You are configuring Microsoft Cloud App Security.
You have a custom threat detection policy based on the IP address ranges of your company’s United States-based offices.
You receive many alerts related to impossible travel and sign-ins from risky IP addresses.
You determine that 99% of the alerts are legitimate sign-ins from your corporate offices.
You need to prevent alerts for legitimate sign-ins from known locations.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
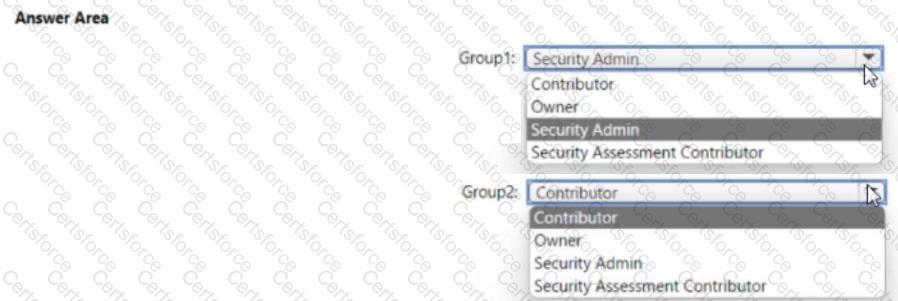
You need to assign role-based access control (RBAQ roles to Group1 and Group2 to meet The Microsoft Defender for Cloud requirements and the business requirements Which role should you assign to each group? To answer, select the appropriate options in the answer area NOTE Each correct selection is worth one point.
You have a Microsoft Sentinel workspace named sws1.
You plan to create an Azure logic app that will raise an incident in an on-premises IT service management system when an incident is generated in sws1.
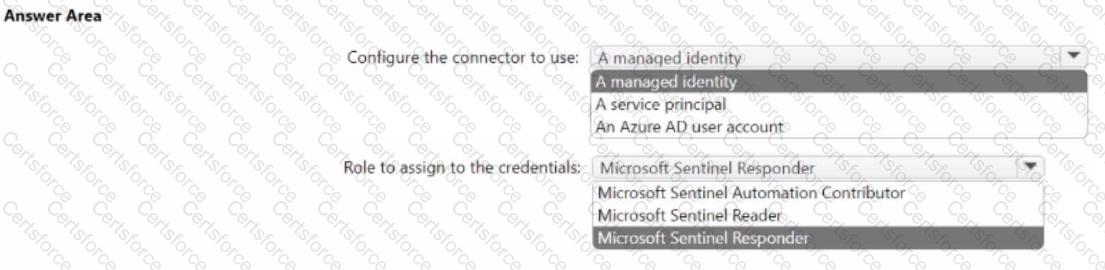
You need to configure the Microsoft Sentinel connector credentials for the logic app. The solution must meet the following requirements:
• Minimize administrative effort.
• Use the principle of least privilege.
How should you configure the credentials? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Your company uses Azure Sentinel to manage alerts from more than 10,000 IoT devices.
A security manager at the company reports that tracking security threats is increasingly difficult due to the large number of incidents.
You need to recommend a solution to provide a custom visualization to simplify the investigation of threats and to infer threats by using machine learning.
What should you include in the recommendation?
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR and contains a Windows device named Device1.
You investigate Device1 for malicious activity and discover a suspicious file named File1.exe. You collect an investigation package from Device1.
You need to review the following forensic data points:
. Is an attacker currently accessing Device1 remotely?
. When was File1.exe first executed?
Which folder in the investigation package should you review for each data point? To answer, select the appropriate options in the answer area.

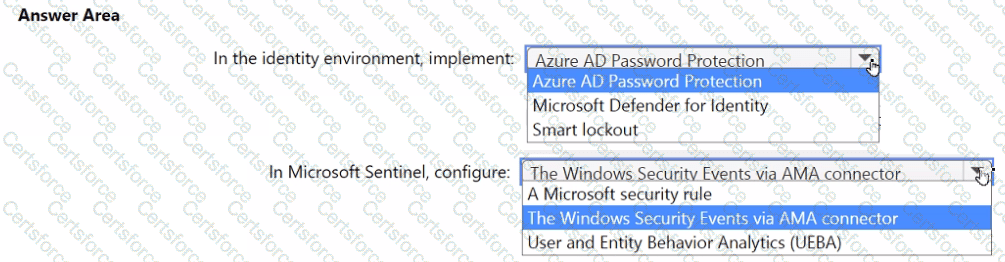
You need to monitor the password resets. The solution must meet the Microsoft Sentinel requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to ensure that the processing of incidents generated by rulequery1 meets the Microsoft Sentinel requirements.
What should you create first?
You need to implement the scheduled rule for incident generation based on rulequery1.
What should you configure first?
You need to configure event monitoring for Server1. The solution must meet the Microsoft Sentinel requirements. What should you create first?
You need to ensure that the configuration of HuntingQuery1 meets the Microsoft Sentinel requirements.
What should you do?