Bob is going to perform an active session hijack against Brownies Inc. He has found a target that allows session oriented connections (Telnet) and performs the sequence prediction on the target operating system. He manages to find an active session due to the high level of traffic on the network. What is Bob supposed to do next?
In which step Steganography fits in CEH System Hacking Cycle (SHC)
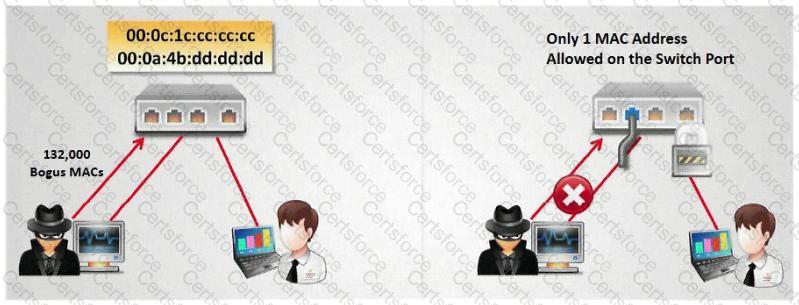
How do you defend against MAC attacks on a switch?