What port scanning method involves sending spoofed packets to a target system and then looking for adjustments to the IPID on a zombie system?
You have initiated an active operating system fingerprinting attempt with nmap against a target system:
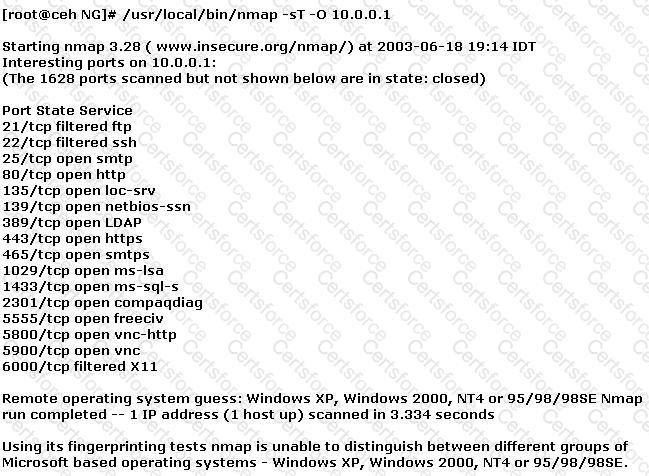
What operating system is the target host running based on the open ports shown above?
Which of the following activities will NOT be considered as passive footprinting?
You are scanning into the target network for the first time. You find very few conventional ports open. When you attempt to perform traditional service identification by connecting to the open ports, it yields either unreliable or no results. You are unsure of which protocols are being used. You need to discover as many different protocols as possible.
Which kind of scan would you use to achieve this? (Choose the best answer)
Paul has just finished setting up his wireless network. He has enabled numerous security features such as changing the default SSID, enabling WPA encryption, and enabling MAC filtering on his wireless router. Paul notices that when he uses his wireless connection, the speed is sometimes 54 Mbps and sometimes it is only 24Mbps or less. Paul connects to his wireless router's management utility and notices that a machine with an unfamiliar name is connected through his wireless connection. Paul checks the router's logs and notices that the unfamiliar machine has the same MAC address as his laptop. What is Paul seeing here?
An nmap command that includes the host specification of 202.176.56-57.* will scan _______ number of hosts.
What are two types of ICMP code used when using the ping command?
A person approaches a network administrator and wants advice on how to send encrypted email from home. The end user does not want to have to pay for any license fees or manage server services. Which of the following is the most secure encryption protocol that the network administrator should recommend?
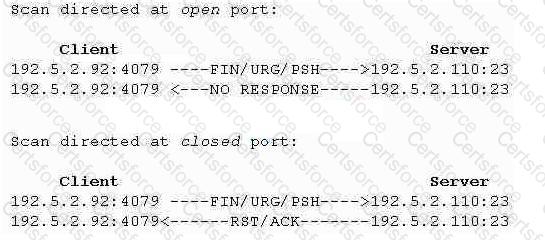
What type of port scan is shown below?
You are conducting a port scan on a subnet that has ICMP blocked. You have discovered 23 live systems and after scanning each of them you notice that they all show port 21 in closed state.
What should be the next logical step that should be performed?
What is the proper response for a NULL scan if the port is closed?
Which of the following Nmap commands would be used to perform a stack fingerprinting?
What is the following command used for?
net use \targetipc$ "" /u:""
While footprinting a network, what port/service should you look for to attempt a zone transfer?
What are the default passwords used by SNMP? (Choose two.)
Which one of the following is defined as the process of distributing incorrect Internet Protocol (IP) addresses/names with the intent of diverting traffic?
Which Windows system tool checks integrity of critical files that has been digitally signed by Microsoft?
Which of the following ICMP message types are used for destinations unreachables?
What information should an IT system analysis provide to the risk assessor?
An attacker uses a communication channel within an operating system that is neither designed nor intended to transfer information. What is the name of the communications channel?