Which of the following best explains the business requirement a healthcare provider fulfills by encrypting patient data at rest?
During a gap assessment, an organization notes that OYOD usage is asignificant risk. The organization implemented administrative policies prohibiting BYOD usage However, the organization has not implemented technical controls to prevent the unauthorized use of BYOD assets when accessing the organization's resources. Which of the following solutions should the organization implement to b»« reduce the risk of OYOD devices? (Select two).
A company wants to improve and automate the compliance of its cloud environments to meet industry standards. Which of the following resources should the company use to best achieve this goal?
All organization is concerned about insider threats from employees who have individual access to encrypted material. Which of the following techniques best addresses this issue?
Previously intercepted communications must remain secure even if a current encryption key is compromised in the future. Which of the following best supports this requirement?
A systems administrator wants to use existing resources to automate reporting from disparate security appliances that do not currently communicate. Which of the following is the best way to meet this objective?
A security analyst needs to ensure email domains that send phishing attempts without previous communications are not delivered to mailboxes The following email headers are being reviewed
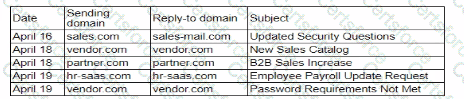
Which of thefollowing is the best action for the security analyst to take?
A senior security engineer flags me following log file snippet as hawing likely facilitated an attacker's lateral movement in a recent breach:

Which of the following solutions, if implemented, would mitigate the nsk of this issue reoccurnnp?
An organization determines existing business continuity practices areinadequateto support critical internal process dependencies during a contingency event. Acompliance analystwants the Chief Information Officer (CIO) to identify the level ofresidual riskthat is acceptable to guide remediation activities. Which of the following does the CIO need to clarify?
A company's SICM Is continuously reporting false positives and false negatives The security operations team has Implemented configuration changes to troubleshoot possible reporting errorsWhich of the following sources of information best supports the required analysts process? (Select two).