A network engineer identified several failed log-in attempts to the VPN from a user's account. When the engineer inquired, the user mentioned the IT help desk called and asked them to change their password. Which of the following types of attacks occurred?
A network architect is working on a physical network design template for a small education institution's satellite campus that is not yet built. The new campus location will consist of two small buildings with classrooms, one screening room with audiovisual equipment, and 200 seats for students. Which of the following enterprise network designs should the architect suggest?
A network architect is working on a new network design to better support remote and on-campus workers. Traffic needs to be decrypted for inspection in the cloud but is not required to go through the company's data center. Which of the following technologies best meets these requirements?
A global company has depots in various locations. A proprietary application was deployed locally at each of the depots, but issues with getting the consolidated data instantly occurred. The Chief Information Officer decided to centralize the application and deploy it in the cloud. After the cloud deployment, users report the application is slow. Which of the following is most likely the issue?
Which of the following helps the security of the network design to align with industry best practices?
A network security engineer must secure a web application running on virtual machines in a public cloud. The virtual machines are behind an application load balancer. Which of the following technologies should the engineer use to secure the virtual machines? (Choose two.)
An outage occurred after a software upgrade on core switching. A network administrator thinks that the firmware installed had a bug. Which of the following should the network administrator do next?
A network architect is designing a solution to place network core equipment in a rack inside a data center. This equipment is crucial to the enterprise and must be as secure as possible to minimize the chance that anyone could connect directly to the network core. The current security setup is:
In a locked building that requires sign in with a guard and identification check.
In a locked data center accessible by a proximity badge and fingerprint scanner.
In a locked cabinet that requires the security guard to call the Chief Information Security Officer (CISO) to get permission to provide the key.
Which of the following additional measures should the architect recommend to make this equipment more secure?
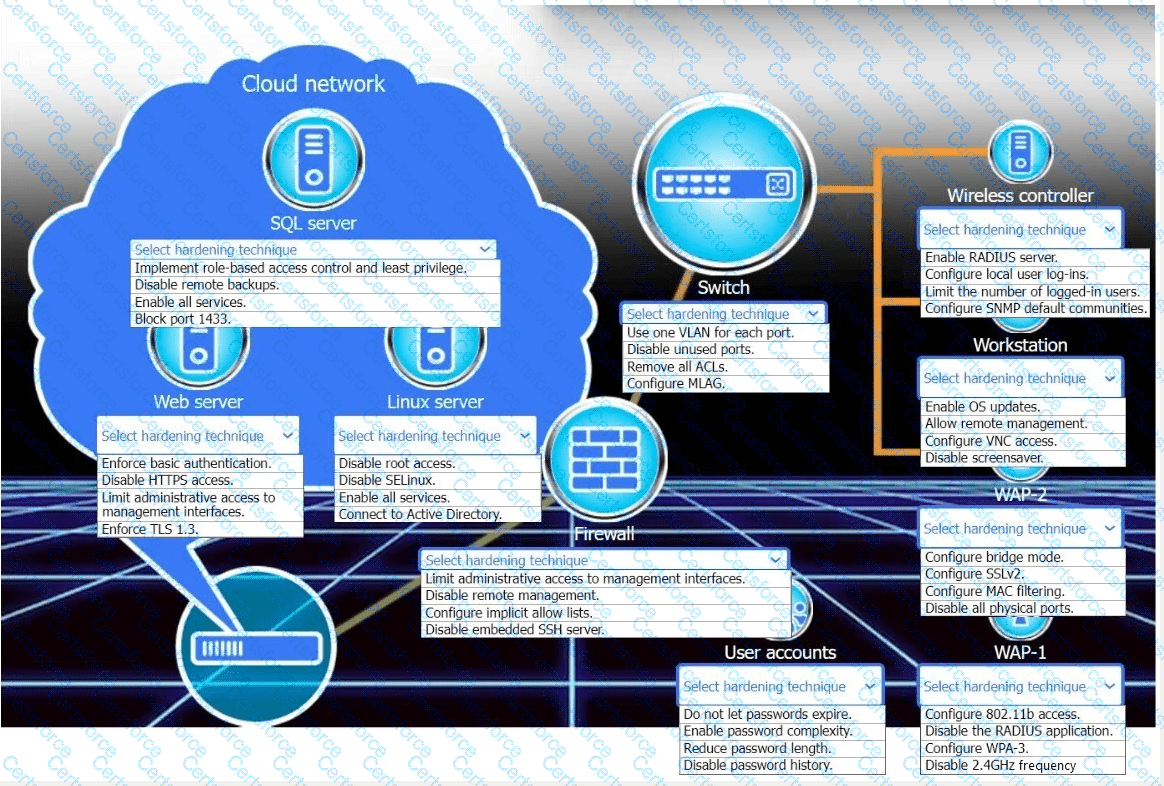
New devices were deployed on a network and need to be hardened.
INSTRUCTIONS
Use the drop-down menus to define the appliance-hardening techniques that provide themostsecure solution.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A SaaS company's new service currently is being provided through four servers. The company's end users are having connection issues, which is affecting about 25% of the connections. Which of the following is most likely the root cause of this issue?