Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice’s machine. From the command prompt, she types the following command:
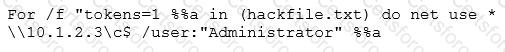 What is Eve trying to do?
What is Eve trying to do?
You are a Network Security Officer. You have two machines. The first machine (192.168.0.99) has Snort installed, and the second machine (192.168.0.150) has Kiwi Syslog installed. You perform a SYN scan in your network, and you notice that Kiwi Syslog is not receiving the alert message from Snort. You decide to run Wireshark on the Snort machine to check if the messages are going to the Kiwi Syslog machine. What Wireshark filter will show the connections from the Snort machine to Kiwi Syslog machine?
Bob wants to ensure that Alice can check whether his message has been tampered with. He creates a checksum of the message and encrypts it using asymmetric cryptography. What key does Bob use to encrypt the checksum for accomplishing this goal?
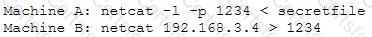
An attacker runs the netcat tool to transfer a secret file between two hosts.
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?
On performing a risk assessment, you need to determine the potential impacts when some of the critical business processes of the company interrupt its service.
What is the name of the process by which you can determine those critical businesses?
You are the lead cybersecurity analyst at a multinational corporation that uses a hybrid encryption system to secure inter-departmental communications. The system uses RSA encryption for key exchange and AES for data encryption, taking advantage of the strengths of both asymmetric and symmetric encryption. Each RSA key pair has a size of 'n' bits, with larger keys providing more security at the cost of slower performance. The
time complexity of generating an RSA key pair is O(n*2), and AES encryption has a time complexity of O(n). An attacker has developed a quantum algorithm with time complexity O((log n)*2) to crack RSA encryption. Given *n=4000' and variable ‘AES key size’, which scenario is likely to provide the best balance of security and
performance? which scenario would provide the best balance of security and performance?
Becky has been hired by a client from Dubai to perform a penetration test against one of their remote offices. Working from her location in Columbus, Ohio, Becky runs her usual reconnaissance scans to obtain basic information about their network. When analyzing the results of her Whois search, Becky notices that the IP was allocated to a location in Le Havre, France. Which regional Internet registry should Becky go to for detailed information?
In Trojan terminology, what is a covert channel?

Allen, a professional pen tester, was hired by xpertTech solutWns to perform an attack simul-ation on the organization's network resources. To perform the attack, he took advantage of the NetBIOS API and targeted the NetBIOS service. B/enumerating NetBIOS, he found that port 139 was open and could see the resources that could be accessed or viewed on a remote system. He came across many NetBIOS codes during enumeration.
identify the NetBIOS code used for obtaining the messenger service running for the logged-in user?
Attacker Rony Installed a rogue access point within an organization's perimeter and attempted to Intrude into its internal network. Johnson, a security auditor, identified some unusual traffic in the internal network that is aimed at cracking the authentication mechanism. He immediately turned off the targeted network and tested for any weak and outdated security mechanisms that are open to attack. What is the type of vulnerability assessment performed by Johnson in the above scenario?
A large mobile telephony and data network operator has a data center that houses network elements. These are essentially large computers running on Linux. The perimeter of the data center is secured with firewalls and IPS systems.
What is the best security policy concerning this setup?
What does the –oX flag do in an Nmap scan?
An attacker decided to crack the passwords used by industrial control systems. In this process, he employed a loop strategy to recover these passwords. He used one character at a time to check whether the first character entered is correct; if so, he continued the loop for consecutive characters. If not, he terminated the loop. Furthermore, the attacker checked how much time the device took to finish one complete password authentication process, through which he deduced how many characters entered are correct.
What is the attack technique employed by the attacker to crack the passwords of the industrial control systems?
Attempting an injection attack on a web server based on responses to True/False QUESTION NO:s is called which of the following?
Your company was hired by a small healthcare provider to perform a technical assessment on the network.
What is the best approach for discovering vulnerabilities on a Windows-based computer?