During a network defense engagement, a red team is able to edit the following registry key:
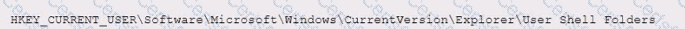
Which of the following tools is the red team using to perform this action?
A network administrator who manages a Linux web server notices the following traffic:
http://corr.ptia.org/.../.../.../... /etc./shadow
Which of the following Is the BEST action for the network administrator to take to defend against this type of web attack?
A security administrator wants to enable a feature that would prevent a compromised encryption key from being used to decrypt all the VPN traffic. Which of the following should the security administrator use?
A security engineer is creating a single CSR for the following web server hostnames:
• wwwint internal
• www company com
• home.internal
• www internal
Which of the following would meet the requirement?
A company that provides services to clients who work with highly sensitive data would like to provide assurance that the data’s confidentiality is maintained in a dynamic, low-risk environment. Which of the following would best achieve this goal? (Select two).
Signed applications reduce risks by:
A Chief Information Security Officer is concerned about the condition of the code security being used for web applications. It is important to get the review right the first time, and the company is willing to use a tool that will allow developers to validate code as it is written. Which of the following methods should the company use?
Which of the following should an organization implement to prevent unauthorized API key sharing?
A security analyst is examining a former employee's laptop for suspected evidence of suspicious activity. The analyst usesddduring the investigation. Which of the following best explains why the analyst is using this tool?
A company is developing a new service product offering that will involve the storage of personal health information. The Chief Information Security Officer (CISO) is researching the relevant compliance regulations. Which of the following best describes the CISO's action?
A control systems analyst is reviewing the defensive posture of engineering workstations on the shop floor. Upon evaluation, the analyst makes the following observations:
• Unsupported, end-of-life operating systems were still prevalent on the shop floor.
• There are no security controls for systems with supported operating systems.
• There is little uniformity of installed software among the workstations.
Which of the following would have the greatest impact on the attack surface?
When managing and mitigating SaaS cloud vendor risk, which of the following responsibilities belongs to the client?
To bring digital evidence in a court of law the evidence must be:
A forensic investigator started the process of gathering evidence on a laptop in response to an incident The investigator took a snapshof of the hard drive, copied relevant log files and then performed a memory dump Which of the following steps in the process should have occurred first?
A security administrator needs to implement a security solution that will
• Limit the attack surface in case of an incident
• Improve access control for external and internal network security.
• Improve performance with less congestion on network traffic
Which of the following should the security administrator do?