Refer to the exhibit.
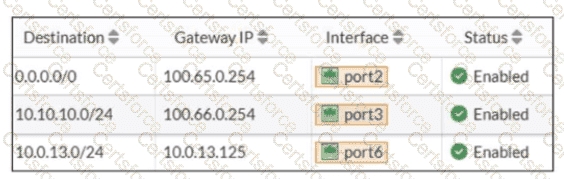
Based on the routing table shown in the exhibit, which two statements are true? (Choose two.)
Refer to the exhibit.
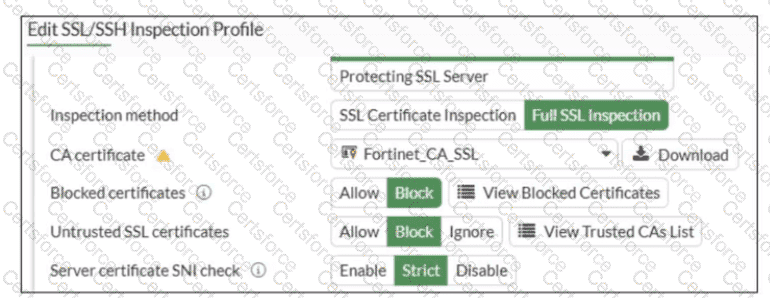
What would be the impact of these settings on the Server certificate SNI check configuration on FortiGate?
Refer to the exhibits.
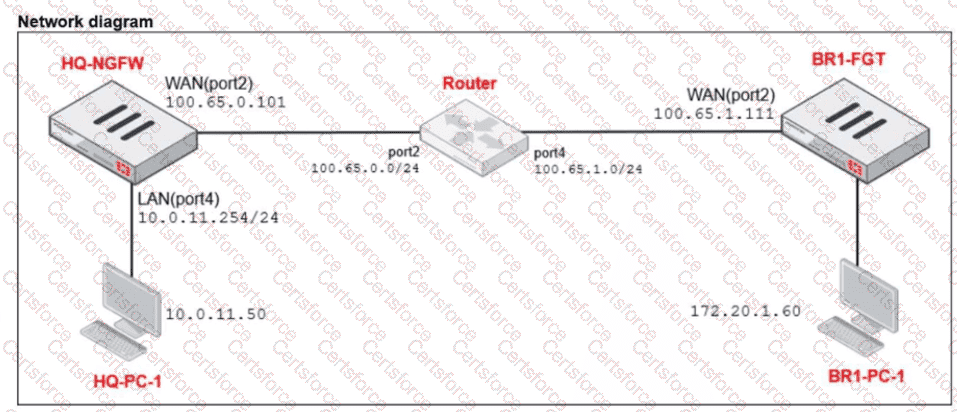
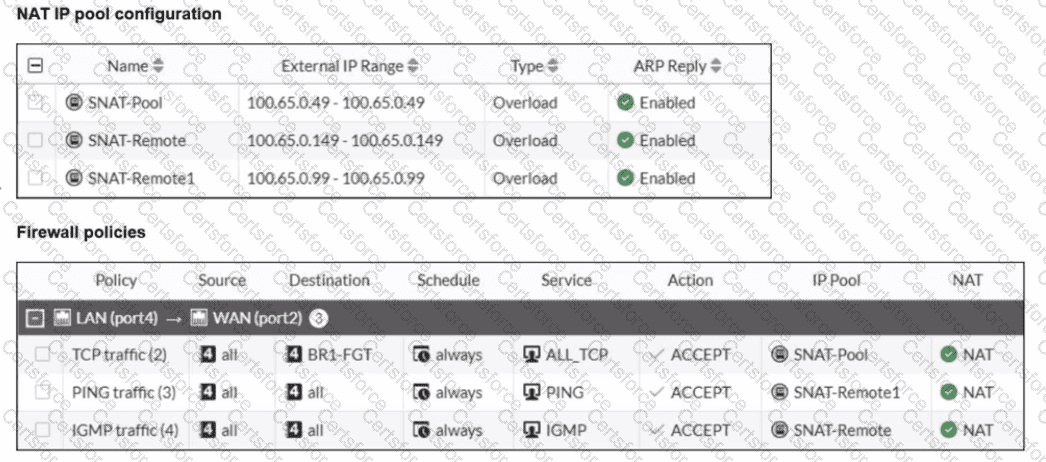
The exhibits show a diagram of a FortiGate device connected to the network, as well as the IP pool configuration and firewall policy objects.
The WAN (port2) interface has the IP address
100.65.0.101/24.
The LAN (port4) interface has the IP address
10.0.11.254/24.
Which IP address will be used to source NAT (SNAT) the traffic, if the user on HQ-PC-1 (10.0.11.50) pings the IP address of BR-FGT (100.65.1.111)?
An administrator wants to configure dead peer detection (DPD) on IPsec VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when there is no inbound traffic.
Which DPD mode on FortiGate meets this requirement?
Refer to the exhibit.
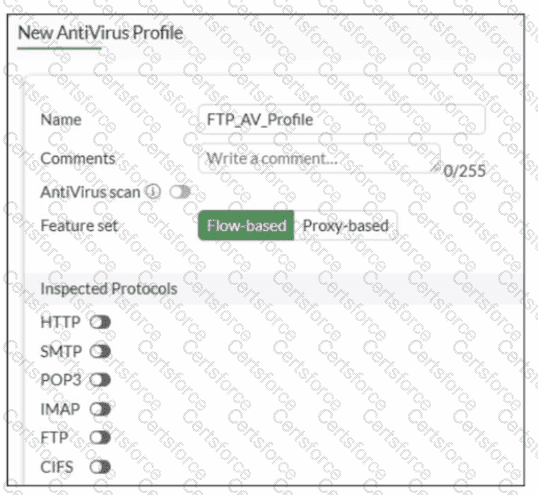
Why is the Antivirus scan switch grayed out when you are creating a new antivirus profile for FTP?
Which two components are part of the secure internet access (SIA) agent-based mode on FortiSASE? (Choose two.)
Refer to the exhibit.
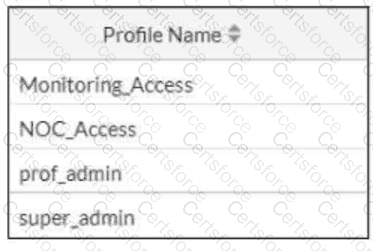
The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that their GUI sessions do not disconnect too early during inactivity. What must the administrator configure to answer this specific request from the NOC team? (Choose one answer)
Refer to the exhibit.
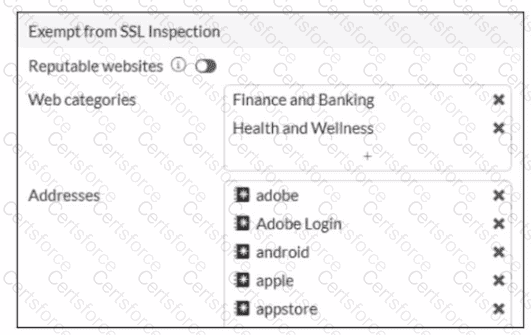
The predefined deep-inspection and custom-deep-inspection profiles exclude some web categories from SSL inspection, as shown in the exhibit For which two reasons are these web categories exempted? (Choose two.)