Which of these options is the most secure procedure for storing backup tapes?
The establishment of a TCP connection involves a negotiation called 3 way handshake. What type of message sends the client to the server in order to begin this negotiation?
A company's security policy states that all Web browsers must automatically delete their HTTP browser cookies upon terminating. What sort of security breach is this policy attempting to mitigate?
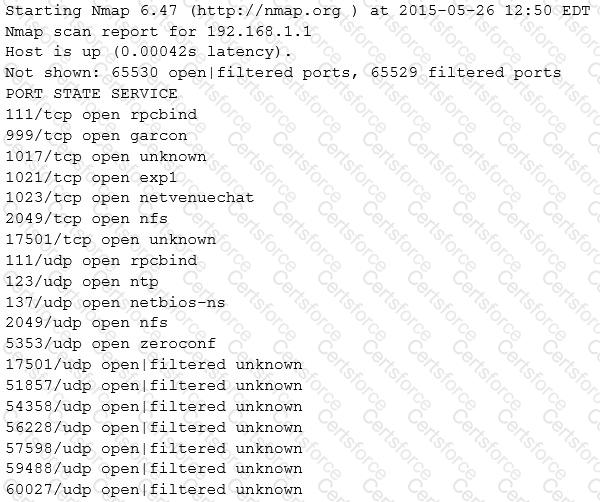
Which of the following Nmap commands will produce the following output?
Output:
The "black box testing" methodology enforces which kind of restriction?
Which of the following is one of the most effective ways to prevent Cross-site Scripting (XSS) flaws in software applications?
Which Metasploit Framework tool can help penetration tester for evading Anti-virus Systems?
Which of the following programming languages is most susceptible to buffer overflow attacks, due to its lack of a built-in-bounds checking mechanism?

Output:
Segmentation fault
What is the difference between the AES and RSA algorithms?
The chance of a hard drive failure is once every three years. The cost to buy a new hard drive is $300. It will require 10 hours to restore the OS and software to the new hard disk. It will require a further 4 hours to restore the database from the last backup to the new hard disk. The recovery person earns $10/hour. Calculate the SLE, ARO, and ALE. Assume the EF = 1 (100%).
What is the closest approximate cost of this replacement and recovery operation per year?
The "gray box testing" methodology enforces what kind of restriction?
In order to have an anonymous Internet surf, which of the following is best choice?
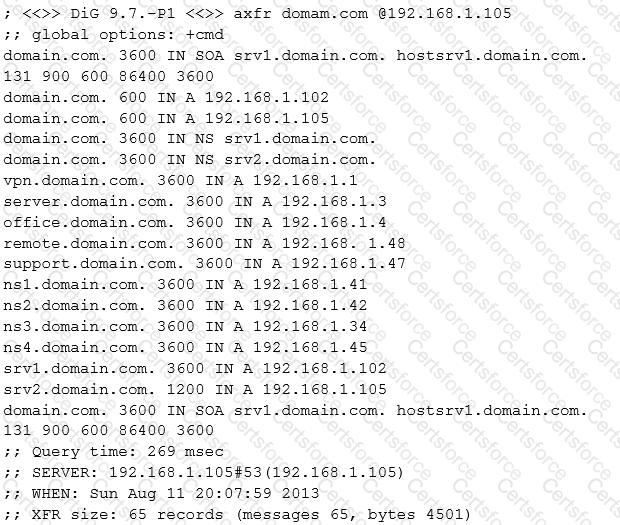
Look at the following output. What did the hacker accomplish?
Which of the following types of firewalls ensures that the packets are part of the established session?
The company ABC recently contracted a new accountant. The accountant will be working with the financial statements. Those financial statements need to be approved by the CFO and then they will be sent to the accountant but the CFO is worried because he wants to be sure that the information sent to the accountant was not modified once he approved it. What of the following options can be useful to ensure the integrity of the data?