Application development team users are having issues accessing the database server within the cloud environment. All other users are able to use SSH to access this server without issues. The network architect reviews the following information to troubleshoot the issue:
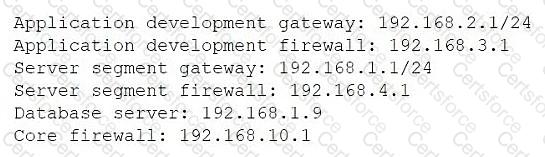
Traceroute output from an application developer's machine with the assigned IP 192.168.2.7:
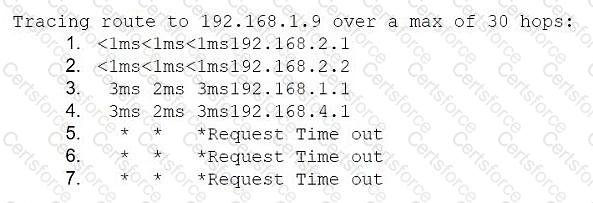
Application development gateway: 192.168.2.1/24
Server segment gateway: 192.168.1.1/24
Database server: 192.168.1.9
Application developer machine IP: 192.168.2.7
Traceroute ends at hop 4: 192.168.4.1 (server segment firewall), then times out
Which of the following is the most likely cause of the issue?
A network architect is designing a new network for a rural hospital system. Given the following requirements:
Highly available
Consistent data transmission
Resilient to simultaneous failures
Which of the following topologies should the architect use?
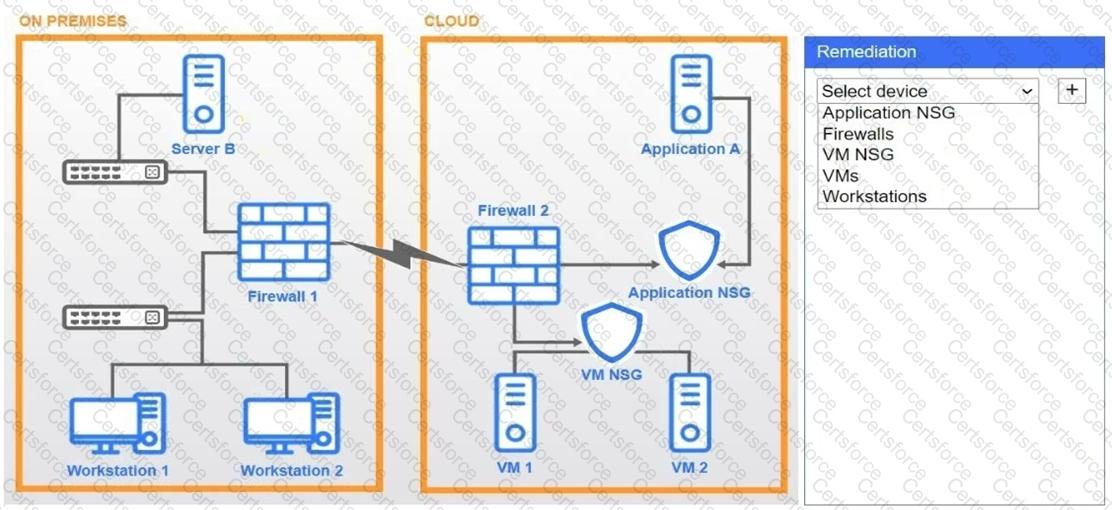
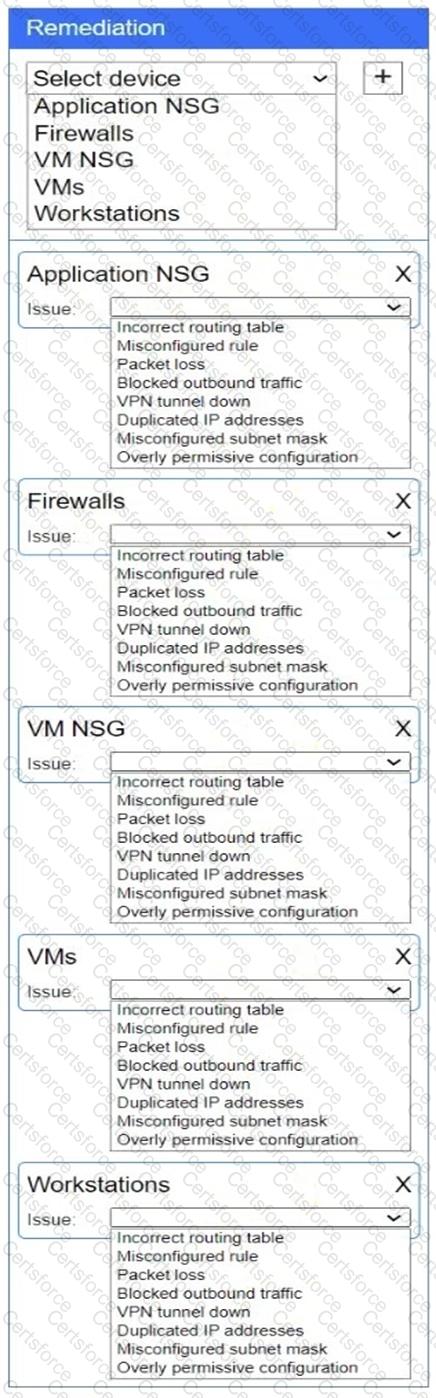
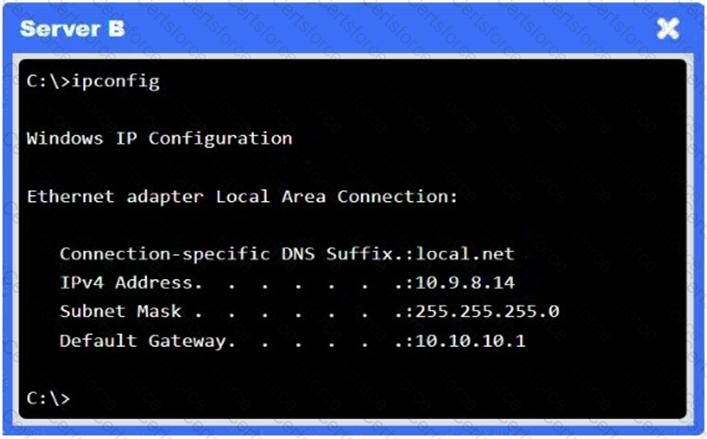
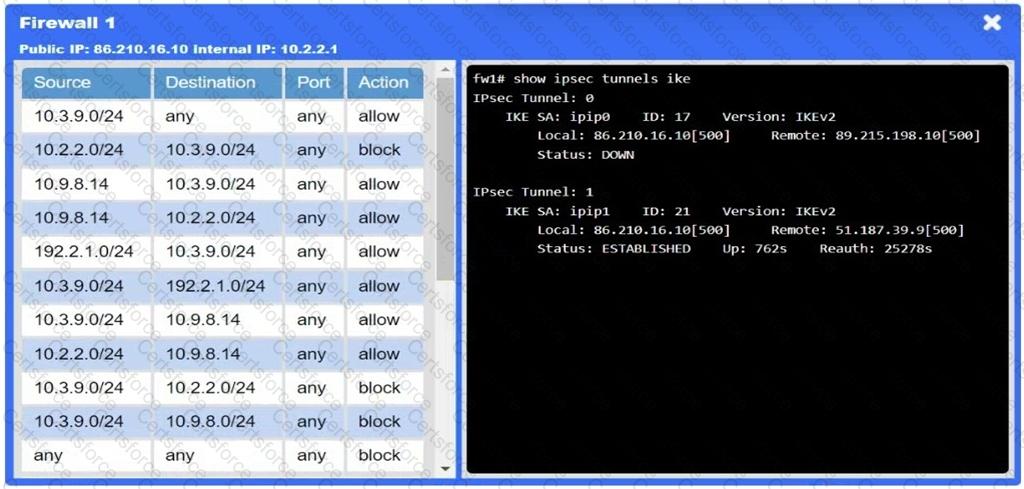
A network administrator needs to resolve connectivity issues in a hybrid cloud setup. Workstations and VMs are not able to access Application A. Workstations are able to access Server B.
INSTRUCTIONS
Click on workstations, VMs, firewalls, and NSGs to troubleshoot and gather information. Type help in the terminal to view a list of available commands.
Select the appropriate device(s) requiring remediation and identify the associated issue(s).
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
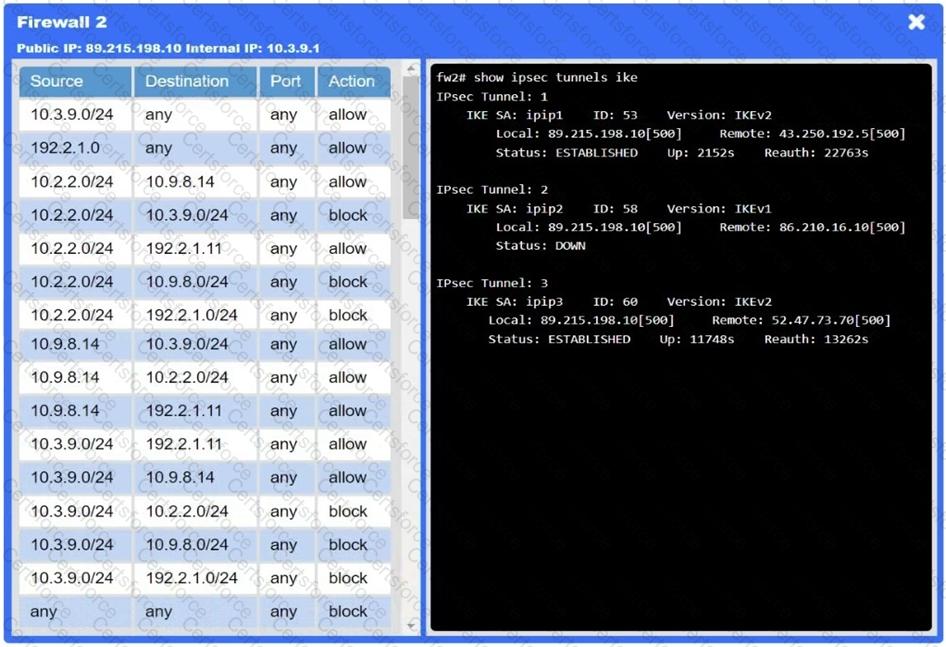
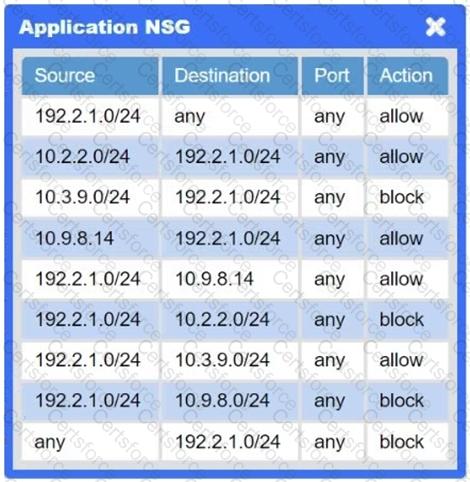
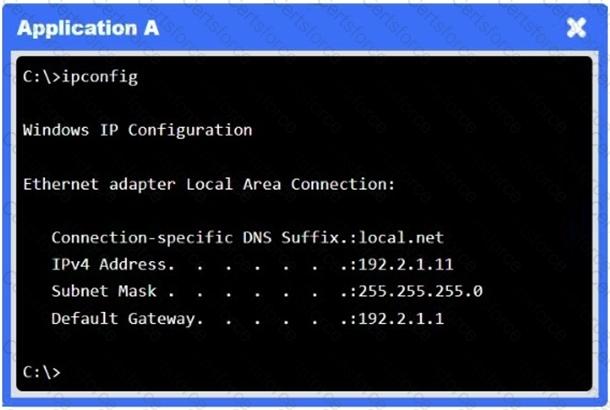
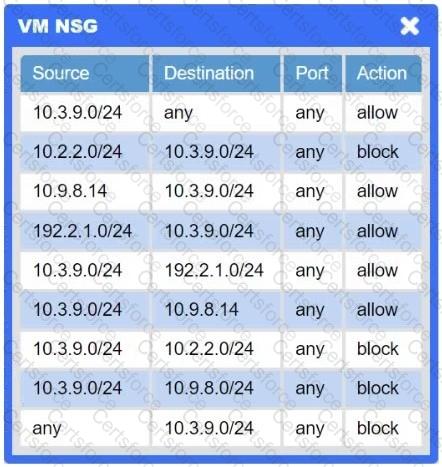


A company deployed new applications in the cloud and configured a site-to-site VPN to connect the internal data center with the cloud. The IT team wants the internal servers to connect to those applications without using public IP addresses. Which of the following is the best solution?
Security policy states that all inbound traffic to the environment needs to be restricted, but all external outbound traffic is allowed within the hybrid cloud environment. A new application server was recently set up in the cloud. Which of the following would most likely need to be configured so that the server has the appropriate access set up? (Choose two.)
A company hosts its applications on the cloud and is expanding its business to Europe. Thecompany must comply with General Data Protection Regulation (GDPR) to limit European customers' access to data. The network team configures the firewall rules but finds that some customers in the United States can access data hosted in Europe. Which of the following is the best option for the network team to configure?
A company is experiencing multiple switch failures. The network analyst discovers the following:
Network recovery time is unacceptable and occurs after the shutdown of some switches.
Some loops were detected in the network.
No broadcast storm was detected.
Which of the following is the most cost-effective solution?
A company provides an API that runs on the public cloud for its customers. A fixed number of VMs host the APIs. During peak hours, the company notices a spike in usage that results in network communication speeds slowing down for all customers. The management team has decided that access for all customers should be fair and accessible at all times. Which of the following is the most cost-effective way to address this issue?
An administrator must ensure that credit card numbers are not contained in any outside messaging or file transfers from the organization. Which of the following controls meets this requirement?
A call center company provides its services through a VoIP infrastructure. Recently, the call center set up an application to manage its documents on a cloud application. The application is causing recurring audio losses for VoIP callers. The network administrator needs to fix the issue with the least expensive solution. Which of the following is the best approach?