A remote user tries to login to a secure network using Telnet, but accidently types in an invalid user name or password. Which responses would NOT be preferred by an experienced Security Manager? (multiple answer)
What happens during a SYN flood attack?
Which of the following is the primary objective of a rootkit?
In the following example, which of these is the "exploit"?
Today, Microsoft Corporation released a security notice. It detailed how a person could bring down the Windows 2003 Server operating system, by sending malformed packets to it. They detailed how this malicious process had been automated using basic scripting. Even worse, the new automated method for bringing down the server has already been used to perform denial of service attacks on many large commercial websites.
Select the best answer.
Eric has discovered a fantastic package of tools named Dsniff on the Internet. He has learnt to use these tools in his lab and is now ready for real world exploitation. He was able to effectively intercept communications between the two entities and establish credentials with both sides of the connections. The two remote ends of the communication never notice that Eric is relaying the information between the two.
What would you call this attack?
Susan has attached to her company’s network. She has managed to synchronize her boss’s sessions with that of the file server. She then intercepted his traffic destined for the server, changed it the way she wanted to and then placed it on the server in his home directory. What kind of attack is Susan carrying on?
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
A POP3 client contacts the POP3 server:
When discussing passwords, what is considered a brute force attack?
Exhibit:
Based on the following extract from the log of a compromised machine, what is the hacker really trying to steal?
What does the following command in netcat do?
nc -l -u -p55555 < /etc/passwd
Which one of the following network attacks takes advantages of weaknesses in the fragment reassembly functionality of the TCP/IP protocol stack?
_____ is the process of converting something from one representation to the simplest form. It deals with the way in which systems convert data from one form to another.
What is GINA?
Peter, a Network Administrator, has come to you looking for advice on a tool that would help him perform SNMP enquires over the network. Which of these tools would do the SNMP enumeration he is looking for?
Select the best answers.
Attackers can potentially intercept and modify unsigned SMB packets, modify the traffic and forward it so that the server might perform undesirable actions. Alternatively, the attacker could pose as the server or client after a legitimate authentication and gain unauthorized access to data. Which of the following is NOT a means that can be used to minimize or protect against such an attack?
Tess King is using the nslookup command to craft queries to list all DNS information (such as Name Servers, host names, MX records, CNAME records, glue records (delegation for child Domains), zone serial number, TimeToLive (TTL) records, etc) for a Domain. What do you think Tess King is trying to accomplish? Select the best answer.
In Linux, the three most common commands that hackers usually attempt to Trojan are:
John wishes to install a new application onto his Windows 2000 server.
He wants to ensure that any application he uses has not been Trojaned.
What can he do to help ensure this?
Exhibit:
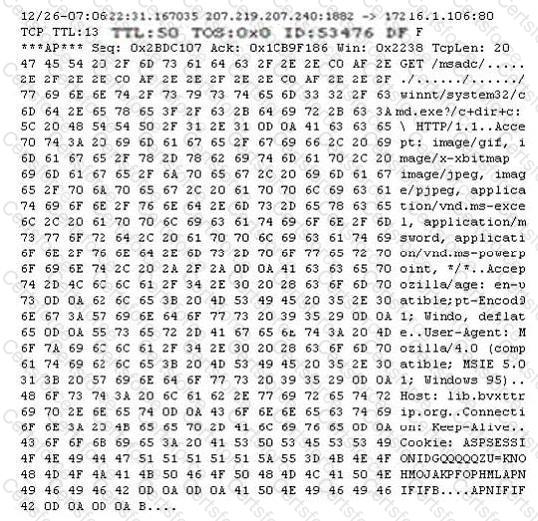
Study the following log extract and identify the attack.