PCI DSS requires which of the following as part of the penetration-testing process?
Which of the following tools provides Python classes for interacting with network protocols?
The following PowerShell snippet was extracted from a log of an attacker machine:
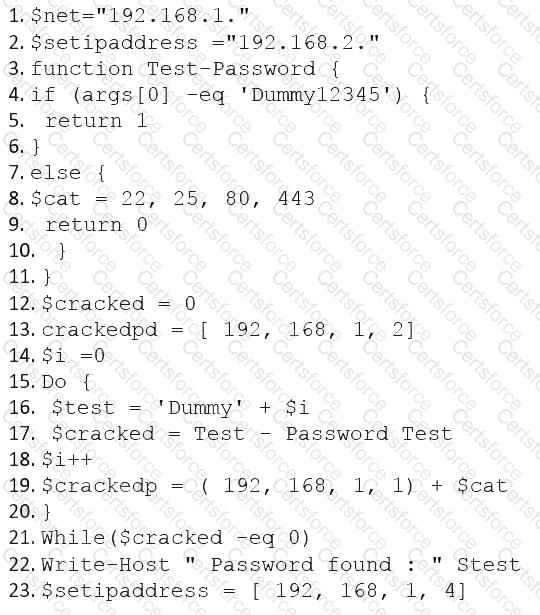
A penetration tester would like to identify the presence of an array. Which of the following line numbers would define the array?
Which of the following tools would BEST allow a penetration tester to capture wireless handshakes to reveal a Wi-Fi password from a Windows machine?
Which of the following is a rules engine for managing public cloud accounts and resources?
During a penetration test, a tester is in close proximity to a corporate mobile device belonging to a network administrator that is broadcasting Bluetooth frames.
Which of the following is an example of a Bluesnarfing attack that the penetration tester can perform?
Which of the following is the MOST important information to have on a penetration testing report that is written for the developers?
A penetration tester downloaded the following Perl script that can be used to identify vulnerabilities in network switches. However, the script is not working properly.
Which of the following changes should the tester apply to make the script work as intended?
Which of the following BEST explains why a penetration tester cannot scan a server that was previously scanned successfully?
A penetration tester was able to compromise a server and escalate privileges. Which of the following should the tester perform AFTER concluding the activities on the specified target? (Choose two.)