A penetration tester runs the following command on a system:
find / -user root –perm -4000 –print 2>/dev/null
Which of the following is the tester trying to accomplish?
Given the following output:
User-agent:*
Disallow: /author/
Disallow: /xmlrpc.php
Disallow: /wp-admin
Disallow: /page/
During which of the following activities was this output MOST likely obtained?
Which of the following would MOST likely be included in the final report of a static application-security test that was written with a team of application developers as the intended audience?
Which of the following web-application security risks are part of the OWASP Top 10 v2017? (Choose two.)
A penetration tester has gained access to part of an internal network and wants to exploit on a different network segment. Using Scapy, the tester runs the following command:
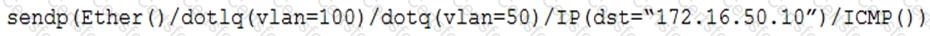
Which of the following represents what the penetration tester is attempting to accomplish?
A penetration tester ran the following command on a staging server:
python –m SimpleHTTPServer 9891
Which of the following commands could be used to download a file named exploit to a target machine for execution?
In an unprotected network file repository, a penetration tester discovers a text file containing usernames and passwords in cleartext and a spreadsheet containing data for 50 employees, including full names, roles, and serial numbers. The tester realizes some of the passwords in the text file follow the format:
A penetration tester wants to test a list of common passwords against the SSH daemon on a network device. Which of the following tools would be BEST to use for this purpose?
Which of the following should a penetration tester do NEXT after identifying that an application being tested has already been compromised with malware?
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified. Which of the following character combinations should be used on the first line of the script to accomplish this goal?