SIMULATION
Using the output, identify potential attack vectors that should be further investigated.
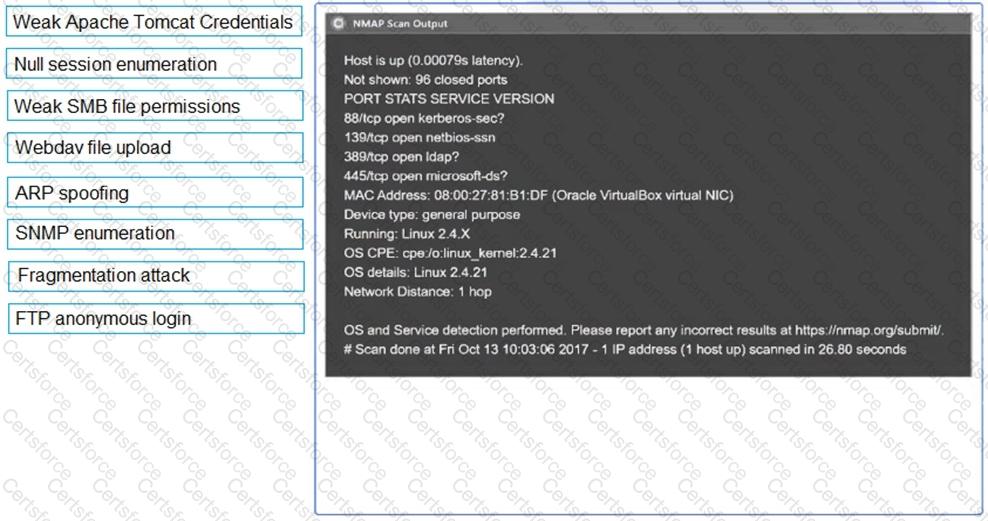
A Chief Information Security Officer wants a penetration tester to evaluate whether a recently installed firewall is protecting a subnetwork on which many decades- old legacy systems are connected. The penetration tester decides to run an OS discovery and a full port scan to identify all the systems and any potential vulnerability. Which of the following should the penetration tester consider BEFORE running a scan?
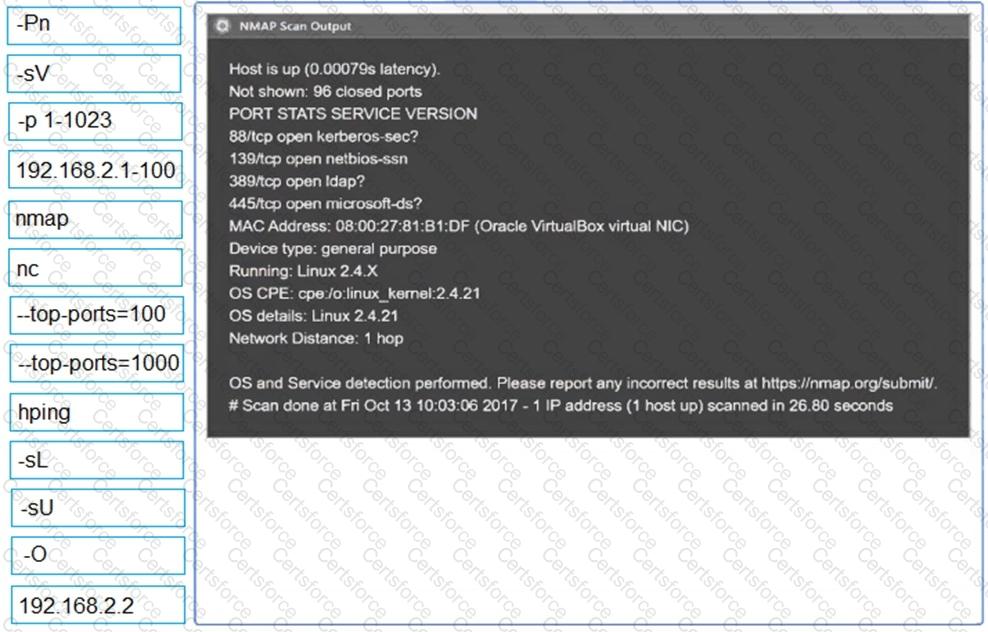
After compromising a system, a penetration tester wants more information in order to decide what actions to take next. The tester runs the following commands:
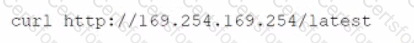
Which of the following attacks is the penetration tester most likely trying to perform?
A company requires that all hypervisors have the latest available patches installed. Which of the following would BEST explain the reason why this policy is in place?
Which of the following concepts defines the specific set of steps and approaches that are conducted during a penetration test?
A penetration tester is conducting an authorized, physical penetration test to attempt to enter a client's building during non-business hours. Which of the following are MOST important for the penetration tester to have during the test? (Choose two.)
A penetration tester is able to use a command injection vulnerability in a web application to get a reverse shell on a system After running a few commands, the tester runs the following:
python -c 'import pty; pty.spawn("/bin/bash")'
Which of the following actions Is the penetration tester performing?
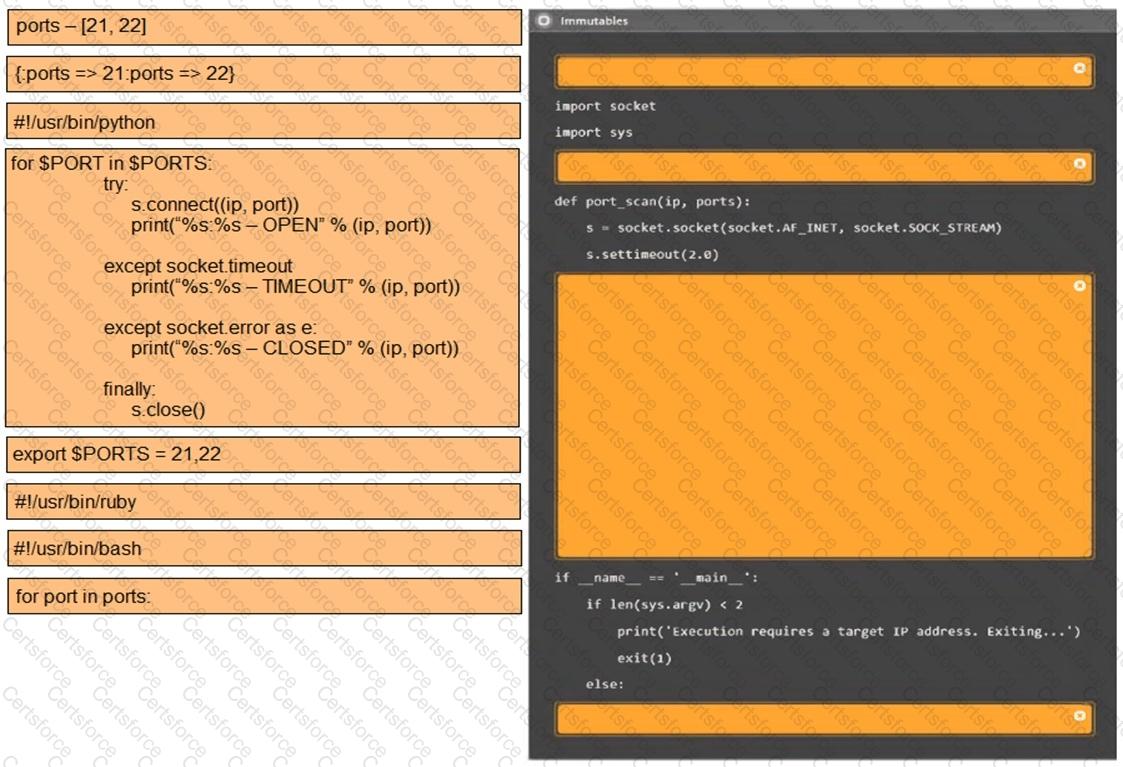
A penetration tester writes the following script:
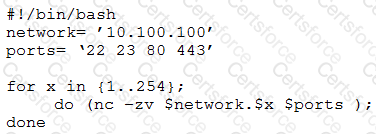
Which of the following is the tester performing?
Which of the following is a regulatory compliance standard that focuses on user privacy by implementing the right to be forgotten?
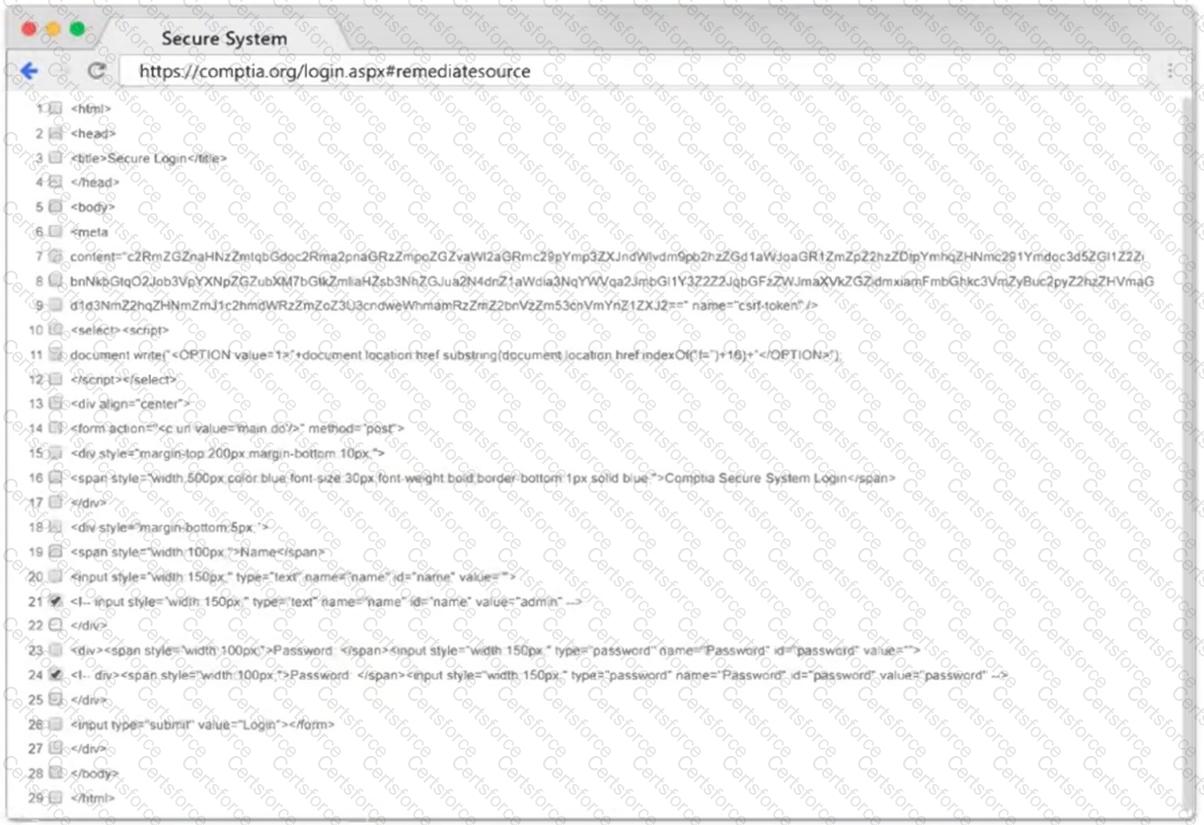
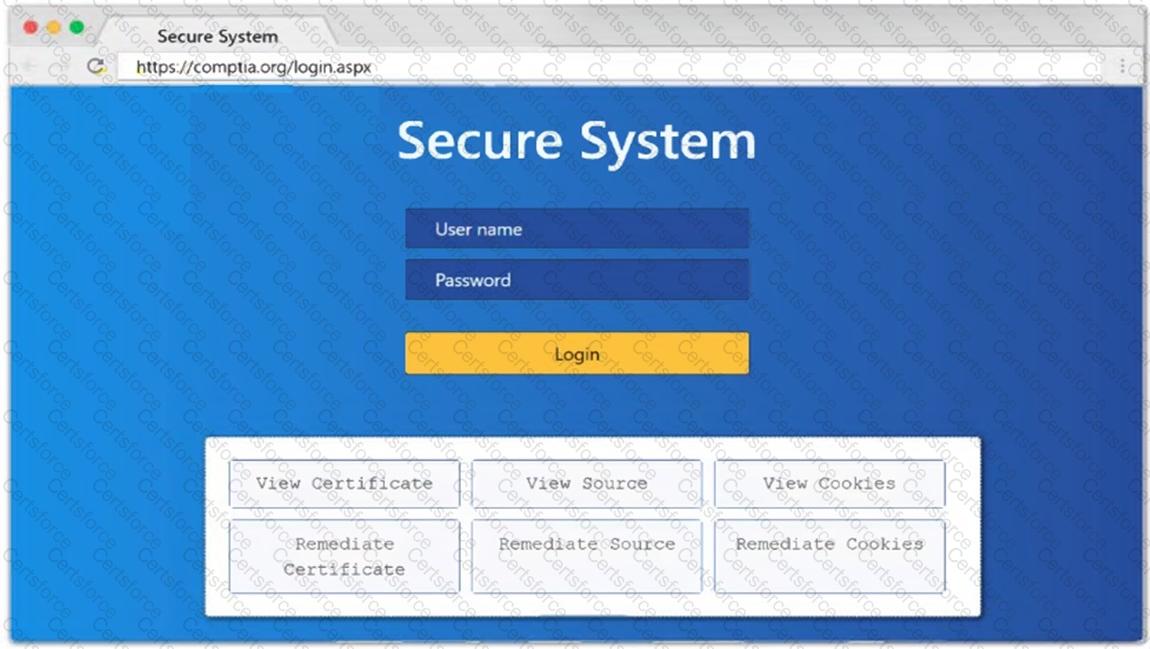
Company.com has hired a penetration tester to conduct a phishing test. The tester wants to set up a fake log-in page and harvest credentials when target employees click on links in a phishing email. Which of the following commands would best help the tester determine which cloud email provider the log-in page needs to mimic?