An network is designed to use OSPF to reach eBGP peers. Which condition should be avoided in the design to potentially prevent the eBGP peers do not flap continuously in case of link failure?
You are designing dual-homed active/active ISP connections from an enterprise customer for internet services, and you have recommended BGP between the customer and ISP. When three security mechanisms do you enable to secure the connection? (Choose three)
In a design around fast convergence in case of a link failure, what is the justification for using a point-to-point OSPF network type on the Ethernet links between leaf-and-spine switches on a data center fabric?
Which two statements about VXLAN are true? (Choose two)
You are designing a traffic monitoring and analysis system for a customer. Which traffic monitoring technique would you recommend to place the amount of burden on the network infrastructure?
Which two design aspects should a metro service provider consider when planning to deploy REP for his backbone? (Choose two.)
A Mobile Service Provider would like to design and deploy an Ethernet service which has similar physical link failover/failback characteristics on the active/backup links as the APS/MSP SONET properties. Which Layer 2 service addresses should be considered to address this design feature?
Which three network management requirements are common practices in network design? (Choose three)
Refer to the exhibit.
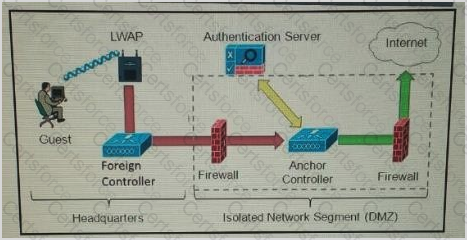
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
Which four resources does Cisco Cloud Center provision in an ACL environment? (Choose four)