Under what conditions does a secondary name server request a zone transfer from a primary name server?
What tool can crack Windows SMB passwords simply by listening to network traffic?
Select the best answer.
A file integrity program such as Tripwire protects against Trojan horse attacks by:
Exhibit:
ettercap –NCLzs --quiet
What does the command in the exhibit do in “Ettercap”?
What did the following commands determine?
C: user2sid \earth guest
S-1-5-21-343818398-789336058-1343024091-501
C:sid2user 5 21 343818398 789336058 1343024091 500
Name is Joe
Domain is EARTH
Exhibit:
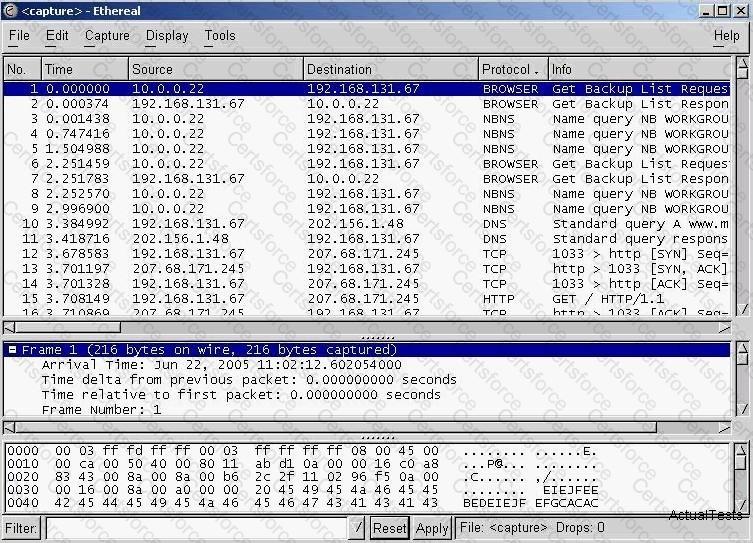
You have captured some packets in Ethereal. You want to view only packets sent from 10.0.0.22. What filter will you apply?
Which Open Web Application Security Project (OWASP) implements a web application full of known vulnerabilities?
An engineer is learning to write exploits in C++ and is using the exploit tool Backtrack. The engineer wants to compile the newest C++ exploit and name it calc.exe. Which command would the engineer use to accomplish this?
Windows file servers commonly hold sensitive files, databases, passwords and more. Which of the following choices would be a common vulnerability that usually exposes them?
What is the purpose of conducting security assessments on network resources?
After gaining access to the password hashes used to protect access to a web based application, knowledge of which cryptographic algorithms would be useful to gain access to the application?
How does an operating system protect the passwords used for account logins?
Which type of scan is used on the eye to measure the layer of blood vessels?
Which of the following guidelines or standards is associated with the credit card industry?
Which command lets a tester enumerate alive systems in a class C network via ICMP using native Windows tools?
How do employers protect assets with security policies pertaining to employee surveillance activities?
When analyzing the IDS logs, the system administrator noticed an alert was logged when the external router was accessed from the administrator's computer to update the router configuration. What type of an alert is this?
When creating a security program, which approach would be used if senior management is supporting and enforcing the security policy?
A computer technician is using a new version of a word processing software package when it is discovered that a special sequence of characters causes the entire computer to crash. The technician researches the bug and discovers that no one else experienced the problem. What is the appropriate next step?
Which of the following is a protocol that is prone to a man-in-the-middle (MITM) attack and maps a 32-bit address to a 48-bit address?