A network administrator for a completely air-gapped and closed system has noticed that anomalous external files have been uploaded to one of the critical servers. The administrator has reviewed logs
in the SIEM that were collected from security appliances, network infrastructure devices, and endpoints. Which of the following processes, if executed, would be MOST likely to expose an attacker?
Which of the following indicates when a company might not be viable after a disaster?
An organization is in frequent litigation and has a large number of legal holds. Which of the following types of functionality should the organization's new email system provide?
A security analyst runs a vulnerability scan on a network administrator's workstation The network administrator has direct administrative access to the company's SSO web portal The vulnerability scan uncovers cntical vulnerabilities with equally high CVSS scores for the user's browser, OS, email client and an offline password manager Which of the following should the security analyst patch FIRST?
Which of the following processes involves searching and collecting evidence during an investigation or lawsuit?
A security engineer has been informed by the firewall team that a specific Windows workstation is part of a command-and-control network. The only information the security engineer is receiving is that
the traffic is occurring on a non-standard port (TCP 40322). Which of the following commands should the security engineer use FIRST to find the malicious process?
A security architect Is analyzing an old application that is not covered for maintenance anymore because the software company is no longer in business. Which of the following techniques should have been Implemented to prevent these types of risks?
A security administrator wants to detect a potential forged sender claim in tt-e envelope of an email. Which of the following should the security administrator implement? (Select TWO).
A security analyst for a managed service provider wants to implement the most up-to-date and effective security methodologies to provide clients with the best offerings. Which of the following resources
would the analyst MOST likely adopt?
A security consultant has been asked to identify a simple, secure solution for a small business with a single access point. The solution should have a single SSID and no guest access. The customer
facility is located in a crowded area of town, so there is a high likelihood that several people will come into range every day. The customer has asked that the solution require low administrative overhead
and be resistant to offline password attacks. Which of the following should the security consultant recommend?
Due to internal resource constraints, the management team has asked the principal security architect to recommend a solution that shifts most of the responsibility for application-level controls to the cloud provider. In the shared responsibility model, which of the following levels of service meets this requirement?
A security engineer is implementing a server-side TLS configuration that provides forward secrecy and authenticated encryption with associated data. Which of the following algorithms, when combined into a cipher suite, will meet these requirements? (Choose three.)
A new, online file hosting service is being offered. The service has the following security requirements:
• Threats to customer data integrity and availability should be remediated first.
• The environment should be dynamic to match increasing customer demands.
• The solution should not interfere with customers" ability to access their data at anytime.
• Security analysts should focus on high-risk items.
Which of the following would BEST satisfy the requirements?
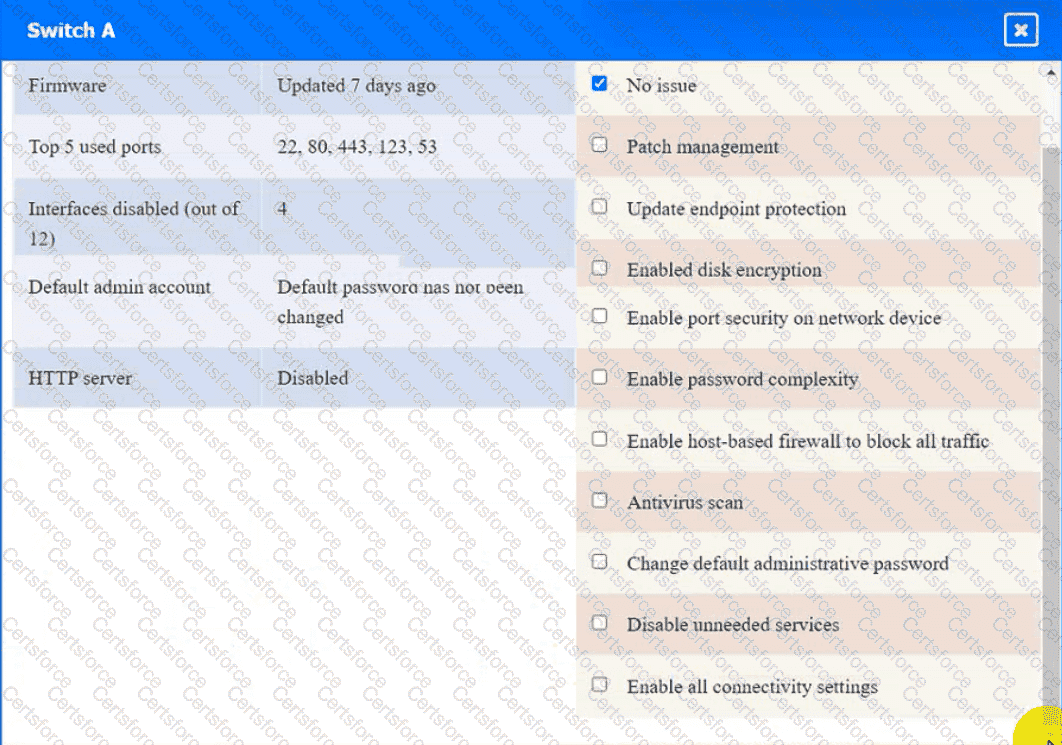
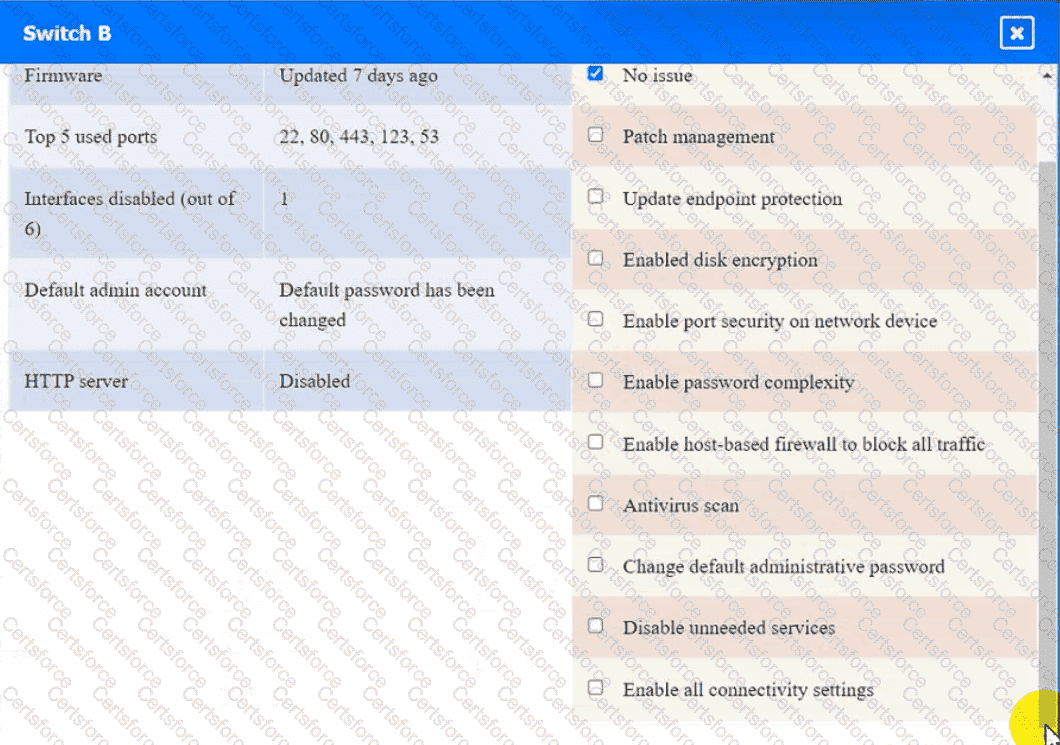
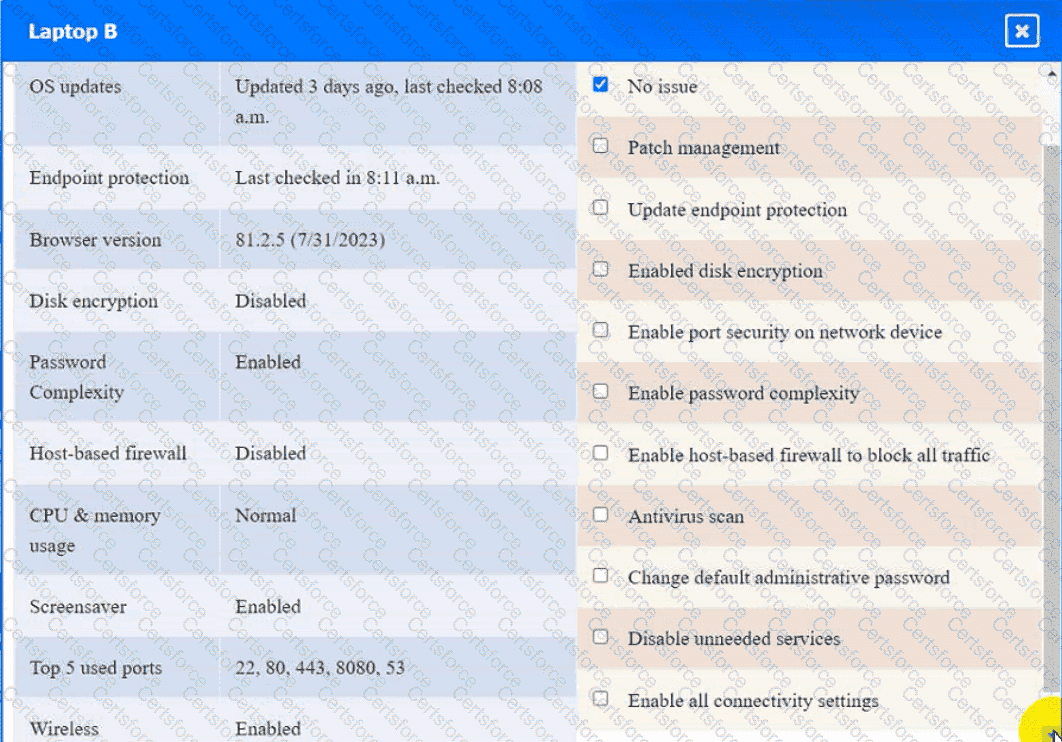
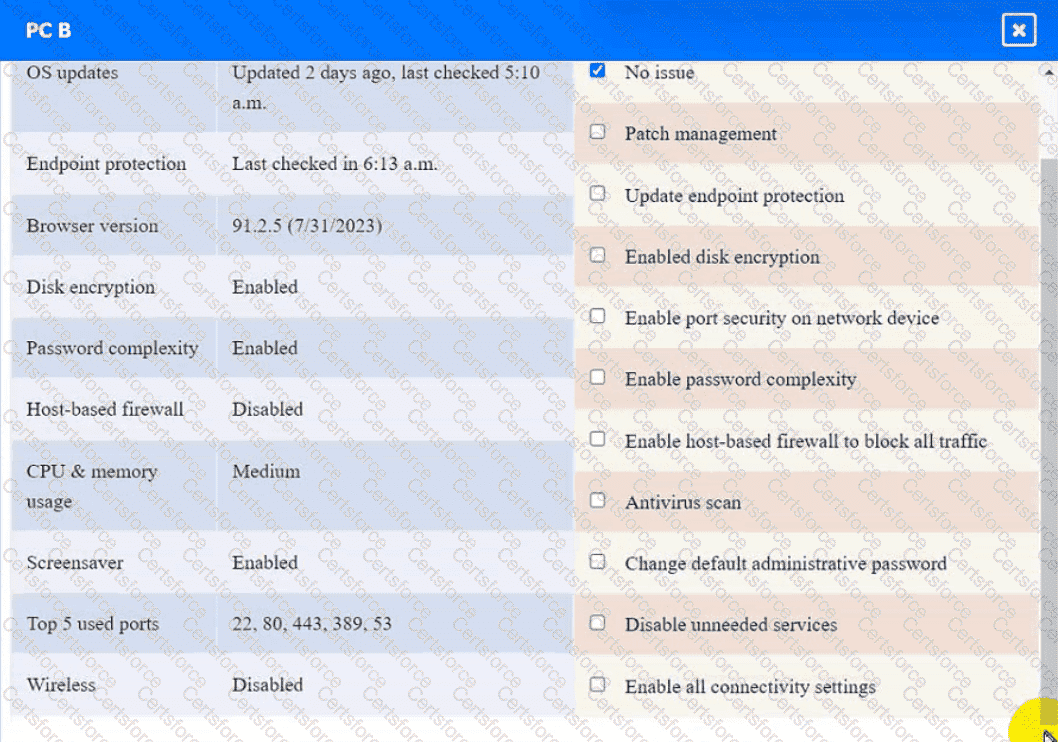
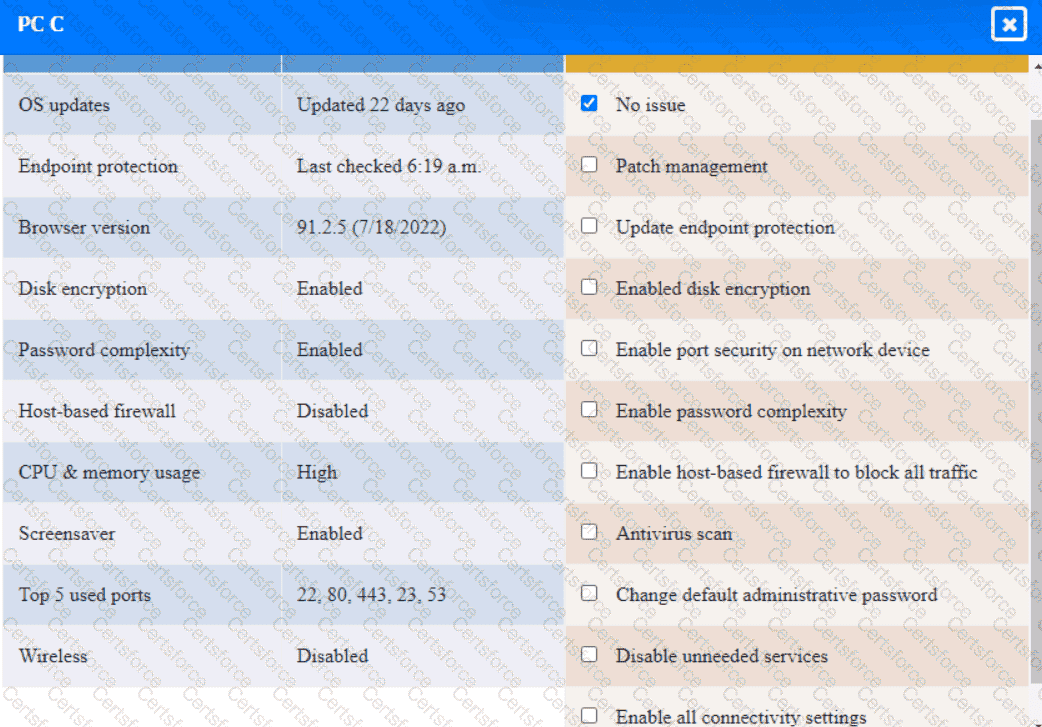
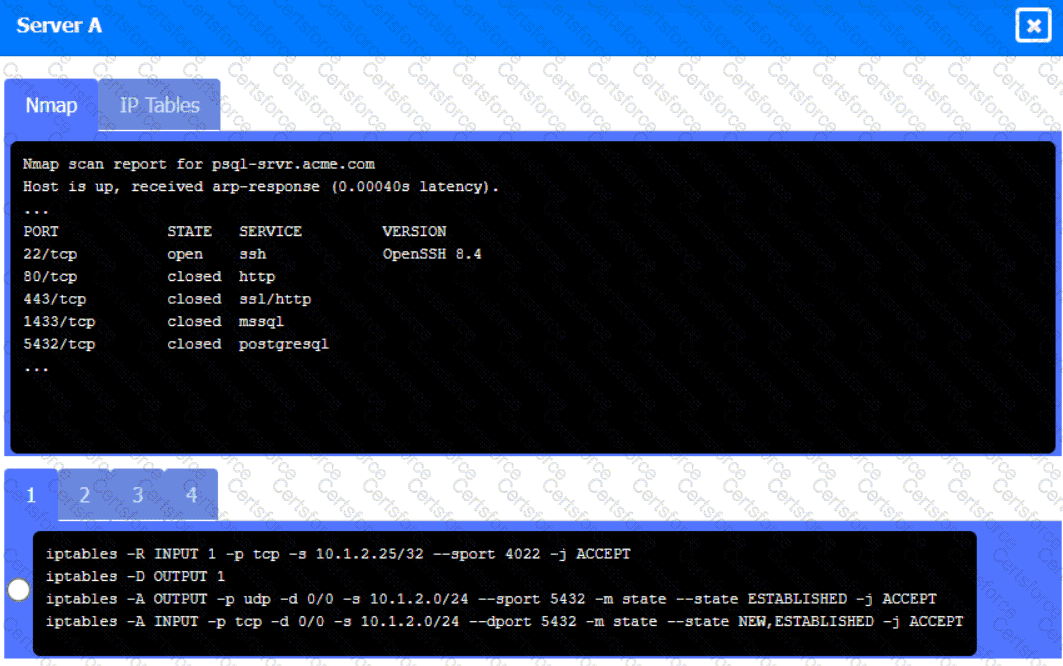
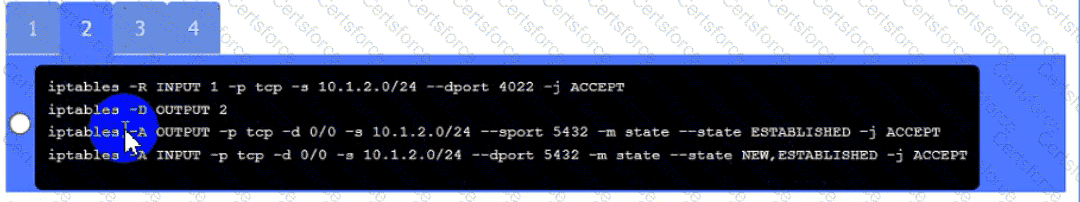
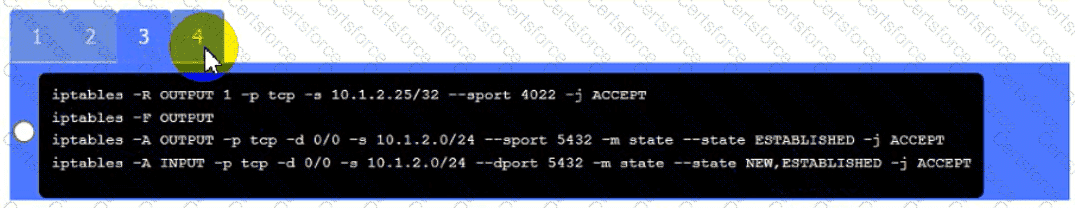
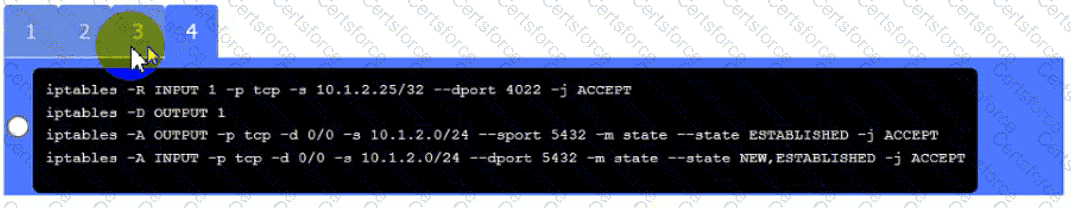
A security engineer needs to review the configurations of several devices on the network to meet the following requirements:
• The PostgreSQL server must only allow connectivity in the 10.1.2.0/24
subnet.
• The SSH daemon on the database server must be configured to listen
to port 4022.
• The SSH daemon must only accept connections from a Single
workstation.
• All host-based firewalls must be disabled on all workstations.
• All devices must have the latest updates from within the past eight
days.
• All HDDs must be configured to secure data at rest.
• Cleartext services are not allowed.
• All devices must be hardened when possible.
Instructions:
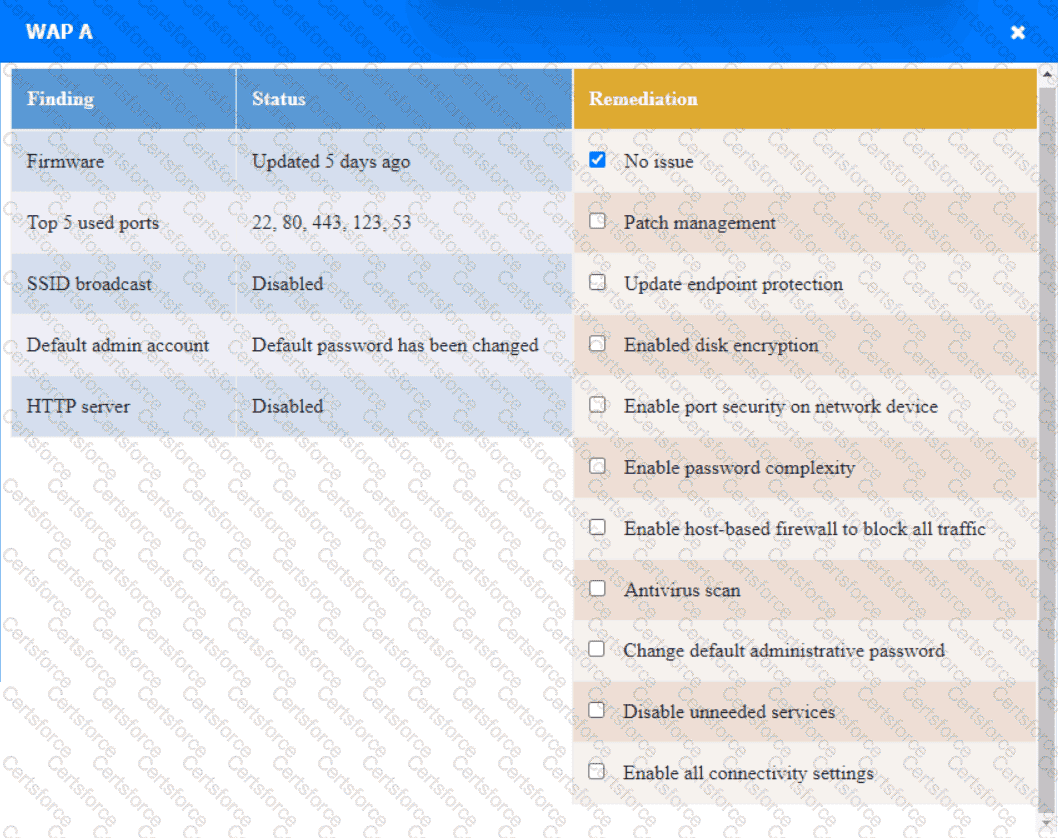
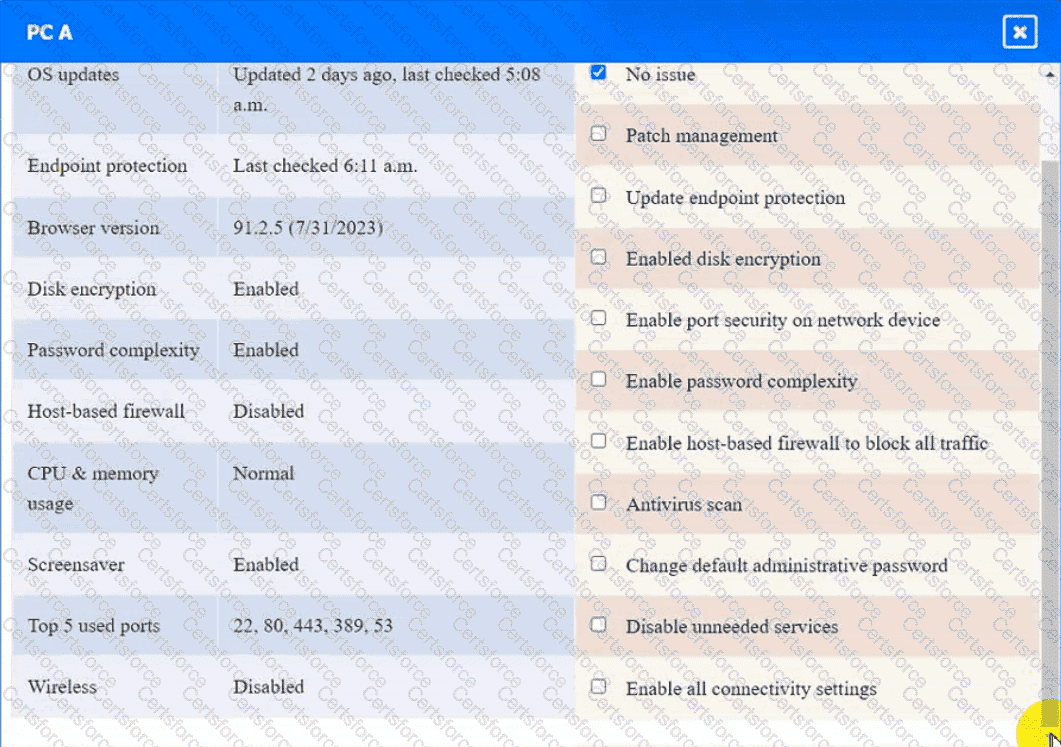
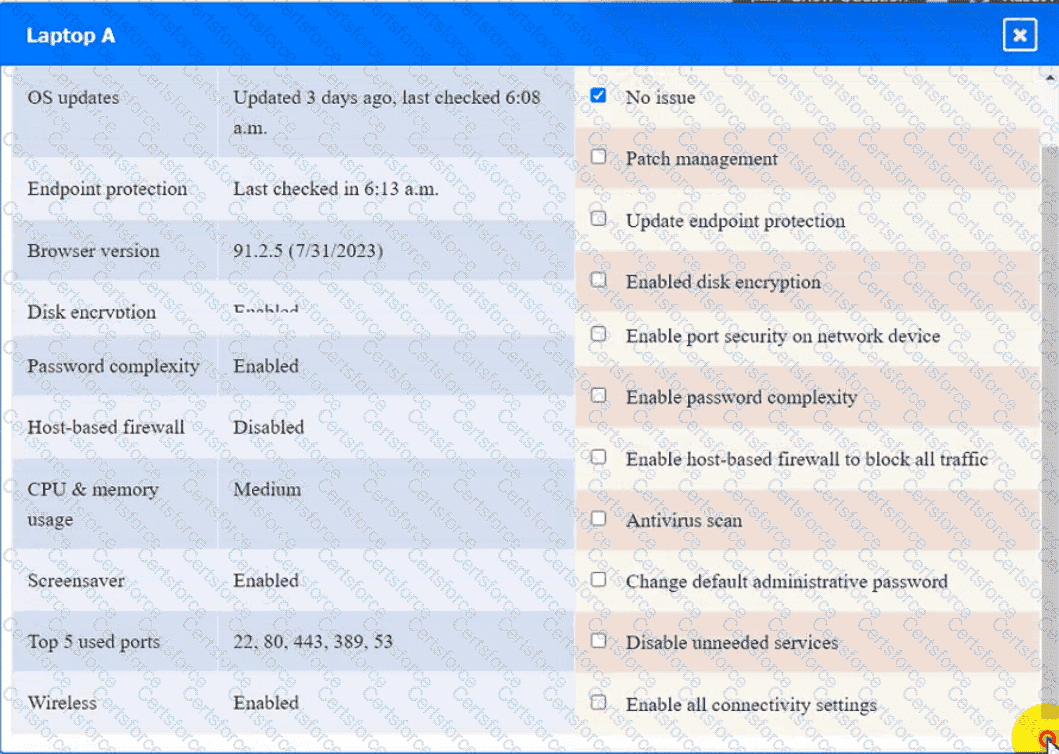
Click on the various workstations and network devices to review the posture assessment results. Remediate any possible issues or indicate that no issue is found.
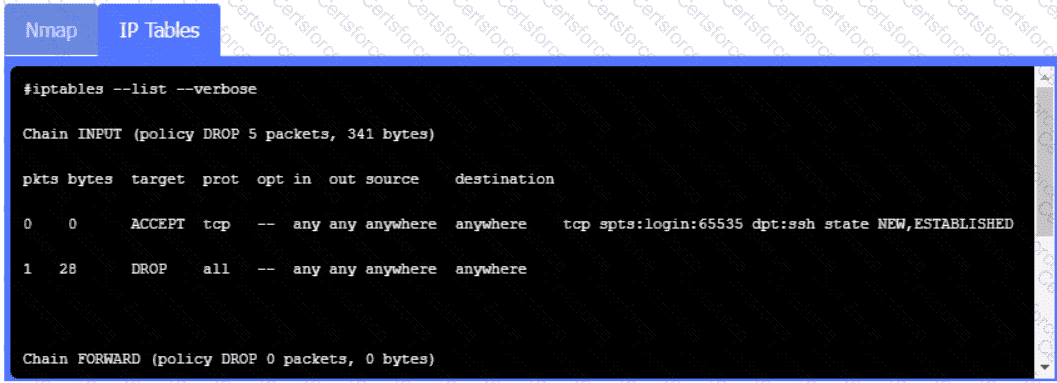
Click on Server A to review output data. Select commands in the appropriate tab to remediate connectivity problems to the pOSTGREsql DATABASE VIA ssh
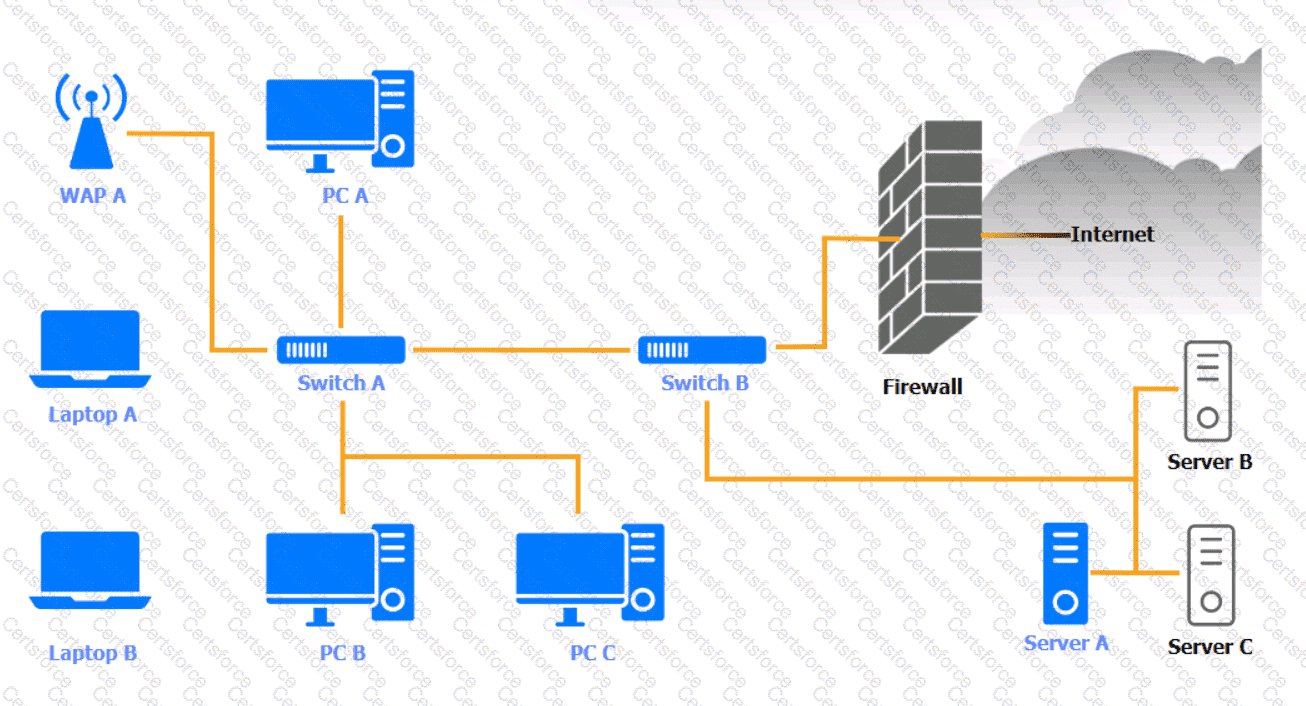
WAP A
PC A
Laptop A
Switch A
Switch B:
Laptop B
PC B
PC C
Server A
A third-party organization has implemented a system that allows it to analyze customers' data and deliver analysis results without being able to see the raw data. Which of the following is the organization implementing?