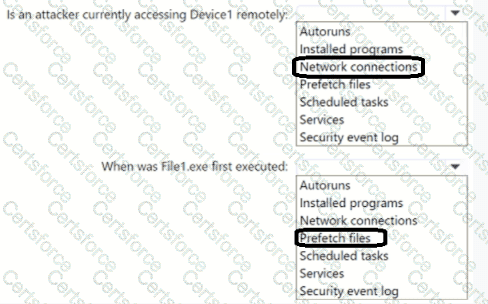
To determine whether a device is being accessed remotely by an attacker, analysts must inspect active network connections collected from the investigation package.
Microsoft Defender for Endpoint investigation packages contain a NetworkConnections.txt file that includes all established, listening, and closed network sessions, including remote IP addresses, ports, and associated processes.
Microsoft’s official Defender for Endpoint documentation states:
“The investigation package includes a list of active network connections at the time of collection, helping analysts identify potential remote access activity or suspicious outbound connections.”
By reviewing the network connections folder/file, you can check for any live sessions to external IPs, RDP, SSH, or other remote-control tools indicating an attacker’s presence.
Data Point 2: When was File1.exe first executed?
✅ Verified Answer = Prefetch files
To find when a file was first executed, you use Prefetch files.
Windows Prefetch is a forensic artifact that records metadata about executables that have been launched, including:
The number of times executed
The path and hash of the executable
Microsoft’s forensic analysis guidance for Defender investigation packages specifies:
“Prefetch files provide information on when applications were first and last executed, which assists in establishing file execution timelines during investigations.”
Therefore, to determine when File1.exe was first executed, you should analyze the Prefetch files contained within the investigation package.
✅ Final Verified Answers:
Forensic Data Point
Folder/File to Review
Is an attacker currently accessing Device1 remotely?
Network connections
When was File1.exe first executed?
Prefetch files
Summary:
These answers align with Microsoft Defender for Endpoint investigation package structure and Microsoft 365 E5 SecOps documentation.

Submit