You have a Microsoft 365 subscription that contains the following resources:
• 100 users that are assigned a Microsoft 365 E5 license
• 100 Windows 11 devices that are joined to the Microsoft Entra tenant
The users access their Microsoft Exchange Online mailbox by using Outlook on the web.
You need to ensure that if a user account is compromised, the Outlook on the web session token can be revoked.
What should you configure?
A security administrator receives email alerts from Azure Defender for activities such as potential malware uploaded to a storage account and potential successful brute force attacks.
The security administrator does NOT receive email alerts for activities such as antimalware action failed and suspicious network activity. The alerts appear in Azure Security Center.
You need to ensure that the security administrator receives email alerts for all the activities.
What should you configure in the Security Center settings?
You have the following SQL query.
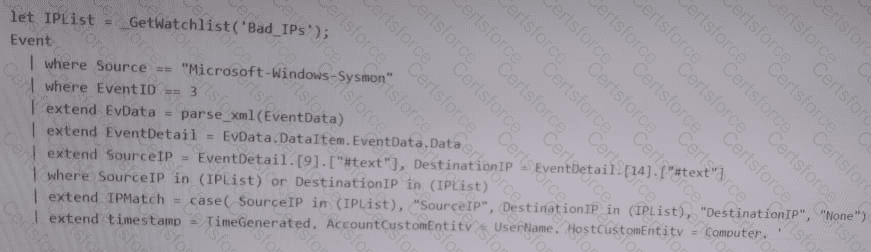
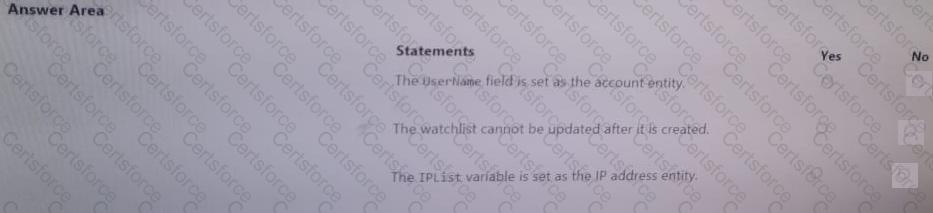
You have a Microsoft Sentinel workspace named sws1.
You need to create a query that will detect when a user creates an unusually large numbers of Azure AD user accounts.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
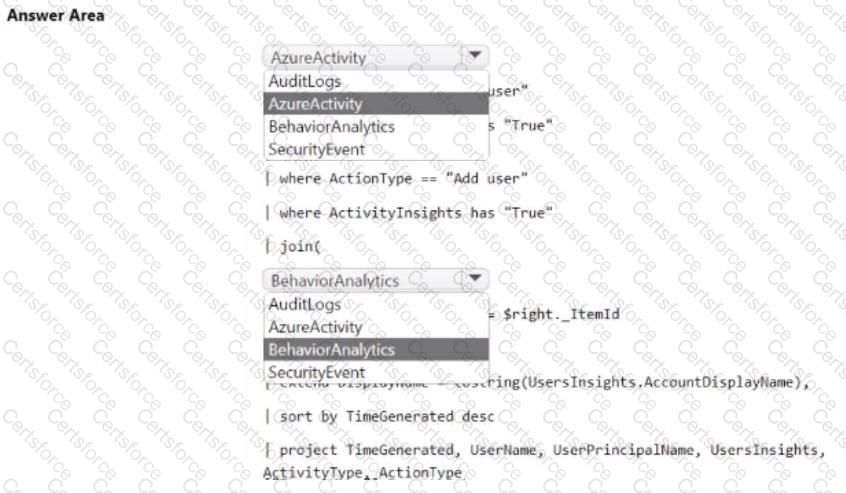
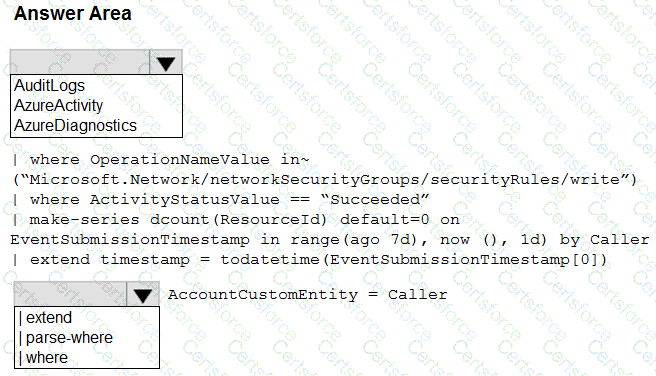
You have an Azure subscription that contains an Microsoft Sentinel workspace.
You need to create a hunting query using Kusto Query Language (KQL) that meets the following requirements:
• Identifies an anomalous number of changes to the rules of a network security group (NSG) made by the same security principal
• Automatically associates the security principal with an Microsoft Sentinel entity
How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
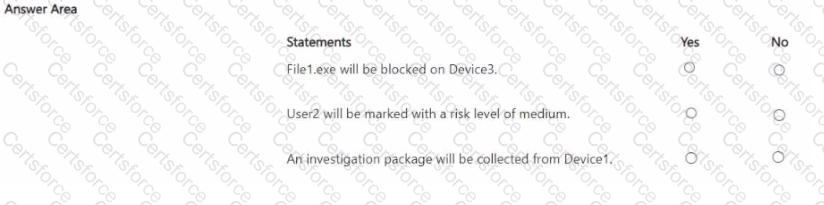
You have a Microsoft 365 subscription that contains three users named User1. User2 and User3 and the resources shown in the following table.

You have a Microsoft Defender XDR detection rule named Rule1 that has the following configurations:
• Scope: DevGroup1
• File hash: File1.exe
• Actions
o Devices: Collect investigation package
o User: Mark as compromised o Files: Block
Each user attempts to run File1.exe on their device.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have a Microsoft Sentinel workspace.
A Microsoft Sentinel incident is generated as shewn in the following exhibit.
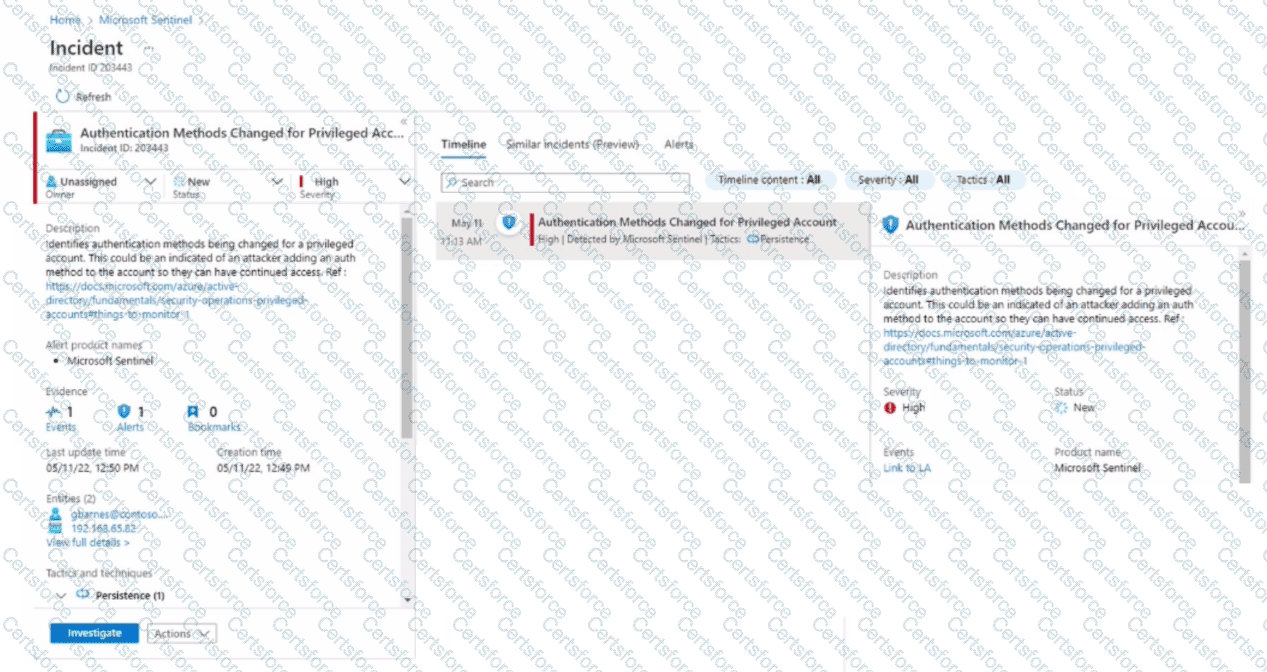
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

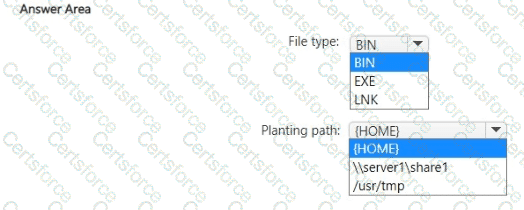
You have a Microsoft 365 E5 subscription that contains Windows 11 and Linux CentOS devices.
In Microsoft Defender XDR, Deception is set to On.
You plan to create a deception rule that will use a custom lure.
You need to specify the type of file, and the planting path for for the custom lure,
What should you specify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You create an Azure subscription.
You enable Microsoft Defender for Cloud for the subscription.
You need to use Defender for Cloud to protect on-premises computers.
What should you do on the on-premises computers?
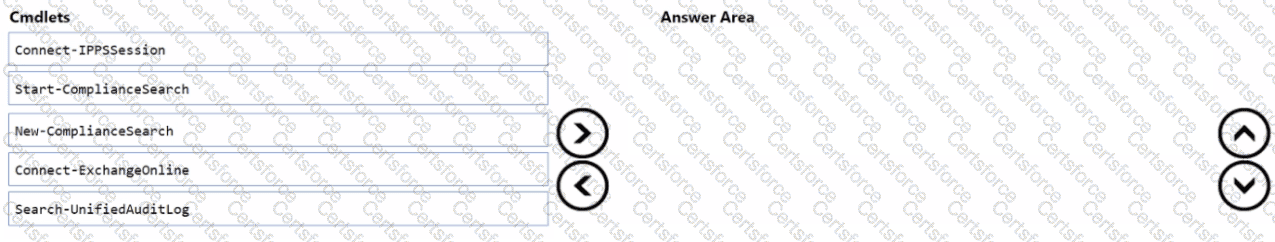
You have a Microsoft 365 E5 subscription that uses Microsoft Exchange Online.
You need to identify phishing email messages.
Which three cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.