You are asked to implement IPS on your SRX Series device.
In this scenario, which two tasks must be completed before a configuration will work? (Choose two.)
Click the Exhibit button.
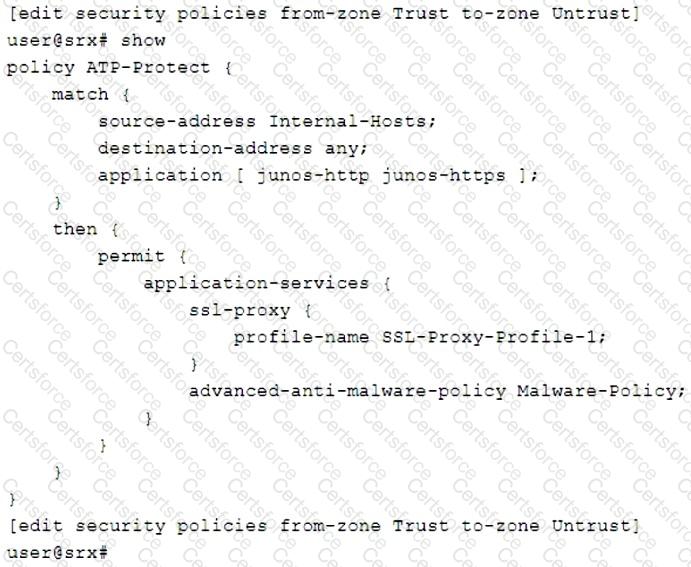
You are asked to create a security policy that will automatically add infected hosts to the infected hosts feed and block further communication through the SRX Series device.
What needs to be added to this configuration to complete this task?
You are asked to block malicious applications regardless of the port number being used.
In this scenario, which two application security features should be used? (Choose two.)
You are configuring logging for a security policy.
In this scenario, in which two situations would log entries be generated? (Choose two.)
Which three statements about SRX Series device chassis clusters are true? (Choose three.)
Which two statements are correct about AppTrack? (Choose two.)
You want to be alerted if the wrong password is used more than three times on a single device within five minutes.
Which Juniper Networks solution will accomplish this task?
Which two statements about SRX chassis clustering are correct? (Choose two.)
You are asked to create an IPS-exempt rule base to eliminate false positives from happening.
Which two configuration parameters are available to exclude traffic from being examined? (Choose two.)