Exhibit
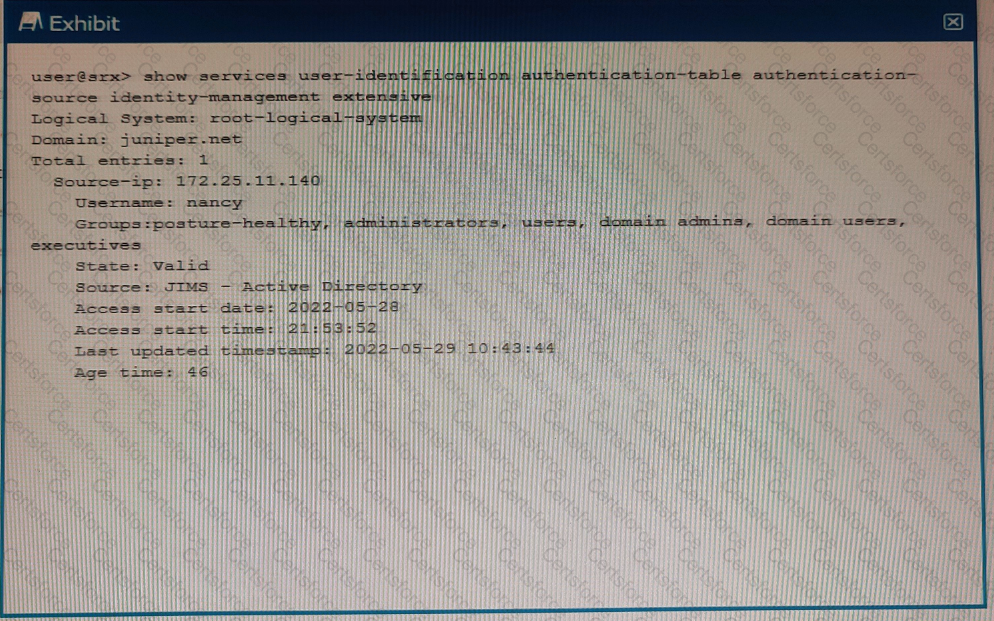
Referring to the exhibit, which two statements are true? (Choose two.)
You need to deploy an SRX Series device in your virtual environment.
In this scenario, what are two benefits of using a CSRX? (Choose two.)
What are three capabilities of AppQoS? (Choose three.)
Your network uses a single JSA host and you want to implement a cluster.
In this scenario, which two statements are correct? (Choose two.)
A client has attempted communication with a known command-and-control server and it has reached the configured threat level threshold.
Which feed will the clients IP address be automatically added to in this situation?
You enable chassis clustering on two devices and assign a cluster ID and a node ID to each device.
In this scenario, what is the correct order for rebooting the devices?
On which three Hypervisors is vSRX supported? (Choose three.)
Which two statements are correct about the fab interface in a chassis cluster? (Choose two.)
Click the Exhibit button.
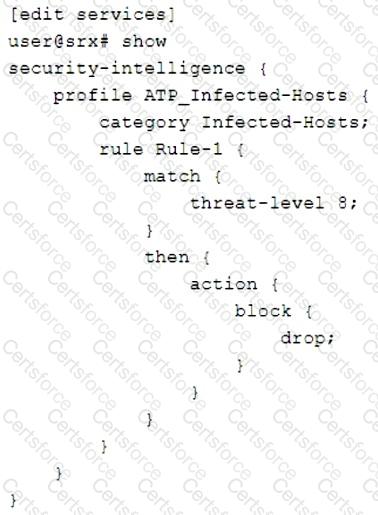
Referring to the exhibit, what will the SRX Series device do in this configuration?
Exhibit
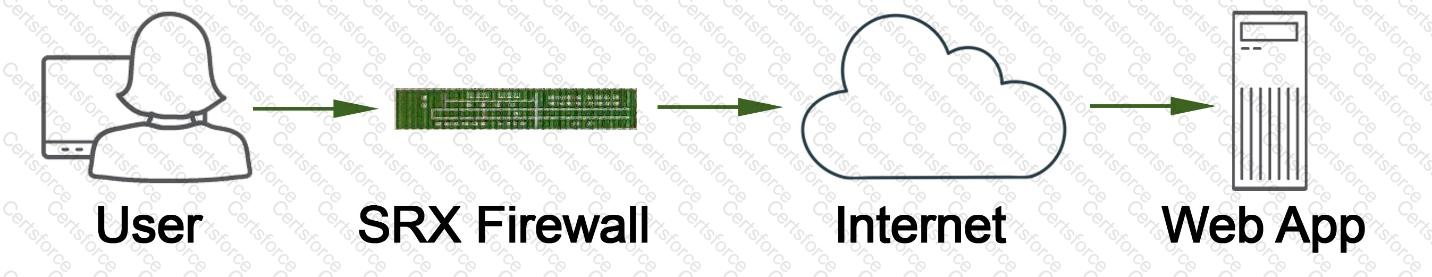
Referring to the exhibit, which two statements describe the type of proxy used? (Choose two.)