A company needs to protect its confidential data from unauthorized access which logical control is best suited for this scenario
How many bits represent the organization unique identifier (oui) in mac addresses?
A common network device used to filter traffic?
The documentation of a predetermined set of instructions or procedures to detect, respond to andlimit consequences of a malicious cyberattack against an organization's information systems(s).
Port used in DNS
Exhibit.
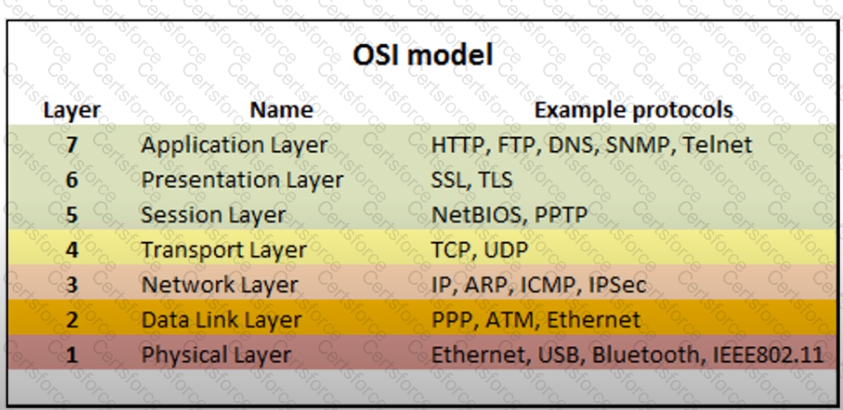
IPSec works in which layer of OSI Model
Which of the following is a common security measure to prevent Cross Site Scripting (XSS) attacks in web applications?
The common term used to describe the mechanisms that control the temperature and humidity in a data center
Type 1 authentication posses
If a device is found that is not compliant with the security baseline, what will be the security team action