What is the role of test automation in security testing?
Attempting an injection attack on a web server based on responses to True/False questions is called which of the following?
Which of the following areas is considered a strength of symmetric key cryptography when compared with asymmetric algorithms?
Craig received a report of all the computers on the network that showed all the missing patches and weak passwords. What type of software generated this report?
A well-intentioned researcher discovers a vulnerability on the web site of a major corporation. What should he do?
Which of the following tools is used to analyze the files produced by several packet-capture programs such as tcpdump, WinDump, Wireshark, and EtherPeek?
Websites and web portals that provide web services commonly use the Simple Object Access Protocol SOAP. Which of the following is an incorrect definition or characteristics in the protocol?
A hacker has managed to gain access to a Linux host and stolen the password file from /etc/passwd. How can he use it?
In IPv6 what is the major difference concerning application layer vulnerabilities compared to IPv4?
Which of the following is an NMAP script that could help detect HTTP Methods such as GET, POST, HEAD, PUT, DELETE, TRACE?
You want to analyze packets on your wireless network. Which program would you use?
A specific site received 91 ICMP_ECHO packets within 90 minutes from 47 different sites.
77 of the ICMP_ECHO packets had an ICMP ID:39612 and Seq:57072. 13 of the ICMP_ECHO packets had an ICMP ID:0 and Seq:0. What can you infer from this information?
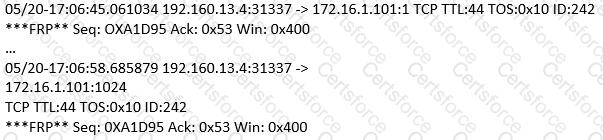
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.). Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.
A new wireless client that is 802.11 compliant cannot connect to a wireless network given that the client can see the network and it has compatible hardware and software installed. Upon further tests and investigation, it was found out that the Wireless Access Point (WAP) was not responding to the association requests being sent by the wireless client. What MOST likely is the issue on this scenario?
Your next door neighbor, that you do not get along with, is having issues with their network, so he yells to his spouse the network's SSID and password and you hear them both clearly. What do you do with this information?