An analyst is examining events in multiple systems but is having difficulty correlating data points. Which of the following is most likely the issue with the system?
A security analyst is trying to validate the results of a web application scan with Burp Suite. The security analyst performs the following:
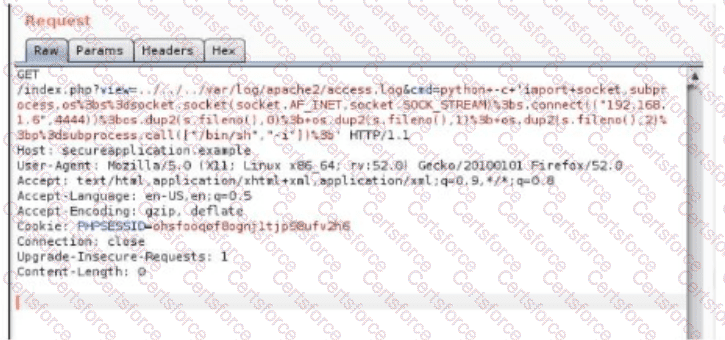
Which of the following vulnerabilitles Is the securlty analyst trylng to valldate?
Which of the following concepts is using an API to insert bulk access requests from a file into an identity management system an example of?
An organization needs to bring in data collection and aggregation from various endpoints. Which of the following is the best tool to deploy to help analysts gather this data?
A security analyst discovers an LFI vulnerability that can be exploited to extract credentials from the underlying host. Which of the following patterns can the security analyst use to search the web server
logs for evidence of exploitation of that particular vulnerability?
During an incident, an analyst needs to acquire evidence for later investigation. Which of the following must be collected first in a computer system, related to its volatility level?
A company is implementing a vulnerability management program and moving from an on-premises environment to a hybrid IaaS cloud environment. Which of the following implications should be considered on the new hybrid environment?
During a security test, a security analyst found a critical application with a buffer overflow vulnerability. Which of the following would be best to mitigate the vulnerability at the application level?
A security analyst received a malicious binary file to analyze. Which of the following is the best technique to perform the analysis?
A security analyst receives the below information about the company's systems. They need to prioritize which systems should be given the resources to improve security.
Host
OS
Key Software
AV
Server 1
Windows Server 2008 R2
Microsoft IIS
Kaspersky
Server 2
Ubuntu Server 22.04 LTS
Apache 2.4.29
None
Computer 1
Windows 11 Professional
N/A
Windows Defender
Computer 2
Windows 10 Professional
N/A
Windows Defender
Which of the following systems should the analyst remediate first?