Vlady works in a fishing company where the majority of the employees have very little understanding of IT let alone IT Security. Several information security issues that Vlady often found includes, employees sharing password, writing his/her password on a post it note and stick it to his/her desk, leaving the computer unlocked, didn’t log out from emails or other social media accounts, and etc.
After discussing with his boss, Vlady decided to make some changes to improve the security environment in his company. The first thing that Vlady wanted to do is to make the employees understand the importance of keeping confidential information, such as password, a secret and they should not share it with other persons.
Which of the following steps should be the first thing that Vlady should do to make the employees in his company understand to importance of keeping confidential information a secret?
In which of the following password protection technique, random strings of characters are added to the password before calculating their hashes?
You need a tool that can do network intrusion prevention and intrusion detection, function as a network sniffer, and record network activity, what tool would you most likely select?
What is the minimum number of network connections in a multi homed firewall?
Your business has decided to add credit card numbers to the data it backs up to tape. Which of the
following represents the best practice your business should observe?
You need to deploy a new web-based software package for your organization. The package requires three separate servers and needs to be available on the Internet. What is the recommended architecture in terms of server placement?
In Wireshark, the packet bytes panes show the data of the current packet in which format?
Code injection is a form of attack in which a malicious user:
A virus that attempts to install itself inside the file it is infecting is called?
Cross-site request forgery involves:
Which of the following types of jailbreaking allows user-level access but does not allow iboot-level access?
Which of the following cryptography attack is an understatement for the extraction of cryptographic secrets (e.g. the password to an encrypted file) from a person by a coercion or torture?
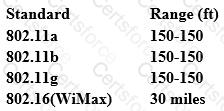
From the following table, identify the wrong answer in terms of Range (ft).
A pen tester is configuring a Windows laptop for a test. In setting up Wireshark, what river and library
are required to allow the NIC to work in promiscuous mode?
Steve, a scientist who works in a governmental security agency, developed a technological solution to identify people based on walking patterns and implemented this approach to a physical control access.
A camera captures people walking and identifies the individuals using Steve’s approach.
After that, people must approximate their RFID badges. Both the identifications are required to open the door.
In this case, we can say: