A network administrator is modifying an outgoing mail policy to enable domain protection for the organization. A DNS entry is created that has the public key.
Which two headers will be used as matching criteria in the outgoing mail policy? (Choose two.)
What is the default behavior of any listener for TLS communication?
What is the order of virus scanning when multilayer antivirus scanning is configured?
A Cisco Secure Email Gateway appliance is processing many messages that are sent to invalid recipients verification. Which two steps are required to accomplish this task? (Choose two.)
An administrator identifies that, over the past week, the Cisco ESA is receiving many emails from certain senders and domains which are being consistently quarantined. The administrator wants to ensure that these senders and domain are unable to send anymore emails.
Which feature on Cisco ESA should be used to achieve this?
Refer to the exhibit.
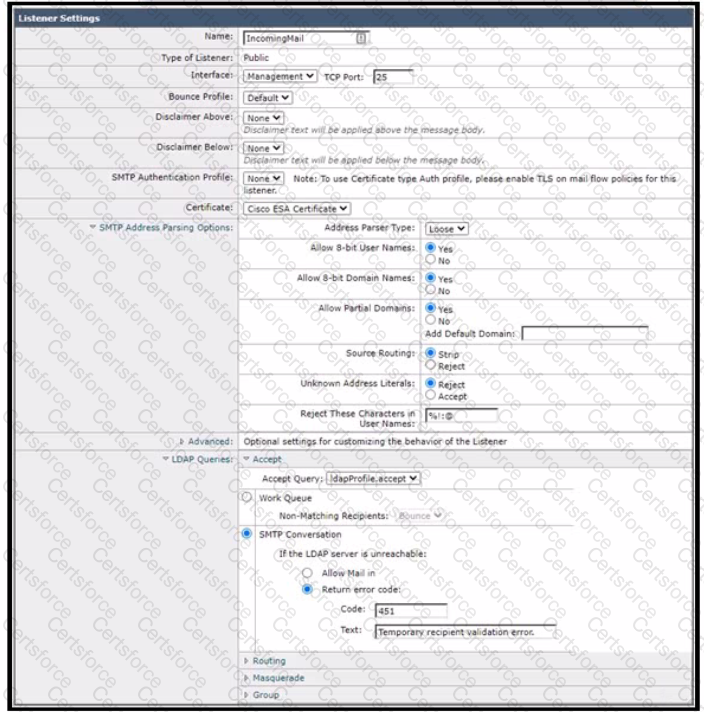
Which additional configuration action must be taken to protect against Directory Harvest Attacks?
When the Cisco ESA is configured to perform antivirus scanning, what is the default timeout value?
Which attack is mitigated by using Bounce Verification?
Which two components must be configured to perform DLP scanning? (Choose two.)
An administrator notices that incoming emails with certain attachments do not get delivered to all recipients when the emails have multiple recipients in different domains like cisco.com and test.com. The same emails when sent only to recipients in cisco.com are delivered properly. How must the Cisco Secure Email Gateway be configured to avoid this behavior?