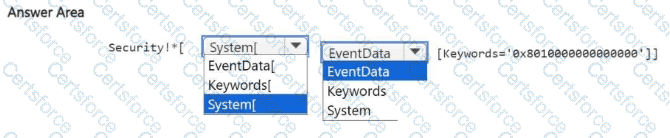
You have an Azure subscription named Sub1. Sub1 contains a Microsoft Sentinel workspace named SW1 and a virtual machine named VM1 that runs Windows Server. SW1 collects security logs from VM1 by using the Windows Security Events via AMA connector.
You need to limit the scope of events collected from VM1. The solution must ensure that only audit failure events are collected.
How should you complete the filter expression for the connector? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
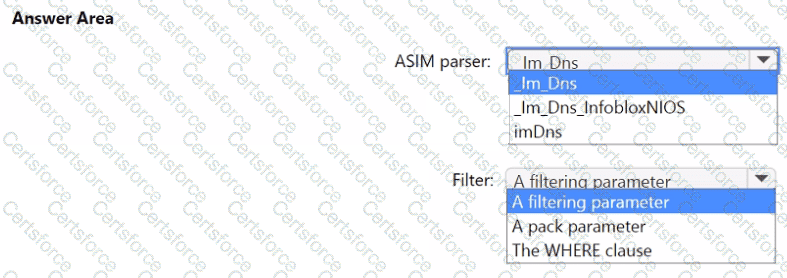
You need to implement the ASIM query for DNS requests. The solution must meet the Microsoft Sentinel requirements. How should you configure the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to modify the anomaly detection policy settings to meet the Microsoft Defender for Cloud Apps requirements and resolve the reported problem.
Which policy should you modify?
You need to implement the Azure Information Protection requirements. What should you configure first?
You need to restrict cloud apps running on CUENT1 to meet the Microsoft Defender for Endpoint requirements. Which two configurations should you modify? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
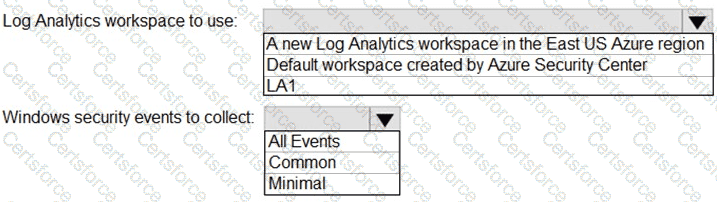
You need to implement Azure Defender to meet the Azure Defender requirements and the business requirements.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.