An organization is preparing to migrate its production environment systems from an on-premises environment to a cloud service. The lead security architect is concerned that the organization's current methods for addressing risk may not be possible in the cloud environment.
Which of the following BEST describes the reason why traditional methods of addressing risk may not be possible in the cloud?
A vulnerability analyst identified a zero-day vulnerability in a company’s internally developed software. Since the current vulnerability management system does not have any checks for this vulnerability, an engineer has been asked to create one.
Which of the following would be BEST suited to meet these requirements?
A security engineer needs to recommend a solution that will meet the following requirements:
Identify sensitive data in the provider’s network
Maintain compliance with company and regulatory guidelines
Detect and respond to insider threats, privileged user threats, and compromised accounts
Enforce datacentric security, such as encryption, tokenization, and access control
Which of the following solutions should the security engineer recommend to address these requirements?
A technician is reviewing the logs and notices a large number of files were transferred to remote sites over the course of three months. This activity then stopped. The files were transferred via TLS-protected HTTP sessions from systems that do not send traffic to those sites.
The technician will define this threat as:
After investigating a recent security incident, a SOC analyst is charged with creating a reference guide for the entire team to use. Which of the following should the analyst create to address future incidents?
Which of the following technologies would need to be in an unmanaged state to perform forensic analysis on a laptop with an unknown encryption key?
An employee's device was missing for 96 hours before being reported. The employee called the help desk to ask for another device Which of the following phases of the incident response cycle needs improvement?
Which of the following is the reason why security engineers often cannot upgrade the security of embedded facility automation systems?
A security analyst is reviewing the following output from a vulnerability scan from an organization's internet-facing web services:
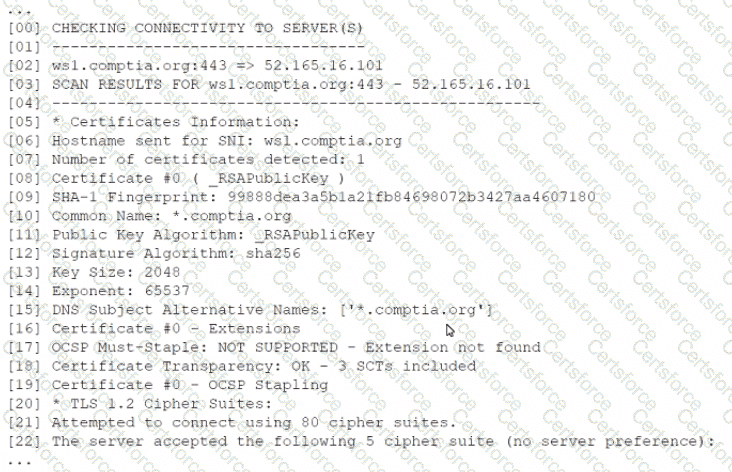
Which of the following indicates a susceptibility whereby an attacker can take advantage of the trust relationship between the client and the server?
An analyst reviews the following output collected during the execution of a web application security assessment:
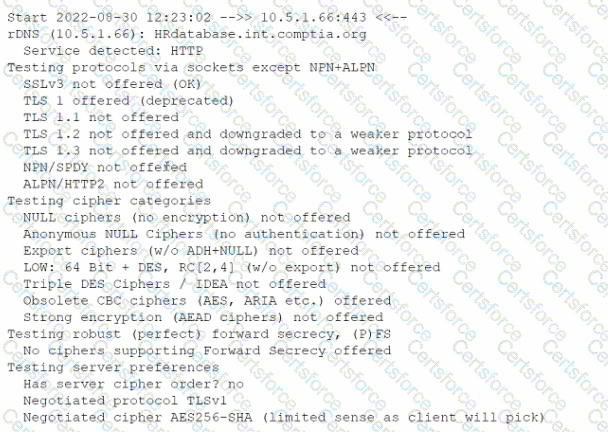
Which of the following attacks would be most likely to succeed, given the output?
The information security manager at a 24-hour manufacturing facility is reviewing a contract for potential risks to the organization. The contract pertains to the support of printers and multifunction devices during non-standard business hours. Which of the following will the security manager most likely identify as a risk?
A security technician is investigating a system that tracks inventory via a batch update each night. The technician is concerned that the system poses a risk to the business, as errors are occasionally generated and reported inventory appears incorrect. The following output log is provided:
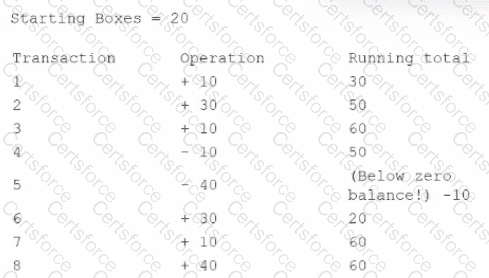
The technician reviews the output of the batch job and discovers that the inventory was never less than zero, and the final inventory was 100 rather than 60. Which of the following should the technician do to resolve this issue?
An IT director is working on a solution to meet the challenge of remotely managing laptop devices and securely locking them down. The solution must meet the following requirements:
• Cut down on patch management.
• Make use of standard configurations.
• Allow for custom resource configurations.
• Provide access to the enterprise system from multiple types of devices.
Which of the following would meet these requirements?
A company wants to use a process to embed a sign of ownership covertly inside a proprietary document without adding any identifying attributes. Which of the following would be best to use as part of the process to support copyright protections of the document?
An organization performed a risk assessment and discovered that less than 50% of its employees have been completing security awareness training. Which of the following should the ChiefInformation Security Officer highlight as an area of Increased vulnerability in a report to the management team?