An enterprise has two WLANs configured on WLC. It is reported that when converting APs to FlexConnect mode, WLAN A works but WLAN B does not. When converting APs to local mode, WLAN B works, but WLAN A does not. Which action is needed to complete this configuration?
Which condition introduce security risk to a BYOD policy?
A company is concerned about unauthorized APs on their wired and wireless networks. The company implements a Cisco Catalyst Center (formerly DNA Center) solution. Which feature must be enabled?
A shopping center uses AireOS controllers with Cisco Wave 2 APs. A separate WLAN named Guest-012345678-WLAN is used for guest wireless clients. Management needs location analytics to determine popular areas. CMX must track only associated clients. What must be selected on the CMX server settings?
Refer to the exhibit.
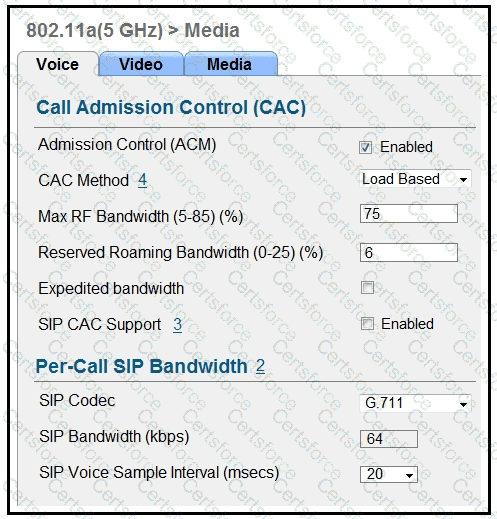
Which two items must be supported on the VoWLAN phones to take full advantage of this WLAN configuration? (Choose two.)
A Cisco WLC has been added to the network and Cisco ISE as a network device, but authentication is failing. Which configuration within the network device configuration should be verified?
An enterprise has recently deployed a voice and video solution available to all employees using AireOS controllers. The employees must use this service over their laptops, but users report poor service when connected to the wireless network. The programs that consume bandwidth must be identified and restricted. Which configuration on the WLAN aids in recognizing the traffic?
An engineer configures a Cisco Aironet 600 Series OfficeExtend AP for a user who works remotely. What is configured on the Cisco WLC to allow the user to print a printer on his home network?
An engineer must enable LSS for the AppleTV mDNS service only when ORIGIN is set to Wired. Which action meets this requirement?
You enter the command or a Cisco Catalyst 3850 Series Switch that runs Cisco ISO XE. What does the command do?