti-forgery tokens.
Vulnerability 2
1) Denial of service
2) Command injection
3) SQL injection
4) Authorization bypass
5) Credentials passed via GET
Fix 2
A) Implement prepared statements and bind
variables.
B) Remove the serve_forever instruction.
C) Prevent the "authenticated" value from being overridden by a GET parameter.
D) HTTP POST should be used for sensitive parameters.
E) Perform input sanitization of the userid field.
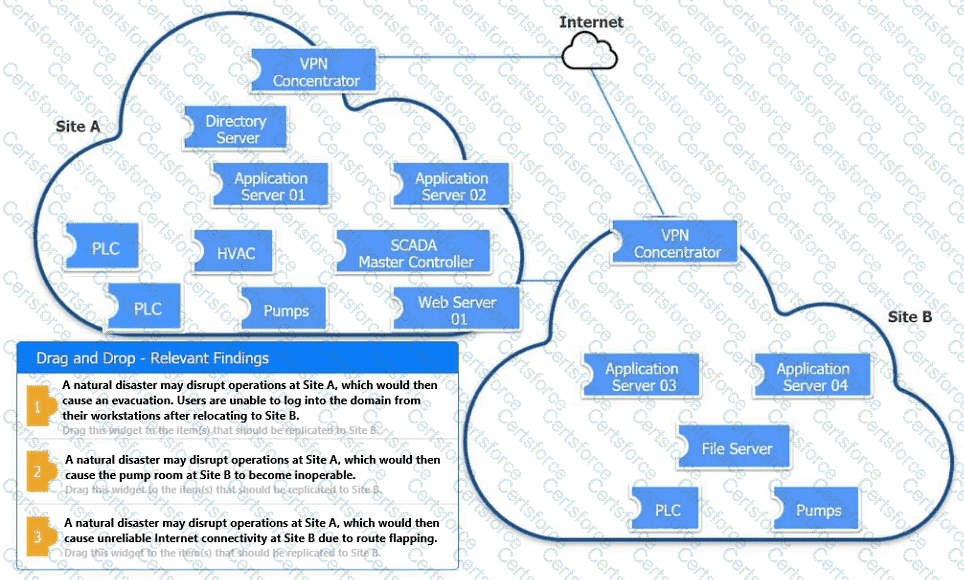
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simul-ation, please click the Reset All button.
A company detects suspicious activity associated with external connections Security detection tools are unable tocategorize this activity. Which of the following is the best solution to help the company overcome this challenge?
A security engineer wants to propose an MDM solution to mitigate certain risks. The MDM solution should meet the following requirements:
• Mobile devices should be disabled if they leave the trusted zone.
• If the mobile device is lost, data is not accessible.
Which of the following options should the security engineer enable on the MDM solution? (Select two).
A security architect is investigating instances of employees who had their phones stolen in public places through seemingly targeted attacks. Devices are able to access company resources such as email and internal documentation, some of which can persist in application storage. Which of the following would best protect the company from information exposure? (Select two).
A company wants to use loT devices to manage and monitor thermostats at all facilities The thermostats must receive vendor security updates and limit access to other devices within the organization Which of the following best addresses the company's requirements''
Operational technology often relies upon aging command, control, and telemetry subsystems that were created with the design assumption of: