During a penetration test, a tester finds a target that is running MS SQL 2000 with default credentials. The tester assumes that the service is running with Local System account. How can this weakness be exploited to access the system?
What is the main reason the use of a stored biometric is vulnerable to an attack?
Which of the following techniques does a vulnerability scanner use in order to detect a vulnerability on a target service?
Which of the following does proper basic configuration of snort as a network intrusion detection system require?
What is the broadcast address for the subnet 190.86.168.0/22?
A penetration tester was hired to perform a penetration test for a bank. The tester began searching for IP ranges owned by the bank, performing lookups on the bank's DNS servers, reading news articles online about the bank, watching what times the bank employees come into work and leave from work, searching the bank's job postings (paying special attention to IT related jobs), and visiting the local dumpster for the bank's corporate office. What phase of the penetration test is the tester currently in?
John the Ripper is a technical assessment tool used to test the weakness of which of the following?
Which of the following techniques will identify if computer files have been changed?
Which tool is used to automate SQL injections and exploit a database by forcing a given web application to connect to another database controlled by a hacker?
Which of the following items of a computer system will an anti-virus program scan for viruses?
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set:
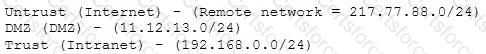
The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
Which NMAP command combination would let a tester scan every TCP port from a class C network that is blocking ICMP with fingerprinting and service detection?
Which type of scan measures a person's external features through a digital video camera?
A security policy will be more accepted by employees if it is consistent and has the support of
When creating a security program, which approach would be used if senior management is supporting and enforcing the security policy?