
In Microsoft Sentinel, when using the Windows Security Events via AMA (Azure Monitor Agent) connector, you can configure an XPath filter expression to control which Windows security events are collected from a connected virtual machine.
Microsoft’s documentation specifies that event filtering is based on the EventLog XML schema, and filtering by Keywords allows you to target specific audit categories. In Windows Security logs, events are categorized as follows by their Keywords bitmask:
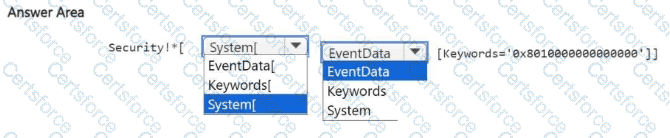
Since the requirement is to collect only audit failure events, the XPath filter must include only the System node (which contains the event header metadata) and filter by the Keywords attribute equal to 0x8010000000000000.
The correct XPath syntax for the filter in this case is:
Security!*[System[Keywords='0x8010000000000000']]
Explanation of components:
System[...] — Refers to the event’s header metadata section (where Keywords, EventID, and Level are stored).
Keywords='0x8010000000000000' — Matches only events that have the Audit Failure bit set.
Therefore, only events with Audit Failure outcomes will be collected from VM1, satisfying the requirement to minimize event ingestion and reduce unnecessary log noise.
✅ Final Answer: Security!*[System[Keywords='0x8010000000000000']]
Submit