Exhibit.
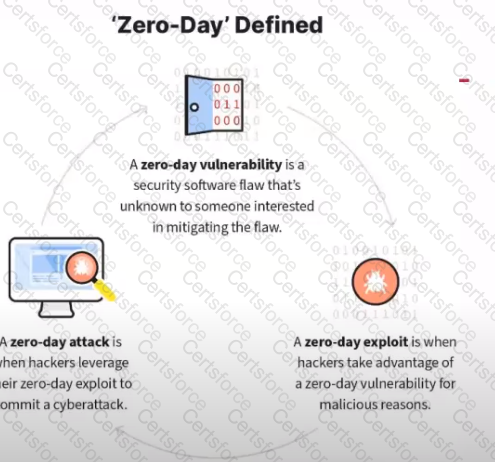
What kind of vulnerability is typically not identifiable through a standard vulnerability assessment?
Which one of the following cryptographic algorithms does not depend upon the prime factorization problem?
Which layer of OSI the Firewall works
4 Embedded systems and network-enabled devices that communicate with the internet are considered as
The means by which a threat actor carries out their objectives
Which of these activities is often associated with DR efforts?
Which is the component of a Business Continuity (BC) plan
A standard that defines wired communications of network devices
A collection of actions that must be followed in order to complete a task or process in accordance with a set of rules
EKristal is the security administrator for a large online service provider. Kristal learns that the company is harvesting personal data of its customers and sharing the data with local governments where the company operates, without the knowledge of the users, to allow the governments to persecute users on the basis of their political and philosophical beliefs. The published user agreement states that the company will not share personal user data with any entities without the users' explicit permission. According to the ISC2 Code of Ethics, to whom does Kristal ultimately report in this situation?