These hackers have limited or no training and know how to use only basic techniques or tools. What kind of hackers are we talking about?
During an Xmas scan, what indicates a port is closed?
which of the following protocols can be used to secure an LDAP service against anonymous queries?
This type of injection attack does not show any error message. It is difficult to exploit as it returns information when the application is given SQL payloads that elicit a true or false response from the server. By observing the response, an attacker can extract sensitive information. What type of attack is this?
To invisibly maintain access to a machine, an attacker utilizes a toolkit that sits undetected In the core components of the operating system. What is this type of rootkit an example of?
Which of the following LM hashes represent a password of less than 8 characters? (Choose two.)
A large enterprise has been experiencing sporadic system crashes and instability, resulting in limited access to its web services. The security team suspects it could be a result of a Denial of Service (DoS) attack. A significant increase in traffic was noticed in the network logs, with patterns suggesting packet sizes exceeding the prescribed size limit. Which among the following DoS attack techniques best describes this scenario?
in an attempt to increase the security of your network, you Implement a solution that will help keep your wireless network undiscoverable and accessible only to those that know It. How do you accomplish this?
An attacker scans a host with the below command. Which three flags are set?
# nmap -sX host.domain.com
Which of the following is considered an exploit framework and has the ability to perform automated attacks on services, ports, applications and unpatched security flaws in a computer system?
ViruXine.W32 virus hides its presence by changing the underlying executable code. This virus code mutates while keeping the original algorithm intact — the code changes itself each time it runs, but the function of the code (its semantics) does not change at all.
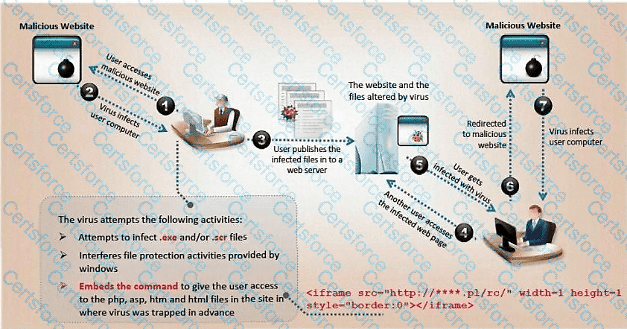
Here is a section of the virus code (refer to image), where the loop performs XOR encryption and changes the way the code looks every time it is executed.
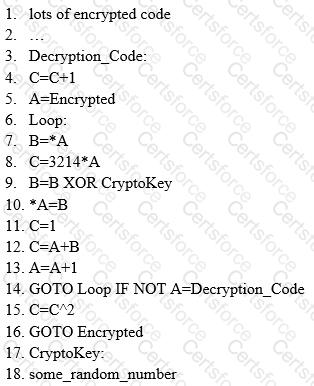
What is this technique called?
PGP, SSL, and IKE are all examples of which type of cryptography?
You are attempting to crack LM Manager hashes from a Windows 2000 SAM file. You will be using an LM brute-force hacking tool for decryption.
What encryption algorithm will you be decrypting?
What is the purpose of a demilitarized zone on a network?
A Certified Ethical Hacker (CEH) is given the task to perform an LDAP enumeration on a target system. The system is secured and accepts connections only on secure LDAP. The CEH uses Python for the enumeration process. After successfully installing LDAP and establishing a connection with the target, he attempts to fetch details like the domain name and naming context but is unable to receive the expected response. Considering the circumstances, which of the following is the most plausible reason for this situation?