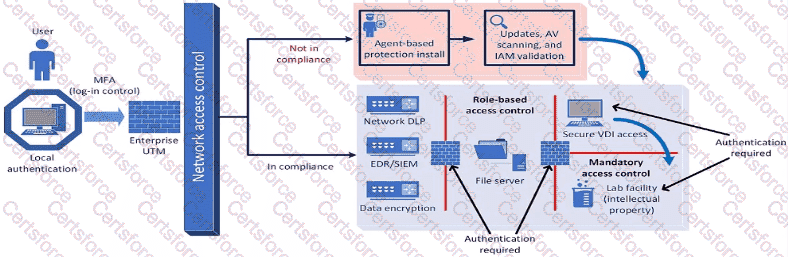
The security diagram proposed by the security architect depicts a Zero Trust security model. Zero Trust is asecurity framework that assumes all entities, both inside and outside the network, cannot be trusted and must be verified before gaining access to resources.
Key Characteristics of Zero Trust in the Diagram:
Role-based Access Control: Ensures that users have access only to the resources necessary for their role.
Mandatory Access Control: Additional layer of security requiring authentication for access to sensitive areas.
Network Access Control: Ensures that devices meet security standards before accessing the network.
Multi-factor Authentication (MFA): Enhances security by requiring multiple forms of verification.
This model aligns with the Zero Trust principles of never trusting and always verifying access requests, regardless of their origin.
[References:, CompTIA SecurityX Study Guide, NIST Special Publication 800-207, "Zero Trust Architecture", "Implementing a Zero Trust Architecture," Forrester Research, , , , , ]
Submit