An “unknown error code” is appearing on an ESXi host during authentication. An engineer checks the authentication logs but is unable to identify the issue. Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?
An engineer is analyzing a ticket for an unexpected server shutdown and discovers that the web-server ran out of useable memory and crashed.
Which data is needed for further investigation?
Refer to the exhibit.
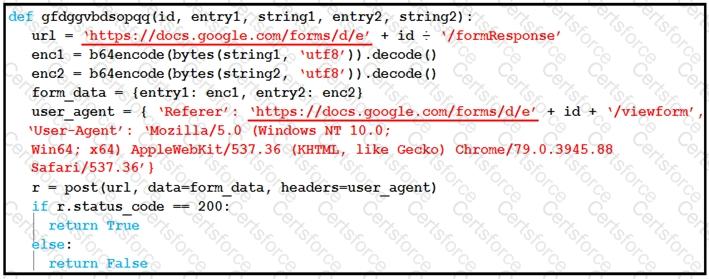
Which type of code is being used?
Refer to the exhibit.
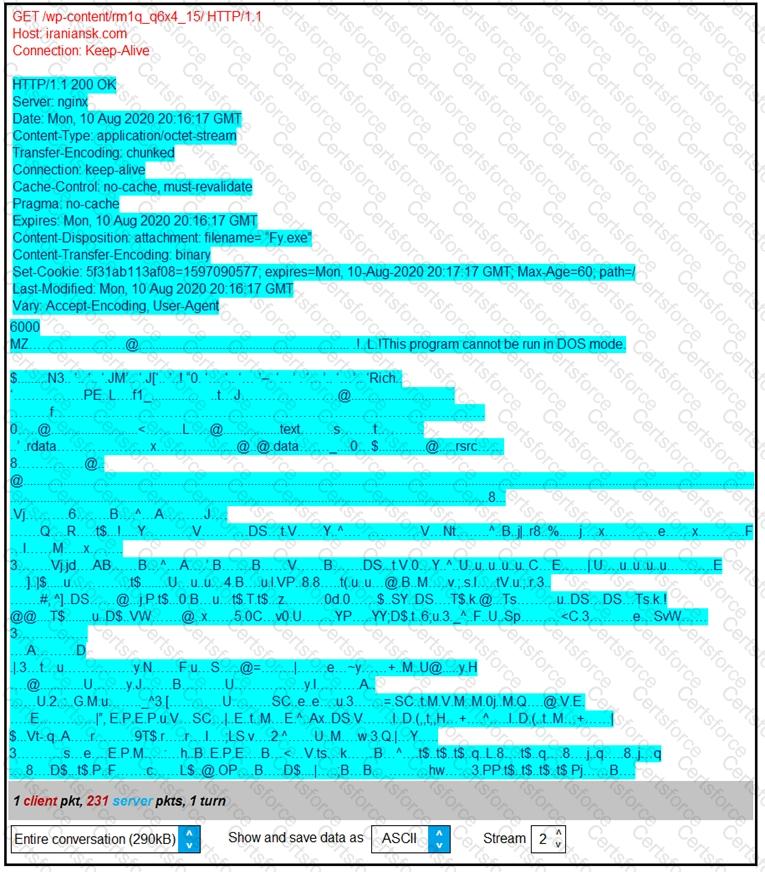
According to the Wireshark output, what are two indicators of compromise for detecting an Emotet malware download? (Choose two.)

Refer to the exhibit. A security analyst notices that a web application running on NGINX is generating an unusual number of log messages. The application is operational and reachable. What is the cause of this activity?
Refer to the exhibit.
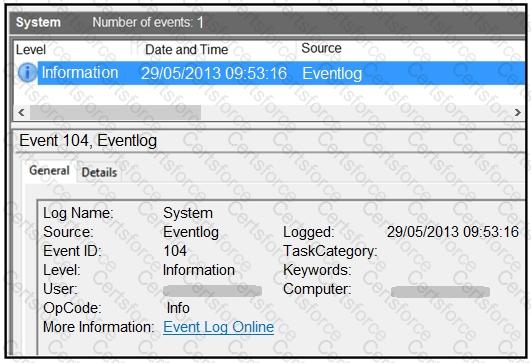
An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?
An organization experienced a ransomware attack that resulted in the successful infection of their workstations within their network. As part of the incident response process, the organization's cybersecurity team must prepare a comprehensive root cause analysis report. This report aims to identify the primary factor or factors responsible for the successful ransomware attack and to formulate effective strategies to prevent similar incidents in the future. In this context, what should the cybersecurity engineer emphasize in the root cause analysis report to demonstrate the underlying cause of the incident?
Refer to the exhibit.
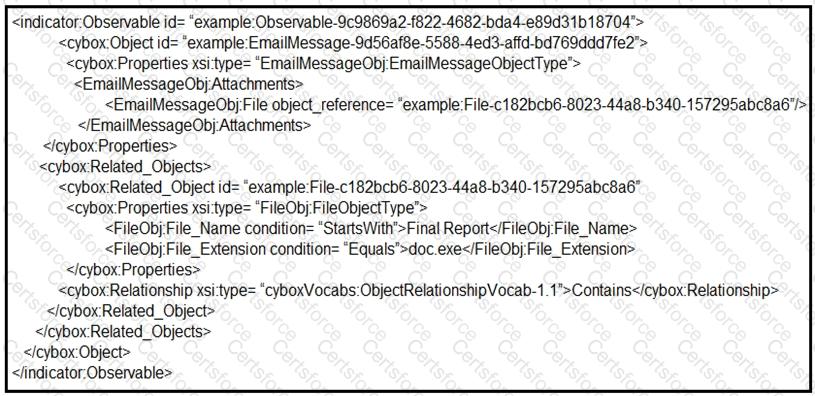
Which determination should be made by a security analyst?
Refer to the exhibit.
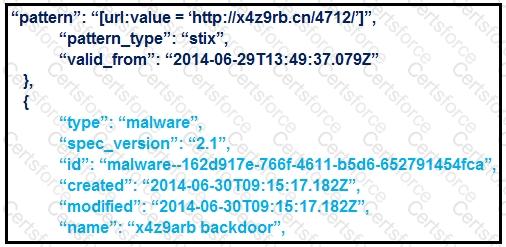
What is the IOC threat and URL in this STIX JSON snippet?
Refer to the exhibit.
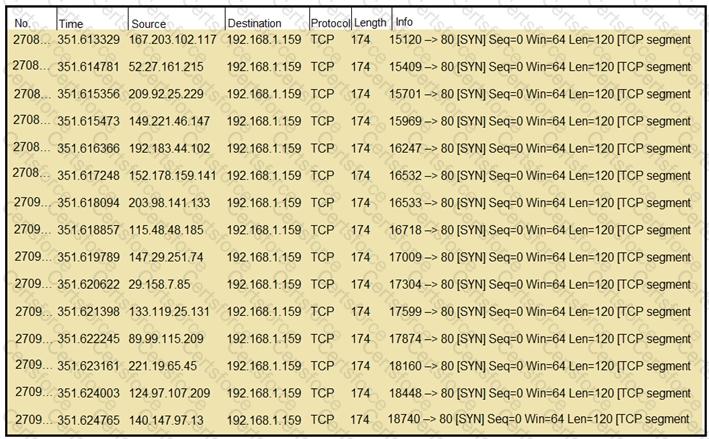
What should an engineer determine from this Wireshark capture of suspicious network traffic?